Endpoint Security , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
WannaCry Outbreak: Microsoft Issues Emergency XP Patch
Researcher Accidentally Blocks New Infections, But Warns Fix is Temporary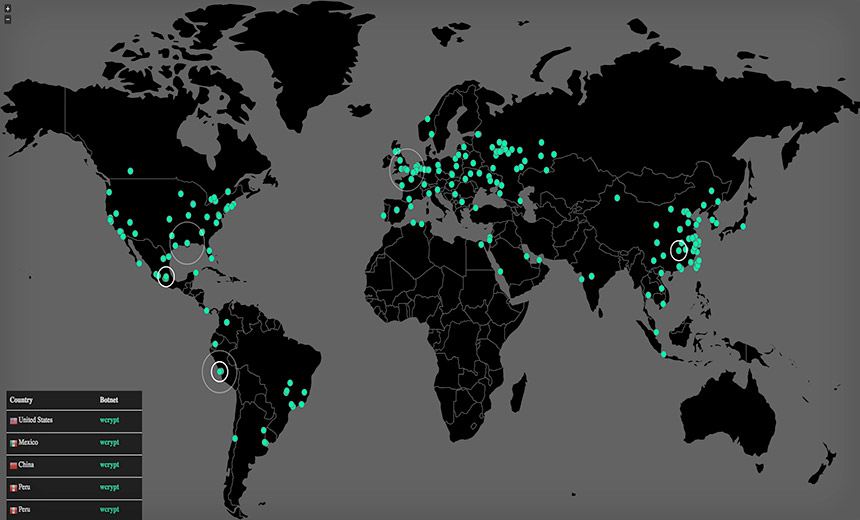
Microsoft has issued emergency security updates for multiple operating systems that it no longer supports to help organizations protect themselves against a still-unfolding global cyberattack. The attack involves WannaCry crypto-locking ransomware, also known by various another names, including WCry and WanaCrypt0r.
See Also: Federal Agencies Tech Brief: Security Investigation, Detection and Rapid Response
The ransomware is being spread via a worm that attempts to leverage two leaked exploits that have been tied to the National Security Agency, including one for an SMB flaw in all versions of Microsoft Windows XP to Server 2008 R2 (see WannaCry Ransomware Outbreak Spreads Worldwide).
Separately, a malware researcher appears to have found a "kill switch" for the strain of ransomware that has infected more than 200,000 endpoints in over 150 countries. But the researcher warns that the respite is almost certainly temporary, since attackers could easily retool their code to enable their ransomware to once again forcibly encrypt infected PCs and hold them to ransom.
Related attacks unfolded May 12 and quickly compromised numerous organizations, ranging from Spanish telco Telefonica and numerous National Health Service trusts and doctor offices across England and Scotland, to Russia's interior ministry and the national rail network in Germany.
#WannaCry ransomware also hits German Train Station. pic.twitter.com/S5hIrsDe3G
— Moften (@hack4lifemx) May 12, 2017
The ransomware is being spread by a worm that targets a Windows SMB flaw. The flaw was patched by Microsoft in March via the MS17-010 security update, apparently after it was tipped off by the NSA. In April, the Shadow Brokers - a shadowy group believed to have ties to the Russian government - leaked an exploit from the "Equation Group" - believed to be the National Security Agency's in-house hacking team, known as Tailored Access Operations - called EternalBlue that targeted the SMB flaw to then install a backdoor called DoublePulsar (see DoublePulsar Pwnage: Attackers Tap Equation Group Exploit).
Microsoft acknowledges in a blog post that it knows that some organizations and individuals still run versions of Windows that it no longer supports via issuing new security updates or other patches. "That means those customers will not have received the above mentioned security update released in March," according to a blog post from Microsoft's Trustworthy Computing team. "Given the potential impact to customers and their businesses, we made the decision to make the security update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download."
In addition, Microsoft said it added related signatures to its free Windows Defender anti-virus software. "Customers running anti-malware software from any number of security companies can confirm with their provider that they are protected," the company says.
Target: DoublePulsar, EternalBlue
Security firm Cisco Talos, in an analysis of the WannaCry attacks to date published May 12, says that the attack code is designed to look for the DoublePulsar backdoor, and if that's not found, to then try the EternalBlue exploit against an endpoint.
"WannaCry does not appear to be only leveraging the EternalBlue modules associated with this attack framework; it is simply scanning accessible servers for the presence of the DoublePulsar backdoor," Cisco Talos security researchers write. "In cases where it identifies a host that has been implanted with this backdoor, it simply leverages the existing backdoor functionality available and uses it to infect the system with WannaCry."
Otherwise, attackers have programmed their attack code to target the SMB exploit. "In cases where the system has not been previously compromised and implanted with DoublePulsar, the malware will use EternalBlue for the initial exploitation of the SMB vulnerability," they write. "This is the cause of the worm-like activity that has been widely observed across the internet."
The attacks seen to date have demanded about $300 in bitcoins from victims to share an unlock code.
Bitcoin surveillance company Elliptic says three different bitcoin wallet addresses have been hardcoded into the ransomware by attackers. But it's not clear if any ransomware victims have in fact received a working decryption key in response.
As of May 13, roughly 100 payments totaling 15 bitcoins - worth about $27,000 - had been sent to those bitcoin wallets. (Update: As of 9am GMT on May 15, the total had risen to 167 payments, totaling 25 bitcoins worth $44,000.)
But Elliptic has warned that the number of ransom payments may spike on May 15, three days after the initial infection. That's because the ransomware lock screen informs victims they have three days to pay, at which point the ransom demand doubles. After seven days, the malware warns, "you won't be able to recover your files forever."
