Application Security , Fraud Management & Cybercrime , Governance & Risk Management
Zero-Day Attacks Exploit MSHTML Flaw in Microsoft Windows
Workarounds Detailed to Block Active Attack; Microsoft Has Yet to Release Patches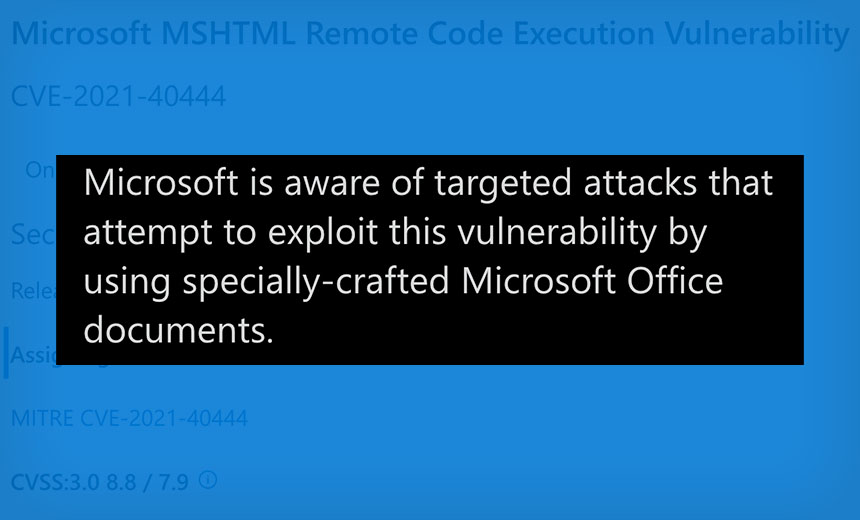
Attackers are actively exploiting a flaw in Microsoft Windows for which no patch is yet available.
See Also: Revealing the Dark Web: How to Leverage Technologies to Alert and Block Dark Web Access
Microsoft says in a Tuesday security alert that the remote execution vulnerability exists in MSHTML, and that it "is aware of targeted attacks that attempt to exploit this vulnerability by using specially crafted Microsoft Office documents."
Microsoft says its security research team is still probing the flaw, and no full security fixes or patches are yet available, although it's weighing issuing a regular security update as part of its monthly patch-release cycle, or releasing an emergency fix. In the meantime, however, its security alert details workarounds and mitigations that it recommends security teams immediately put in place.
The newly discovered flaw, designated CVE-2021-40444, exists in MSHTML, aka Trident, which is the HTML engine that's been built into Windows since Internet Explorer debuted more than 20 years ago, and which has allowed Windows to read and display HTML files. While Microsoft has been progressively retiring IE in favor of its newer Edge browser, the MSHTML component continues to be "also used by Microsoft Office," Broadcom's Symantec notes in its own security alert about the flaw.
Attackers Wield Malicious ActiveX Controls
Due to the vulnerability, "an attacker could craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine," after which "the attacker would then have to convince the user to open the malicious document," Microsoft says. Unfortunately, as the continuing prevalence of malicious macro attacks demonstrates, this remains a viable attack tactic.
"Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights," Microsoft adds. In other words, the greater a user's access rights, the greater the risk posed by a successful attack, since it gives attackers the ability to remotely execute any code on a victim's system.
Microsoft credits multiple researchers for discovering the flaw: Rick Cole of the Microsoft Threat Intelligence Center; Bryce Abdo, Genwei Jiang and Dhanesh Kizhakkinan of Mandiant; and Haifei Li of EXPMON, who notes he alerted Microsoft to the problem on Sunday.
Code for exploiting the flaw has not yet become public.
But Li tweets that the vulnerability involves "logical flaws" in how MSHTML was built, rather than coding errors that have given rise to attacks based on "memory corruption."
We have reproduced the attack on the latest Office 2019 / Office 365 on Windows 10 (typical user environment), for all affected versions please read the Microsoft Security Advisory. The exploit uses logical flaws so the exploitation is perfectly reliable (& dangerous).— EXPMON (@EXPMON_) September 7, 2021
He adds: "Since there's no patch, we strongly recommend that Office users be extremely cautious about Office files" and avoid opening any such files from unknown or not fully trusted sources.
These in-the-wild attacks are a reminder that fresh zero-day exploits remain a fact of life, says Andrew Thompson, a threat analyst at Mandiant.
"Now is a great time to remind defenders that they need to focus on comprehensive post-exploitation mitigation and detection," he tweets. "Now is also a great time for security testers and researchers to not be the first to release an exploit, especially pre-patch. It won't help defenders."
Flaw Poses Serious Risk
Security experts say this flaw appears destined to pose a serious threat for the foreseeable future.
Btw, although Microsoft has stopped using the term zero day to describe them in their own products, this one (CVE-2021-40444) is specifically a zero day.
It's under active attack, there's no patch, the vendor didn't know etc.— Kevin Beaumont (@GossiTheDog) September 8, 2021
"This one is legit and is going to be worse than the Equation Editor CVEs (which make up almost all endpoint exploitation still), so strap in," tweets Kevin Beaumont, the head of the security operations center for U.K. fashion retailer Arcadia Group, and a past senior threat intelligence analyst at Microsoft.
Beaumont is referencing an Equation Editor stack buffer overflow flaw first disclosed by Microsoft in 2017, which existed in earlier versions of Office and could be exploited to "allow a remote, unauthenticated attacker to execute arbitrary code on a vulnerable system," according to Microsoft's security alert at the time.
Unfortunately, the flaw, CVE-2017-11882, continues to be widely exploited by criminals, and also ranks as one of the top 10 flaws being exploited by nation-state attackers tied to China, Russia, North Korea and Iran, the FBI and Department of Homeland Security recently warned.
"Interestingly, the vulnerable component was 17 years old - compiled in 2000 - at the time of exploitation and unchanged since its removal in 2018," researchers at IBM X-Force have noted. Microsoft removed the binary from Windows after losing the source code but still attempting to patch it. After an attacker found a fresh way to exploit the flaw, Microsoft removed the code altogether.
Mitigations and Workarounds
With no patch yet being available, Microsoft says one workaround is to disable the installation of all new ActiveX controls in Windows. Some security experts, however, have questioned how feasible this might be.
In the meantime, many endpoint security products, including Microsoft's offerings, are being updated to spot the attack.
"Microsoft Defender Antivirus and Microsoft Defender for Endpoint both provide detection and protections for the known vulnerability," according to Microsoft's security alert. But while nonenterprise customers who have automatic updates enabled will receive updated antivirus signatures to block the attack, many enterprise administrators will have to take further steps.
So if you're Microsoft EDR but not AV (actually a majority of customers, btw) nothing is blocked, unless you set EDR to block mode.— Kevin Beaumont (@GossiTheDog) September 7, 2021
Beaumont says the majority of enterprise customers aren't running Defender Antivirus, but rather Microsoft's endpoint detection and response product. Microsoft says that to stop this attack, organizations using its Defender for Endpoint product must be set it to block mode.