Next-Generation Technologies & Secure Development , Threat Hunting , Threat Modeling
Threat Hunting, From a Model-Driven Cybersecurity Approach

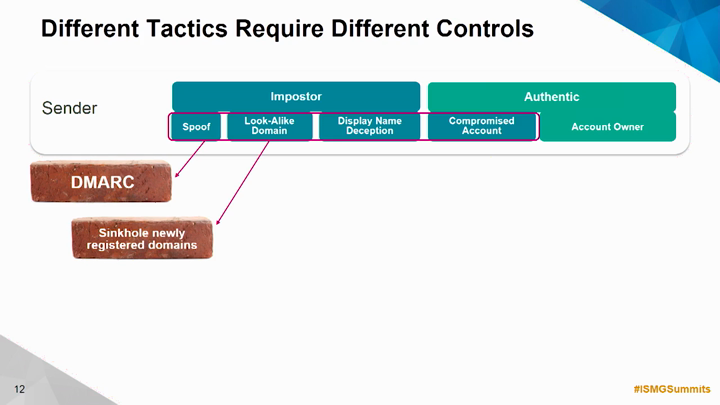
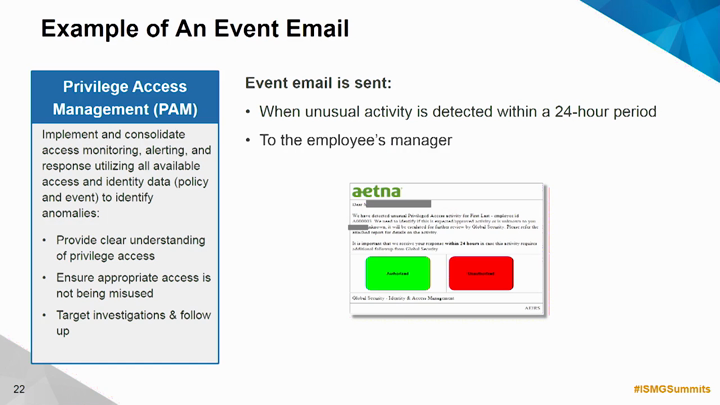
Four years ago, Aetna Global Security hired a chief data scientist for security - a former NSA data scientist who did an outstanding job building over 100 models and a big data infrastructure dedicated to security. The purpose of hiring this data scientist: to take multiple sources of log files from newly deployed controls and determine how best to allocate scarce resources for threat hunting. Soon, while the project was underway, six other implementations of machine learning-driven point solutions catapulted Aetna Global Security into a model-driven security deployment using data analytics. In this session, Jim Routh, CISO at Aetna, discusses what his organization learned from this experience, the implications for security talent management and information sharing going forward, as well as the company's planned move away from passwords to continuous behavioral authentication.
See Also: 2023 Exabeam State of Threat Detection, Investigation, and Response Report