Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Severe Citrix Flaw: Proof-of-Concept Exploit Code Released
Attackers Probe for Vulnerable Systems as Citrix Races to Develop Patches
Technology giant Citrix says it's racing to develop patches to fix a severe flaw in its software, for which proof-of-concept exploit code has now been released. Security experts say tens of thousands of organizations are at risk from the flaw, first disclosed last month, which could give attackers remote access to corporate networks.
See Also: The State of Organizations' Security Posture as of Q1 2018
On Saturday, a group calling itself Project Zero India - a cheeky nod to Google’s Project Zero bug-hunting team - published proof-of-concept code for the vulnerability. Designated CVE-2019-19781, the directory traversal flaw has been present in Citrix's code for nearly six years, but only came to light - at least publicly - in December 2019.
Project Zero India’s dump of the exploit code prompted consultancy TrustedSec to shortly thereafter release its own proof-of-concept exploit code.
“This was only uploaded due to other researchers publishing their code first,” TrustedSec writes in a post on GitHub. “We would have hoped to have had this hidden for a while longer while defenders had appropriate time to patch their systems. We are all for responsible disclosure. In this case, the cat was already out of the bag.”
Other security experts have said that once the flaw came to light, they were able to build a working exploit in little time.
“I was able to reproduce the Citrix ADC remote command execution in one day,” writes Rio Sherri, a senior security consultant with British consultancy and training firm MCSec. “Guess you need to patch ASAP."
Apply Citrix’s Mitigations
The directory traversal flaw exists in Citrix’s Application Delivery Controller and Gateway. Citrix has warned that the flaw is remotely exploitable and could allow access to applications and the internal network (see: Citrix Vulnerability Could Affect 80,000 Companies: Report).
The flaw was discovered by Mikhail Klyuchnikov, a researcher at London-based vulnerability assessment firm Positive Technologies. When the firm first announced the flaw last month, it estimated that 80,000 enterprises across 158 countries were potentially affected.
Experts say the risk posed by the vulnerability is severe. The U.S. National Security Agency's Rob Joyce, who's the senior adviser for cybersecurity strategy to the director, says via Twitter that the vulnerability is a “doozie.”
The Citrix RCE is a doozie. Lots of good security architectures appropriately rely on Citrix to reduce the attack surface significantly and now they are at significant risk. Get this patched. https://t.co/7B9d7e7YK7
— Rob Joyce (@RGB_Lights) January 10, 2020
One challenge for organizations that use the vulnerable Citrix software, however, is that the vendor has yet to issue any patches. Instead, affected organizations have been issued a list of mitigations they must put in place.
But Citrix says it's hard at work to develop patches for affected software. For Application Delivery Controller and Gateway versions 11.1 and 12, Citrix is promising a patch by Jan. 20. Patched versions of 12.1 and 13 are due by Jan. 27, and version 10.5 is due to get a patch by Jan. 30.
“We are currently working to develop permanent fixes," Citrix CISO Fermin J. Serna wrote in a blog post on Saturday. "As with any product of this nature, and consistent with our policies and procedures, these fixes need to be comprehensive and thoroughly tested.”
Positive Technologies has praised Citrix for moving quickly to contain this problem. In its announcement of the flaw, posted on Dec. 23, 2019, the security firm said that Citrix "responded very promptly, by creating and releasing a set of risk mitigation measures within just a couple of weeks after the vulnerability was discovered," adding that "from our experience, we know that in many cases it can take months."
In the meantime, security experts say organizations should have already put in place those multiple mitigations detailed by Citrix.
British security researcher Kevin Beaumont says the mitigations “so far seem fairly strong. So I’d deploy those.” But he also cautions that the mitigations might break some functionality.
Honeypots Spot Attack Probes
Attackers have been hunting for systems running the vulnerable software since last week, researchers say.
Johannes B. Ullrich, director of the SANS Institute's Internet Storm Center, said on Tuesday that his honeypots had detected efforts to identify vulnerable systems, although so far he had not seen any exploit attempts. He noted that the scans weren’t sophisticated.
Warning:
— Bad Packets Report (@bad_packets) January 12, 2020
Mass scanning activity detected from 156.17.191.239 checking for Citrix (NetScaler) Gateway servers vulnerable to CVE-2019-19781.
Ports targeted: 443, 2083, 2087, & 8443/tcp
Mitigation steps to prevent compromise: https://t.co/c9f22TfP2K #threatintel pic.twitter.com/QCUxDrbl9Z
But that activity has evolved in recent days. Troy Mursch of Chicago-based threat intelligence firm Bad Packets reports that he saw mass scanning activity coming from an IP address in Poland on Sunday, following probes from Germany, searching for vulnerable systems.
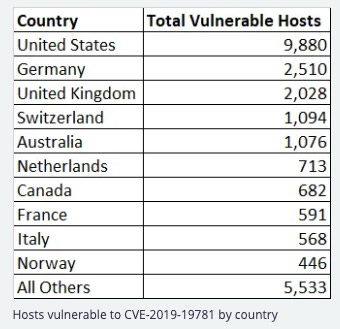
"We’ve discovered this vulnerability currently affects: military, federal, state, and city government agencies; public universities and schools; hospitals and healthcare providers; electric utilities and cooperatives; major financial and banking institutions; and numerous Fortune 500 companies," Mursch says in a Sunday blog post.
Honeypots run by Beaumont, meanwhile, have detected some unsophisticated attempts to install coin miners, or scripts that mine for cryptocurrency. But Beaumont - who has jokingly dubbed the vulnerability “Shitrex” - warns that enterprises need to keep several aspects of the flaw in mind, given the risk it poses.
First and foremost, Beaumont says via Twitter, the flaw is in the ADC and Gateway products themselves, so whether an organization is running a firewall or using multi-factor authentication makes no difference as to its level of exposure. Also, whether or not an enterprise actually uses SSL VPN functionality doesn’t alter its risk exposure.
In addition, intrusion prevention and detection systems won't block attempted exploits, he says. “IPS (Intrusions Prevention Systems) are great but … well, don’t rely on them. Why? The traffic is TLS-encrypted. Your IDS almost certainly can’t see inside it to see threats, unless you’re a unicorn and have SSL decryption and decryption [certificates] for every host on your network and rotate."
Accordingly, Beaumont recommends that all organizations determine if they're exposed to the flaws by using a tool such as Shodan Monitor, which can be set to email administrators if they detect these types of problems.
Executive Editor Mathew Schwartz contributed to this story.






















