Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response
Wawa's Stolen Payment Cards Are Now for Sale
Fraud Marketplace Joker's Stash Says it Has 30 Million Cards
A long-running marketplace for selling stolen payment card data is advertising a large new batch linked to the breach at Wawa convenience stores late last year.
See Also: Where to Invest Next: People, Processes and Technology for Maturing Cyber Defenses
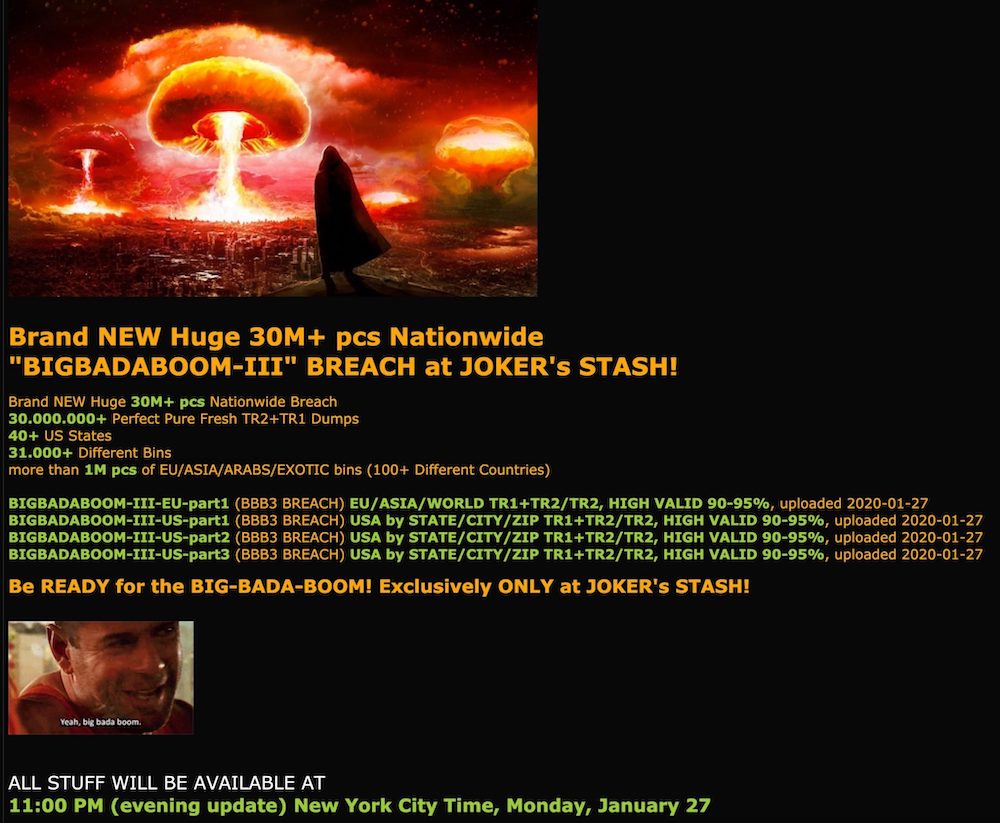
The “Joker’s Stash” marketplace started promoting on Monday a batch of data that likely comes from WaWa’s beach, according to Gemini Advisory, a New York-based consultancy that specializes in anti-fraud services. Joker’s Stash calls the data dump “BIGBADABOOM-III.”
In December, Wawa revealed that point-of-sale devices and fuel dispensers across its 850 stores, which are primarily on the East Coast of the U.S., were infected with malware. The malware collected credit and debit card numbers, expiration dates and cardholder names.
The exposure lasted from March 4, 2019, through Dec. 12, 2019 (see: Wawa Stores: POS Malware Attack Undetected for 8 Months).
Large Breach
Joker’s Stash claims its latest dump contains as many as 30 million payment cards from 40 states. About 1 million of the cards are from other countries, according to its advertisement. The cards contain more than 31,000 banking identification numbers, or BINs, which identifying the issuing bank.
“As far as payment cards go, this is one of the largest breaches that we’ve seen,” says Christopher J.S. Thomas, an intelligence product analyst with Gemini.
By comparison, the 2013 Target breach exposed 40 million payment cards. Other large breaches include Home Depot, which in 2014 saw 56 million payment cards stolen, and TJX in 2007, which had 46.5 million card details stolen.
Joker’s Stash tends to stagger what it makes available for sale. Thomas says there are only about 100,000 cards for sale now. The median price for a set of card details is $17, with prices for cards from users outside the U.S. as much as $210, Gemini writes.
The data may be of limited use to fraudsters. Wawa said at the time of the breach that the CVV – which is a three digit security code number on the reverse of a card – was not leaked. That would make it harder for cybercriminals to, for example, make online card-not-present purchases, which usually require that code. However, it would still be possible to clone the card, or copy the stolen data onto a dummy card, says Sam Rubin, vice president of The Crypsis Group.
The rollout of EMV cards, which have embedded microchips that provide for more secure transactions, are intended to stop the use of cloned cards. But whether a cloned card is blocked from completing a transaction also depends on how a card is processed during a transaction.
Rubin says the chance of fraud for affected Wawa customers has certainly increased, but “it's important to keep in mind that the chances of fraud for any single card is relatively low.”
Wawa also says PINs were not breached nor other personal information. Also, banks and card issuers will be on high alert for anomalies that might indicate a card within the breach is being fraudulently used.
The Wawa cards “are certainly not going to be the most high demand and the most desirable information out there, although it’s often possible to make fraudulent gains off of little information,” Thomas says.
Joker’s Stash says it will also post geolocation data about cardholders, which could include a cardholder’s city, state of residence and ZIP code. That could allow fraudsters to seek out those people and trick them into divulging the CVV, for example. So far, however, only state information has been listed, Gemini says.
Joker’s Stash also tends to use data acquired from extra large breaches to generate attention more than sales, Thomas says. The site has recently been trying to defend its reputation, citing media stories and taking credit for well-publicized breaches, he says.
“It’s certainly like shooting a flare to the sky so everyone knows about the breach, everyone knows that it’s been posted,” Thomas says. “So in terms of staying under the radar, this is certainly not the type of strategy you would enact for discretion, and that would make it more difficult to cash out the cards.”
Wawa Alert
Wawa issued a statement on Tuesday, saying it's confident that the malware was contained by Dec. 12 and that customers have not been at risk since then.
“We have alerted our payment card processor, payment card brands, and card issuers to heighten fraud monitoring activities to help further protect any customer information,” the company says. “We continue to work closely with federal law enforcement in connection with their ongoing investigation to determine the scope of the disclosure of Wawa-specific customer payment card data.
Wawa is offering one year of prepaid fraud and credit monitoring via Experian, which can be registered for here with this activation code: 4H2H3T9H6.
“We continue to encourage our customers to remain vigilant in reviewing charges on their payment card statements and to promptly report any unauthorized use to the bank or financial institution that issued their payment card by calling the number on the back of the card,” Wawa says.



















