Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Fraud Risk Management
White House 'Stands Down' SolarWinds, Exchange Response Groups
Unified Coordination Groups Were Created to Respond to Cybersecurity Incidents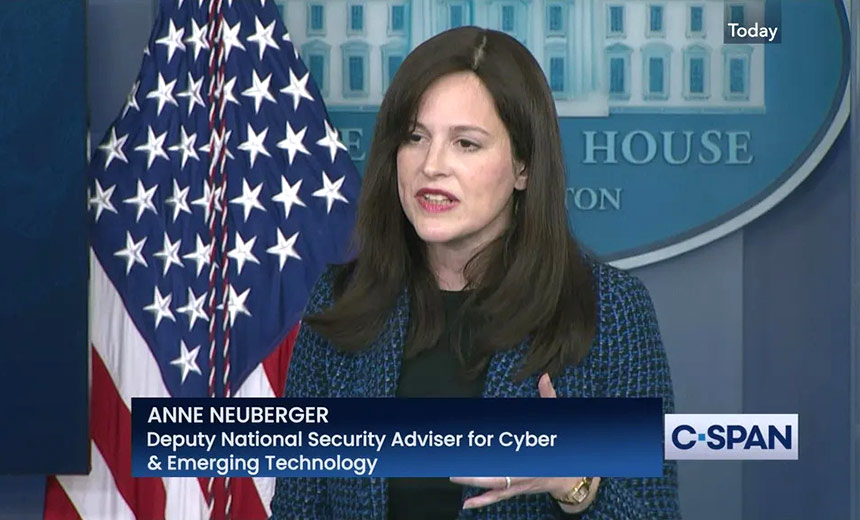
The White House announced Monday that it is "standing down" two Unified Coordination Groups that were created to coordinate the federal response to the SolarWinds supply chain attack and attacks on vulnerable on-premises Microsoft Exchange email servers.
See Also: Enabling Government for Modernized IT
Anne Neuberger, the deputy national security adviser for cyber and emerging technology who's overseeing the Biden administration's response to the attacks, says the two groups' work can be scaled back because of increases in patching and other mitigation by federal agencies and companies.
"Due to the vastly increased patching and reduction in victims, we are standing down the current [Unified Coordination Group] surge efforts and will be handling further responses through standard incident management procedures," Neuberger says.
Both of the groups included representatives of the FBI, the U.S. Cybersecurity and Infrastructure Security Agency and the Office of the Director of National Intelligence. The National Security Agency also provided input and technical assistance.
The Unified Coordination Group that responded to the SolarWinds supply chain attack was originally established under the Trump administration after security firm FireEye discovered the incident in December 2020. The other response group was set up in March after the attacks against the vulnerable, on-premises Exchange servers came to light (see: White House Establishes Group to Investigate Exchange Attacks).
Sanctions Announced
The announcement about the groups comes after the Biden administration announced sanctions Thursday targeting Russia and several organizations and individuals tied to the SolarWinds attack and election misinformation campaigns. The White House said Russia's Foreign Intelligence Service, or SVR, carried out the attack on SolarWind's Orion network monitoring platform that led to follow-on attacks on nine federal agencies and about 100 companies (see: US Sanctions Russia Over SolarWinds Attack, Election Meddling).
The Biden administration also announced it would expel 10 Russian diplomats from the U.S. On Friday, Russia, which has denied involvement in the SolarWinds attack, announced it would demand that 10 American diplomats leave the country (see: US Pulls Back Curtain on Russian Cyber Operations).
Meanwhile, the FBI obtained a court order that allowed the bureau to remove malware from on-premises Exchange servers at organizations affected by zero-day exploits (see: FBI Removing Web Shells From Infected Exchange Servers).
White House Claims Progress
In announcing plans to wind down the two Unified Coordination Groups, the Biden administration noted that it would take the "lessons learned" from these two cyber incidents and apply them to other risk mitigation efforts.
For instance, the White House pointed to the partnership it developed with Microsoft to create a one-click mitigation tool for customers who were running either current or no longer supported on-premises versions of Exchange server to reduce the risk until they could fully implement patches.
Plus, CISA developed a methodology to help better track the patching and fixing of vulnerable Exchange servers, according to the White House.
The Biden administration noted that the Unified Coordination Group created to respond to the SolarWinds incident helped the FBI and U.S. Justice Department identify the 100 companies and nine government agencies that were targeted by the SVR, which "enabled focused victim engagement and improved understanding of what the perpetrators targeted from the larger set of exposed entities."
Neuberger noted: "The SolarWinds and Microsoft Exchange [Unified Coordination Groups] highlight the priority and focus the administration places on cybersecurity and at improving incident response for both the U.S. government and the private sector."
Unified Coordination Groups are typically created through the National Incident Management System, a standardized approach to incident management created by the Department of Homeland Security and designed to coordinate the response by federal agencies, says Mike Hamilton, a former vice chair of the Department of Homeland Security's State, Local, Tribal, and Territorial Government Coordinating Council.
"The Unified Coordination Group stands up when the response to an incident requires a multiple agency response as well as clearly defined incident command," says Hamilton, now the CISO of CI Security. "As the incident moves from response to recovery, the UCG is no longer needed. This is not the end of incident management - just a change in the command structure."




















