Account Takeover Fraud , Cybercrime , Fraud Management & Cybercrime
Twitter Hack: Suspects Left Easy Trail for Investigators
Bitcoin Accounts Linked to Driver's Licenses, Leading to Arrests
Suspects in the epic attack against Twitter were uncovered, in part, by the use of their real photo identification for cryptocurrency accounts they used to broker the sale of stolen usernames. The mistakes proved crucial to their identification, according to court documents.
See Also: Spear Phishing: Top 3 Threats
In court filings, the FBI, U.S. Secret Service and the state of Florida describe the elaborate, lengthy and multistage process three hackers allegedly used to gain access to 130 high-profile Twitter accounts on July 15 to wage a brief cryptocurrency scam (see: 3 Charged in Twitter Hack).
The information that showed the attack's road map appeared in filings from U.S. Attorney's Office for Northern District of California and Florida state attorney for Hillsborough County that charge Graham Ivan Clark, of Tampa, Fla., also known as Kirk#5270; Mason John Sheppard, of the U.K., also known as “Chaewon” and “ever so anxious#001; and Nima Fazeli, of Orlando, also known as “Rolex,” “Rolex#0373,” “Rolex#373,” and “Nim F”.
Sheppard is charged with computer intrusion, wire fraud conspiracy and money laundering conspiracy, while Fazeli is charged with one count of computer intrusion.
Clark was arrested by federal agents on July 31 and charged by the U.S. Attorney's Office for Northern District of California and the state attorney for Hillsborough County, Florida. Clark faces 30 charges and as of Monday remains in jail on $725,000 bail.
The FBI says another arrest was made, but it has not released that person's name or additional details.
The Twitter Hack
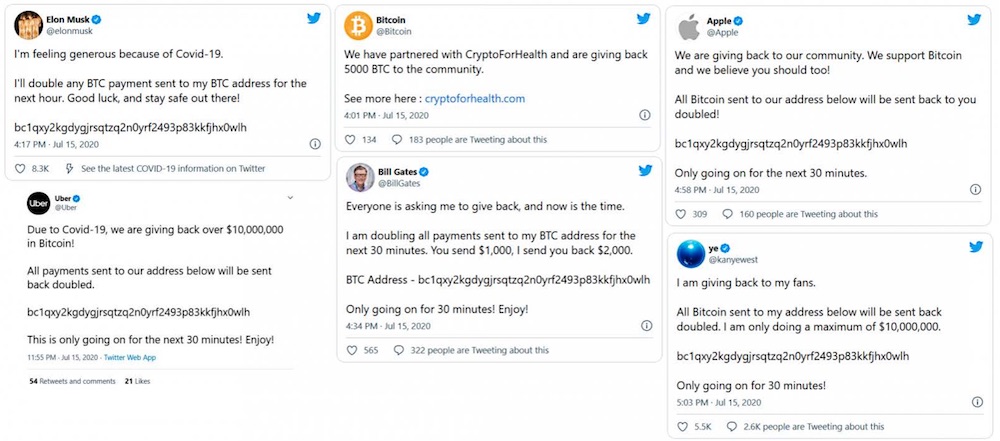
The incident took place on July 15 when several Twitter employees were victimized by a phone-based spear-phishing attack that provided the hackers with credentials for the social media firm's internal systems and tools enabling their takeover, Twitter reported last week.
The malicious actors used stolen credentials to take over 130 accounts, and then they tweeted from 45 of them, the social media company says. The tweets falsely said the owners of the accounts would send double the number of bitcoins back to accounts that sent in money. The hackers also accessed the direct message inbox of 36 accounts and downloaded the Twitter data of seven, according to Twitter.
But before the hack took place investigators say the 17-year-old Clark, the alleged mastermind of the operation, took the first steps to set things in motion several months earlier, according to Andrew Warren, the state attorney for Hillsborough County, Florida.
First Steps
On May 3, Clark, aka Kirk#5270, allegedly did "willfully, knowingly and without authorization access and cause to be accessed a computer, computer system, computer network and electronic devices used by Twitter," according to a court filing from the 13th Judicial Circuit of the state of Florida.
The court records do not specify what happened on May 3 nor what Clark allegedly did between that date and when the attack took place on July 15.
On July 15, however, a person with the handle Kirk#5270 allegedly made a statement on a Discord online chat forum "that he/she could reset, swap and control any Twitter account at will, and would do so in exchange for bitcoin transfers," according to court documents.
The Discord conversation was gathered via a search warrant issued to investigators that enabled them to access Discord's files relating to any conversations between Kirk#5270 and others.
