Application Security , Containerization & Sandboxing , Cybercrime
Vulnerability Researchers Hit by North Korean Hackers
Google Warns Social Engineering Attacks Have Been Backdooring Researchers' Systems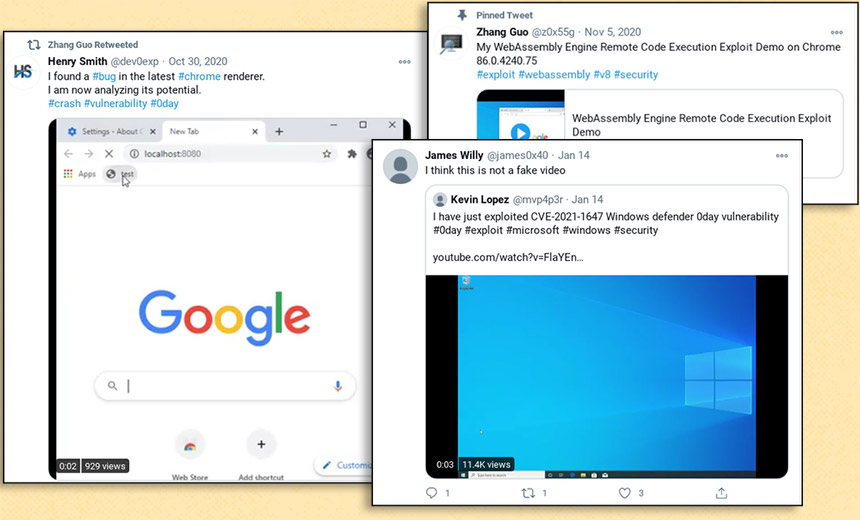
North Korean hackers have been "targeting security researchers working on vulnerability research and development at different companies and organizations" to trick them into installing backdoored software, warns Google's Threat Analysis Group.
The group's Monday blog post describes what it says is a monthslong attack campaign that has already notched up multiple victims.
See Also: The State of Organizations' Security Posture as of Q1 2018
The campaign traces to "a government-backed entity based in North Korea," which has used a variety of techniques to trick researchers, Google warns. "We hope this post will remind those in the security research community that they are targets to government-backed attackers and should remain vigilant when engaging with individuals they have not previously interacted with."
Google says the ploy typically begins with attackers, posing as security researchers, asking a fellow bug hunter if they want to collaborate on vulnerability research, and then sharing a project file for Microsoft's Visual Studio integrated development environment tool, which includes an exploit for a known vulnerability hidden in the software.
"Within the Visual Studio Project would be source code for exploiting the vulnerability, as well as an additional DLL that would be executed through Visual Studio build events," it says. "The DLL is custom malware that would immediately begin communicating with actor-controlled C2 domains."
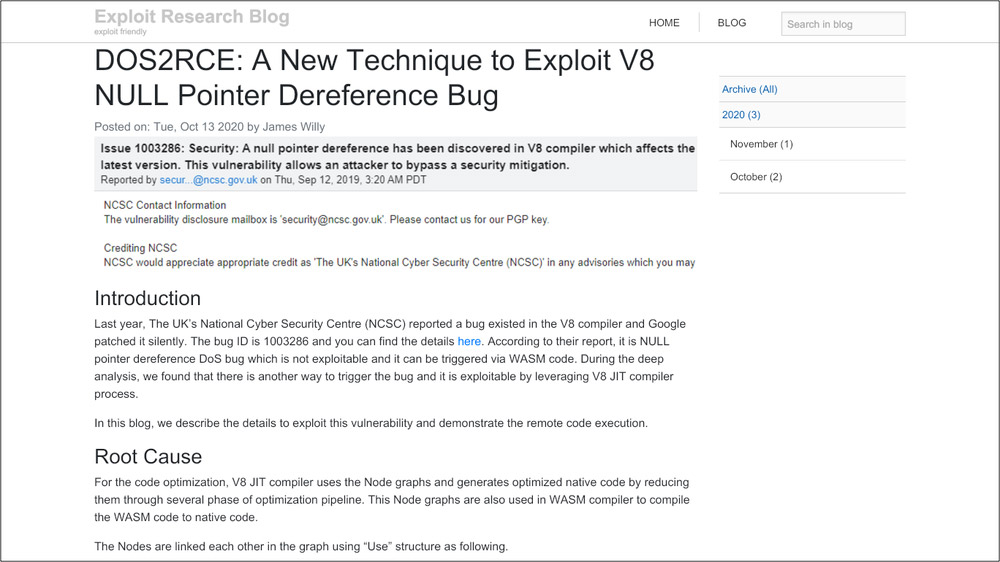
In other attacks seen by Google, researchers running fully patched Windows 10 systems and the Chrome browser who visited an attacker-controlled blog appeared to have been hit by a zero-day flaw - perhaps in Chrome - that installed an "in-memory backdoor" that "would begin beaconing to an actor-owned command-and-control server."
