Cybercrime , Fraud Management & Cybercrime
Ursnif Banking Trojan Variant Steals More Than Financial Data
Researchers Say Latest Version Evades Detection
A newly discovered variant of the long-running Ursnif banking Trojan is able to better evade security protection and has the ability to steal not only financial information but also email user accounts, the content of inboxes and digital wallets, researchers report.
See Also: Ransomware Demystified: What Security Analysts Need to Know
Researchers at Cybereason first noticed the new Ursnif campaign earlier this year. The Trojan, which also goes by the name Gozi, has been around for more than 10 years, but it has become more popular since 2015, when someone posted the source code on Github.
Since then, malicious actors have tweaked the code to meet their needs, and several variants of Ursnif have appeared - mainly attacking banks and other financial institutions. Researchers at Cybereason found the new variant by monitoring customer data and other information from January and February.
In this latest campaign, which Cyberseason analysts describe in a March 12 blog post, the Trojan has only been spotted in Japan, and the full extent of these attacks is still under investigation.
Assaf Dahan, a security researcher with Cybereason, tells Information Security Media Group that the actors behind these types of Trojans generally know which banks and which customers they want to target.
Targeted Attacks
While other versions of Ursnif have been observed in attacks elsewhere, including the U.S., Brazil, Asia and Europe, the new version has been customized to target Japanese-speaking bank customers, according to Cybereason.
"It's in the interest of the attackers to make the target as deliberate as possible," Dahan said. "If by accident, this malware reaches someone in Brazil, or an American laptop, it simply wouldn't run. They wouldn't want to waste their time targeting an audience that they could not make money from. ... In addition to social engineering, the malware makes sure that the computer settings are in Japanese."
As banking security has hardened and more customer have used mobile banking apps, attackers have switched to using Trojans such as Ursnif to steal other types of data, including email configurations, as well as credentials and passwords stored in web browsers and even digital wallets, according to Cybereason.
"You put in the hard work of infiltrating a system or infecting a machine, and you make sure you bypass all the security products - why would you only steal banking information?" Dahan asked. "There are other things, such as personal information, that can be sold later in the black market for a lot of money. If they are already there, they might as well collect all the information that they can get their hands on. ... With this variant, it's much more focused on stealing other information, especially email information."
If Ursnif embeds within a corporate network, it has the potential to steal internal emails, which may contain proprietary information that can either be sold or used to create a larger footprint within the network, Dahan added.
How It Starts
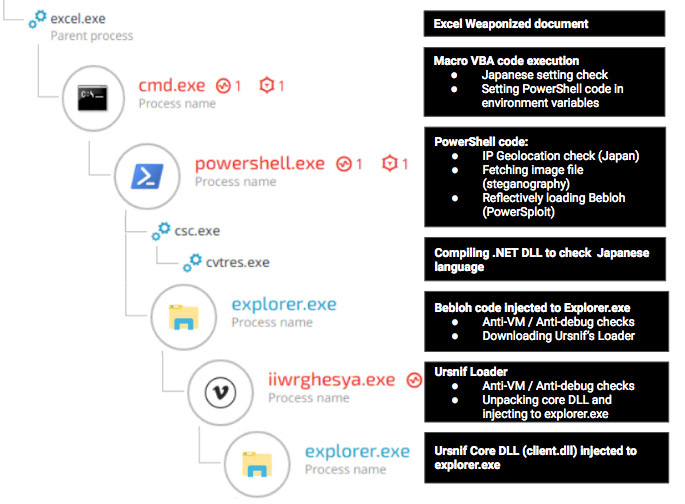
Attacks using the latest version of Ursnif start with a phishing attack. In many cases, a phishing email is sent to a victim that contains a malicious attachment - typically an Excel spreadsheet. If the victim clicks on an "Enable Content" button, they will not see the spreadsheet; rather an embedded macro code, which contains PowerShell commands, is then downloaded, according to Cybereason.
The commands also ensure that the infected PC has Japanese country settings.
The PowerShell code then downloads an image from an image-sharing website. The attackers use steganography to hide their intent, Cybereason reports.
A Stealthy Campaign
One of the new features within this Ursnif variant is what researchers deem a stealthy persistence mechanism, or "last minute persistence." This is a method of trying to install the malicious payload in the shortest time possible to avoid detection by security software.
"This malware, unlike other versions, changes its persistence to be stealthy," Dahan said. "In previous versions, they just write this key and drop their files and configure the file to run as soon as the machine boots, or when the user logs into the machine. But since it's written on a disk or in Windows registry, it's easy to detect if you know where to look for it. In this variant, you wouldn't see it because it simply does not exist on the disk. At the very last minute, when the PC shuts down, it will create its persistence. When the user logs back in, in a fraction of a second, it then deletes that persistence and removes any evidence from the disk."
Once the infected PC is turned back on, the full attack starts.
The initial payload hidden in the PowerShell code is another Trojan called Bebloh - also known as URLZone and Shiotob - which is used as a downloader that runs a number of tests to ensure that it's running within the system and not an isolated virtual machine being used as a sandbox. If the coast is clear, the main Ursnif malware begins downloading and then can start stealing credentials, passwords and data.
Dahan noted that researchers are starting to notice more of these types of attacks using two different types of Trojans. In the latest campaign tracked in Japan, the attackers coupled Ursnif with Bebloh because Bebloh is better at detecting sandboxes and helps to ensure that the attack is carried out without detection.
It's not clear what group may be behind the new variant Ursnif. And, so far, it's only appeared in Japan, Dahan says. But that could change.
Banking Trojan Surge
Ursnif is one of thousands of banking Trojan in use - and the numbers keep increasing. A recent report from Kaspersky Lab found that in 2018, 889,452 users of the company's security tools were attacked by banking Trojans. That's an increase of about 16 percent from 2017.
Of all the Trojan attacks recorded in 2018, 24 percent were within the corporate sector, which includes not only employees giving away banking and other data, but also malware allowing cybercriminals to compromise financial resources, Kaspersky found.