'Accident' Disables Some New Attacks
A British security expert who goes by "Malware Tech" - and who declined to be named in press reports - told the BBC that he found a reference in the malware to a domain - www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com - which wasn't registered. So he registered it.
Only then, he found that the malware had been using the nonsense website name as a check: If the ransomware pinged that domain and received back a "domain not found" error message, the malware assumed that it was running on a legitimate endpoint. But if it received an "HTTP 200 OK answer," the malware assumed it was running in a virtual environment designed for studying malware, and the ransomware would then disable itself in an attempt to foil researchers.
MalwareTech says he has now redirected the domain name to a sinkhole that will redirect infected endpoints to instructions for how they can remove the attack code and patch their systems.
IP addresses from our sinkhole have been sent to FBI and ShadowServer so affected organizations should get a notification soon. patch ASAP.
— MalwareTech (@MalwareTechBlog) May 13, 2017
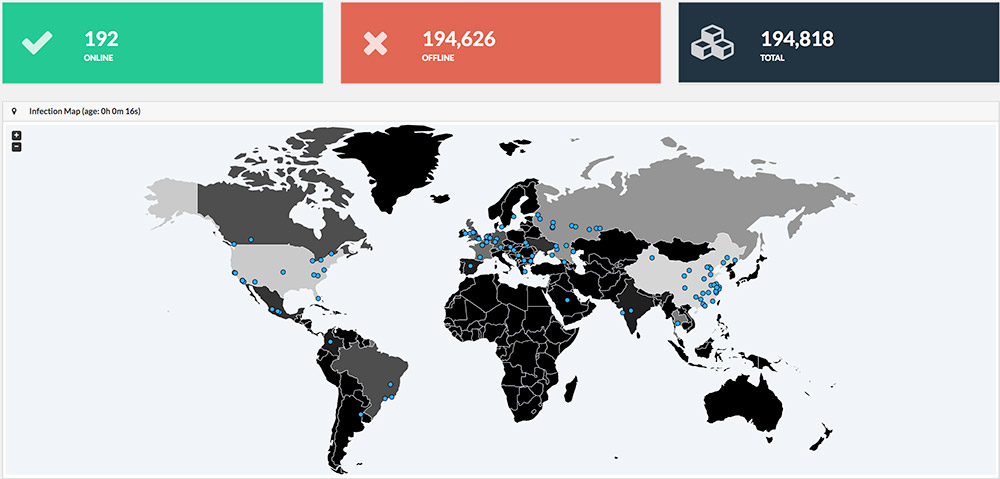
"This sinkholed domain has prevented further infections occurring and has already resulted in preventing over 100,000 potential infections," the U.K. National Cyber Security Center, part of intelligence agency GCHQ, says in a blog post, noting that it's been working with MalwareTech. "However, this action will not remediate infections that have already occurred. Currently, the best mitigation available to prevent infection by Wannacry is the guidance presented in the following blog by MalwareTech and the latest ransomware guidance from the NCSC."
As of May 13, up to 200,000 endpoints appeared to have been infected with the ransomware, according to MalwareTech. Any endpoint that was infected after MalwareTech sinkholed the domain referenced by the ransomware, however, will not be crypto-locked, at least with the current version of Wcrypt.
Experts: No Surprise
Security experts say they are not surprised that this sort of attack unfolded, and they have been urging all organizations to install the MS17-010 security update as quickly as possible (see Responding to WannaCry Ransomware Outbreak).
"I think it was not if this was going to happen, it was really when," Professor Bill Buchanan at the Edinburgh Napier University School of Computing tells Sky News. "It's been well-known in the security community that this was a major, critical vulnerability that was announced on the 14th of March. So, industry has had over a month to be able to cope with this, and it's obvious that many systems haven't been patched ... [and] that many computers within the public sector are still running XP systems."
Cybersecurity expert Chris Pierson, CSO and general counsel for payment technology firm Viewpost, tells Information Security Media Group that it's also no surprise that mass attacks have affected the healthcare sector.
"Healthcare computers are usually always on, less frequently patched due to their role in the healthcare process, and oftentimes hospitals and clinics are lagging behind on cybersecurity controls," he says.
Respite Likely Brief; Mitigate Now
Security experts say that whoever is behind these attacks could easily learn from the mitigations that have been used against the code.
"It's very important that people patch their systems now because we did stop this one, but there will be another one coming and it will not be stoppable by us, " MalwareTech tells the BBC. "There's a lot of money in this, there's no reason for them to stop. There's not really much effort for them to change the code and then start over - so there's a good chance they are going to do it, maybe not this weekend but quite likely on Monday morning."
Alan Woodward, a professor of computer science at the University of Surrey who advises the EU's law enforcement intelligence agency, Europol, on cybersecurity matters, offered the following advice for all organizations: "Apply MS17-010. Isolate NT4, 2000, XP. Block ports 139, 445 and 3389."
For any organization that cannot apply MS17-010 or block those ports for some reason, "disable SMBv1," the NCSC recommends, pointing to Microsoft guidance.
Some Microsoft customers have already still been paying for pricey "extended support" for Windows Server 2003 and Windows XP, which debuted more than 15 years ago. But Microsoft has been lauded by many security experts for stepping forward to issue emergency patches to the public.
"By releasing an out-of-bounds patch for unsupported operating systems such as Windows XP and Server 2003, people now are able to patch rather than having to attempt upgrades to newer system in order to be secured against this worm," MalwareTech says in a blog post.
Lynne Owens, head of the U.K. National Crime Agency, tells the BBC that no culprits or suspects behind the WannaCry outbreak have been identified, but the agency has been deploying "all covert and overt means available to us" to try to track them down.






