These actors have used multiple platforms to communicate with potential targets, including Twitter, LinkedIn, Telegram, Discord, Keybase and email. We are providing a list of known accounts and IOCs in the blog post.
— Shane Huntley (@ShaneHuntley) January 26, 2021
The hackers "have used multiple platforms to communicate with potential targets, including Twitter, LinkedIn, Telegram, Discord, Keybase and email," Shane Huntley, a researcher in Google's Threat Analysis Group, says on Twitter.
"They've used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits and for amplifying and retweeting posts from other accounts that they control," Google says.
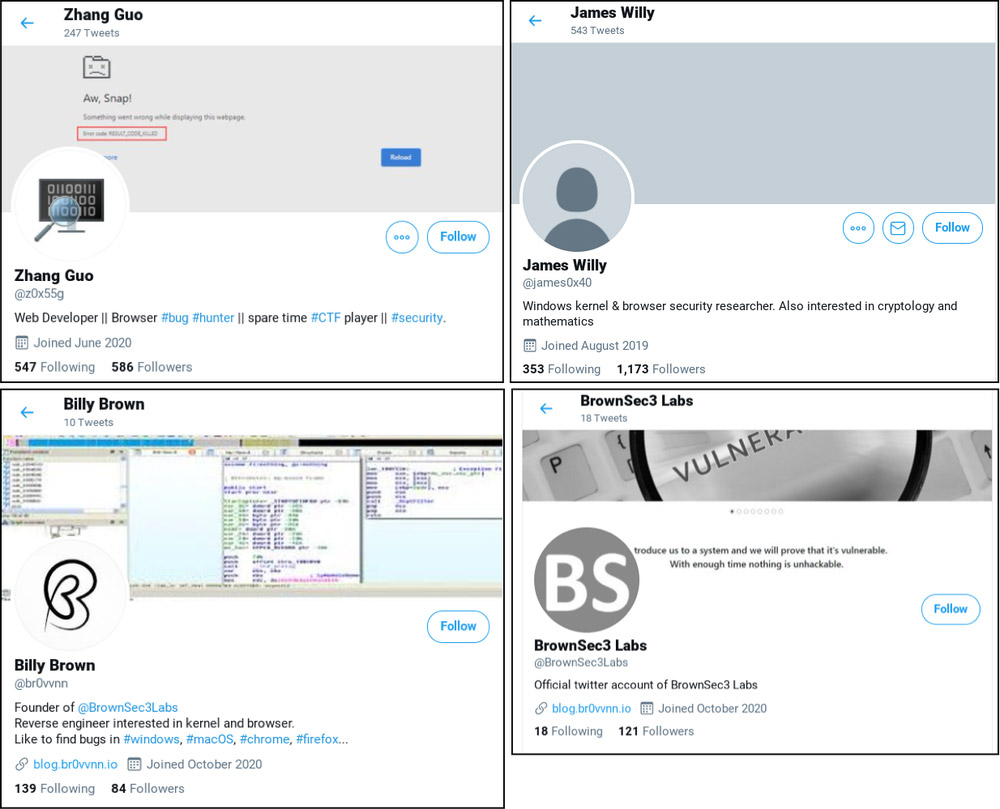
"We are providing a list of known accounts and aliases," Google says, as well as other indicators of compromise, including command-and-control URLs, file paths where malware may have been installed on compromised systems, and hashes for known malware. It recommends that any individual or organization that communicated with one of the attacker-controlled accounts immediately review their systems, using the IOCs, for signs of compromise.