Investigators obtained an image of an internal administrative tool used by Twitter to make changes to user accounts that were sent by “Kirk#5270” to an unidentified individual who used the Discord moniker “Rolex#0373”, which is associated with Fazeli.
"Upon receiving the image, Rolex#0373 responded with 'Damn', and later, 'I’m in,'" the court documents say.
Allegedly, Kirk#5270 (Clark) immediately provided Rolex#0373 (Fazeli) with a bitcoin address that investigators interpreted as Kirk#5270 asking for payment for access to the Twitter accounts, the court documents say.
At the time this Discord conversation allegedly was taking place, Kirk#5270 was providing proof of access to a wide variety of Twitter accounts to another Discord member named "ever so anxious#001", aka Sheppard.
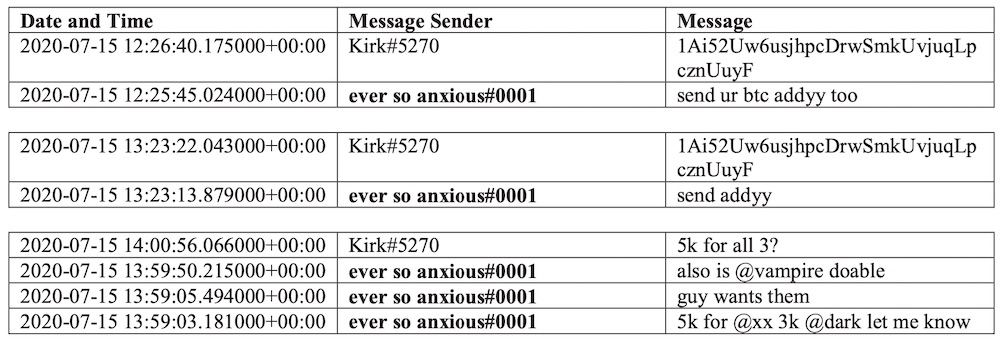
"For example, 'Kirk#5270' provided images of administrator-level access to Twitter accounts '@bumblebee,' '@sc,' '@vague,' and '@R9,' among many others. Based on the entire chat, it appears that 'ever so anxious#0001' began to find buyers for Twitter usernames," the court documents say.
Twitter told the FBI that three of the accounts mentioned in the Discord conversation, @xx, @dark, and @vampir, were compromised in the July 15 attack, the court documents say.
Also on July 15, the court filings note, several members of the OGUsers darknet forum began advertising illicit access to any Twitter account.
"A user named Chaewon, aka Sheppard, advertised that he could change email addresses tied to any Twitter account for $250 and provide direct access to accounts for between $2,500 and $3,000," the court document says.
Investigators using blockchain analysis found several deposits and withdrawals to the wallet associated with Kirk#5270 (Clark) on July 15 totalling 3.69 bitcoin, or about $33,000, from a cluster of wallets associated with Sheppard called the Chaewon cluster. The timing and amounts of these deposits correspond with the timing of payment requests made by “Kirk#5270” to “ever so anxious#0001” (Sheppard) for stolen Twitter usernames, the investigators say.
Investigators also found additional money transfers related to the Twitter hack also took place from "ever so anxious#0001".
The investigators were able to determine that by the time the hack concluded, the bitcoin address associated with the attack handled about 415 transactions totalling 12.86 bitcoin, worth about $117,457, which is the amount that was scammed from the 130 victims.
Search Warrant Executed
On July 31, federal agents executed a search warrant in the Northern District of California at a residence where a juvenile believed to be Discord user Kirk#5270 was located. The federal court papers do not identify Clark by name due to his age but refer to him as Juvenile 1.
Juvenile 1 was found at the residence and agreed to be interviewed. He allegedly admitted that he was Discord user Kirk#5270 and participated in the sale of illegal Twitter access, knew Chaewon by the name Mason and that the person lived in the U.K. Juvenile 1 said he and Chaewon considered turning themselves into police once the Twitter attack became public, the court documents say.
Juvenile 1, (Clark) was placed under arrest in Tampa on July 31. The court documents did not mention extradition to Florida, but the Florida state attorney handling the case says Clark is a Tampa resident and will be tried as an adult by his office.
Final Attribution
Investigators were able to tie Sheppard and Fazeli to the various cryptocurrency wallets and Discord accounts involved using their driver's license numbers, which the two used to verify their cryptocurrency wallets.
In Fazeli's case, investigators used an IP address associated with the Rolex#0373 Discord account, Coinbase wallets and the Rolex OGUsers account, giving them enough evidence to conclude they were controlled by the same person, according to court documents.
Sheppard was identified in a similar fashion through his Binance cryptowallet account that also allegedly contained his driver's license photo, the investigators say.