Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Tupperware Website Hit by Card Skimmer
Researchers Say Magecart-Style Attack Targeted Payment Card Data
Tupperware, known for its colorful array of food storage containers, is the latest company to have its website hit with a card skimmer that siphons off payment card details at checkout, according to the security firm Malwarebytes.
See Also: OnDemand | API Protection – The Strategy of Protecting Your APIs
A Tupperware spokesman tells Information Security Media Group that as of Thursday, the company had removed the malicious code from its website and started an investigation.
"Tupperware recently became aware of a potential security incident involving unauthorized code on our U.S. and Canadian ecommerce sites," the company spokesperson says. "As a result, we promptly launched an investigation, took steps to remove the unauthorized code, and a leading data security forensics firm was engaged to assist in the investigation."
Malwarebytes says its researchers first came across the malicious JavaScript on March 20 and attempted to alert Tupperware about the attack, but the company did not immediately reply to calls or emails. Tupperware responded only after the research was published on Wednesday, Malwarebytes says.
Following publication of the blog, we noticed that the malicious PNG file has been removed. This will break the skimmer.
— MB Threat Intel (@MBThreatIntel) March 25, 2020
However, other artifacts remain present and a full security sweep will be necessary. pic.twitter.com/BAuByz8KsZ
It's not yet clear how much payment card data may have been stolen or whether any has been offered for sale on dark net sites, Malwarebytes says.
Ongoing Attacks
Jérôme Segura, director of threat intelligence at Malwarebytes, tells Information Security Media Group that the skimmer attack likely lasted for at least five days. Tupperware attracts about 1 million visitors each month, the Malwarebytes research report notes.
Segura believes this attack is likely the work of Magecart, an umbrella name for a group of cybercriminal organizations that have been planting JavaScript skimmers, also known as JavaScript sniffers or JS sniffers, on dozens of ecommerce sites to steal payment card data (see: Magecart Group Continues Targeting E-Commerce Sites).
As more consumers turn to ecommerce as a result of the spread of COVID-19, Segura expects these types of skimming attacks are likely to increase.
"It's really important for online merchants to secure their sites and have a point of contact so that defenders can report these breaches," Segura says. "Web skimmers have been one of our top detections as far as web threats are concerned, and we are closely monitoring them during this period."
Deceptive Images
The Malwarebytes researchers noticed a suspicious iframe on the Tupperware website during a routine scanning exercise earlier this month.
The iframe displays the image a shopper sees during the checkout process. When Malwarebytes looked at the iframe on the Tupperware site, however, it was loading content from a domain called "deskofhelp.com," which was registered on March 9 and has been tied phishing attacks, according to the report.
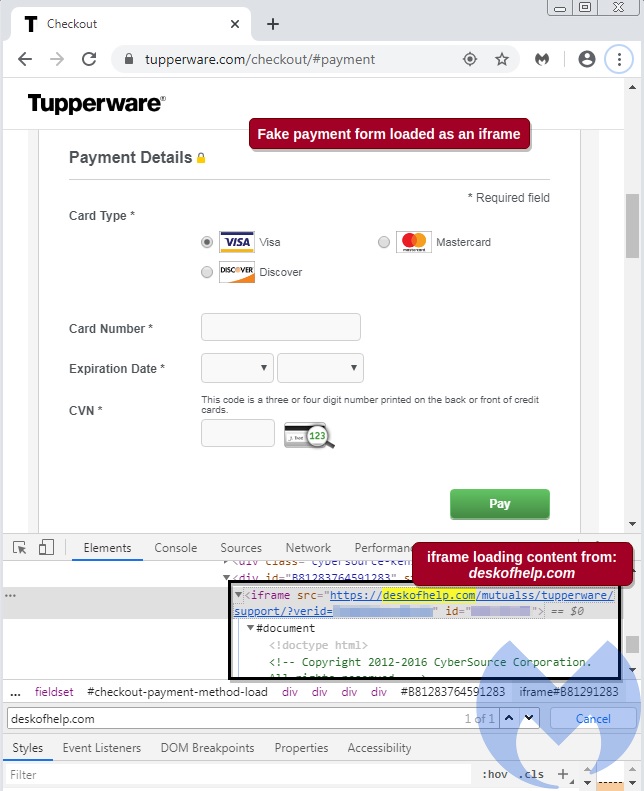
The Malwarebytes researchers saw that the form created by the malicious iframe would collect shoppers' first and last name, billing address, telephone number, credit card number, credit card expiry date and CVV number. When customers attempted to check out, they would receive an error message, the report notes.
The attackers' JavaScript injection would then collect the data and store it. At the same time, the fake checkout page created by the suspicious iframe would disappear and be replaced by the legitimate one, Malwarebytes notes. If a shopper then entered the same payment details, the transaction would go through.
Difficult to Detect
"The most interesting thing here is how threat actors built this iframe dynamically without leaving too many traces. Even though we caught it, we think most web scanners would have missed it," Segura says. "The technique in itself is not new, but a little bit more elaborate than usual, in particular because embedding data into images - steganography - can make identification harder."
One tipoff that something was wrong is that the attackers did not adjust the malicious checkout forms for different versions of the Tupperware websites. For instance, an English language version of the fake page appeared on the Spanish version of Tupperware's website, according to Malwarebytes.
In addition to the malicious iframe and fake checkout form, the Malwarebytes researchers also found code on the Tupperware homepage that would dynamically call a "FAQ" icon stored on one of the company's servers. When a shopper attempted to checkout, that FAQ icon would silently load in the background, along with the malicious JavaScript, and instruct the iframe to load the fake checkout form to collect the payment data, the report notes.
Other Attacks
Other retailers have recently been targeted by Magecart groups. For example, TechCrunch reported that Magecart hackers broke into blender-maker NutriBullet's website several times over the past two months and infected the payment pages with JavaScript skimmers.
In addition, researchers reported this month that payment card data stolen last year when hackers compromised online stores that were using the Volusion checkout platform is now surfacing on dark web sites and forums (see: For Sale: Card Data From Online Stores Using Volusion).
Managing Editor Scott Ferguson contributed to this report.





