Researchers Report Being Targeted
Several vulnerability researchers have reported that they were targeted.
One researcher who says he initially fell for the attack is Alejandro Caceres (@_hyp3ri0n). But at least in his case, he notes, any potential fallout was mitigated by the project he was working on being in a dedicated virtual machine, meaning attackers wouldn't have been able to access anything else on the system. He also notes that no customer data was exposed.
"A guy going by the name James Willy approached me about help with a zero-day. After providing a writeup on root cause analysis, I realized the Visual Studio project he gave me was backdoored," reports Caceres, who runs the small security research and development firm Hyperion Gray.
20k to anyone that gives me his full identity and address (and it's proven correct ofc). I will of course be approaching proper authorities at the DoD and LEA tomorrow. Thanks all.
— Alejandro Caceres (@_hyp3ri0n) January 26, 2021
Caceres reports that the flaw exploited by attackers "is well known" and that "Visual Studio even warns you to not open untrusted projects."
He adds: "But it was third-hand with a trusted party in between, and I was just helping out with some analysis, so I thought it was good. It was not."
Google, meanwhile, recommends that security researchers always safeguard themselves in the manner practiced by Caceres: "If you are concerned that you are being targeted, we recommend that you compartmentalize your research activities using separate physical or virtual machines for general web browsing, interacting with others in the research community, accepting files from third parties and your own security research."
Monthslong Campaign
"The campaign seems to have been ongoing for a while because the persona James Willy (james0x40) created his GitHub account on April 16," says security researcher Matt Suiche, who runs Dubai-based research firm Comae Technologies.
He's dubbed the operation "Pandorabox," given the various vulnerability lures being used to try and trick security researchers.
One outstanding question, he says, is how Google has attributed the campaign to North Korean hackers. "No explanation was given on the attribution," Suiche says in a blog post, although he points out that Kaspersky has noted that the malware has code similar to code previously used by the North Korean hacking group known as Lazarus.
KTAE code similarity analysis for the malware used to target security researchers involved in 0day analysis and development. "Manuscrypt" (also known as FALLCHILL) is typically used by the Lazarus APT. pic.twitter.com/hXxuJIj9Lc
— Costin Raiu (@craiu) January 26, 2021
"Note, that this alone isn’t enough for a successful attribution as it can be easily misled - maybe Google TAG has more information since they seemed to be so sure about who was behind?" Suiche says.
Security Firms Face Sustained Attacks
This is hardly the first campaign to target vulnerability researchers or the broader information security ecosystem. The SolarWinds supply chain attack discovered last month, for example, involves a backdoor apparently installed by Russian spies in the company's Orion network-monitoring software.
In recent years, organizations running unpatched VPNs and other security software from Pulse Secure, Fortinet and Palo Alto have also been regularly targeted by crime gangs and nation-state hackers.
This week, security vendor SonicWall warned that it's investigating an apparently "coordinated attack" against its internal network by hackers who have been wielding a zero-day exploit in the company's remote access products.
"The shoemaker's children go barefoot. Whilst not a new thing, owning those in security has been part and parcel of the internet for a long time," tweets Daniel Cuthbert, who's a member of the Black Hat Review Board, founding member of the Open Source Foundation for Application Security, and a longtime bug hunter.
Especially in recent times, however, "the overall security industry has had a poor run … from nearly every VPN provider showing that appsec is hard, to examples like this (that are public)," he says, referring to the campaign targeting vulnerability researchers detailed by Google. "We need to be much better."






















