Governance & Risk Management , Incident & Breach Response , Managed Detection & Response (MDR)
Supply Chain Woes, Again: NetSarang Popped
Server Management Vendor Backdoored; Updates Issued
There's little defense against software updates that have been seeded with malicious code. Companies trust that the software delivered by their suppliers is legitimate.
See Also: Deception-Based Threat Detection: Shifting Power to the Defenders
Unfortunately, that doesn't always turn out to be the case. Kaspersky Lab says it found a data-stealing backdoor called ShadowPad planted in five software packages from server management vendor NetSarang.
The updates were available for more than two weeks before NetSarang was notified by Kaspersky Lab.
"ShadowPad is an example of the dangers posed by a successful supply-chain attack," Kaspersky writes. "Given the opportunities for covert data collection, attackers are likely to pursue this type of attack again and again with other widely used software components."
Victim in Hong Kong
NetSarang specializes in software that enables administrators to securely manage and link Unix, Linux and Windows machines. Its customers include big names in a variety of verticals, including Bank of America, Gazprom, Intel, IBM, 3M and Lockheed Martin.
The group behind the backdoor is unknown and left few traces, Kaspersky writes in a blog post. But the techniques used are similar to PlugX, a remote access Trojan, and Winnti, another backdoor, Kasperky reports.
Although ShadowPad is designed to infect and then wait for instructions, its developers did launch it against a Hong-Kong-based company, Kaspersky writes. The company was not identified.
NetSarang wrote in an advisory that the backdoor was discovered on Aug. 4. The affected products, which were released on July 18, were Xmanager Enterprise 5.0 Build 1232, Xmanager 5.0 Build 1045, Xshell 5.0 Build 1322, Xftp 5.0 Build 1218, and Xlpd 5.0 Build 1220.
"Given that the NetSarang programs are used in hundreds of critical networks around the world, on servers and workstations belonging to system administrators, it is strongly recommended that companies take immediate action to identify and contain the compromised software," Kaspersky writes.
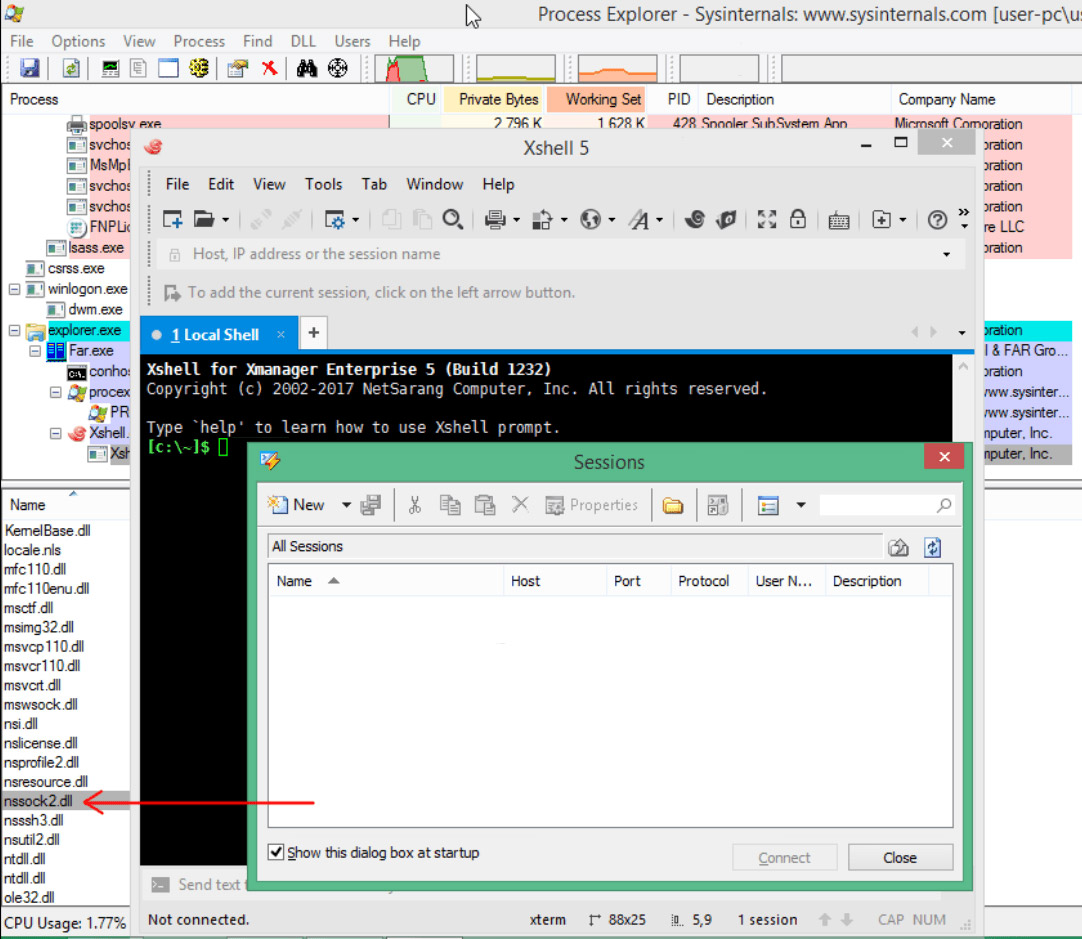
NetSarang says that the security industry has been given a heads-up about the tampered software, which can be detected by the presence of a DLL file. If that file is quarantined by anti-virus software, the application will no longer run. Those organizations that are running tampered software must manually download the updates, it says.
Tampered Update Was Signed
It's no easy feat for attackers to subvert software. They have to gain deep access to a software developer, including access to source code and the digital signing infrastructure. In its advisory, NetSarang did not address how it had been breached.
Kaspersky notes: "An investigation is in progress, but since code was signed and added to all software packages it could point to the fact that attackers either modified source codes or patched software on the build servers."
This kind of attack is exactly how the NotPetya ransomware initially spread in June. The attackers gained access to a Ukrainian account software vendor, MeDoc, which develops one of only two software packages approved by Ukraine's tax-collection agency for paying taxes (see Teardown of 'NotPetya' Malware: Here's What We Know).
The attackers inserted a backdoor into three software updates, which were then distributed to customers. Investigators uncovered later that the updates contained fake digital certificates.
Odd DNS Queries
If a software update is signed with the developer's digital certificate, that's supposed to indicate that the particular build hasn't been modified. But in the case of NetSarang, the tampered software began acting odd.
Kaspersky says strange DNS requests were the tipoff. DNS resolves domain names into IP addresses that can be called into a browser. DNS requests can be monitored and tracked.
"The partner, which is a financial institution, detected these requests on systems related to the processing of financial transactions," the company writes. "Our analysis showed that the source of these suspicious requests was a software package produced by NetSarang."
To begin using the backdoor, the attacker has to activate it. Once turned on, it can allow someone to upload files, create processes and then store that information in a virtual files system located in the victim's registry, Kaspersky writes.
Kaspersky praised NetSarang for acting quickly after it was notified, which may have helped prevent hundreds of further attacks. But it warned that attackers will continue to try to corrupt widely used software.
"This case is an example of the value of threat research as a means to secure the wider internet ecosystem," the company writes. "No single entity is in a position to defend all of the links in an institution's software and hardware supply-chain."

















