Application Security , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Report: Chinese Hackers First to Use NSA Cyberattack Tools
Symantec Report Deepens Mystery Around Lost NSA Tools and Exploits
A Chinese hacking group was using exploits and attack tools developed by the U.S. National Security Agency a few months before another group released the tools, Symantec says in a new report.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
The surprising report deepens the mystery around an extraordinary situation in which some of the U.S.'s most effective cyber weapons fell into the wrong hands. The repercussions, including the devastating WannaCry ransomware attack in May 2017, continue to play out today.
It also raises questions about the Vulnerabilities Equities Process, a U.S. government program that discloses software vulnerabilities to vendors so they can be patched.
Unpatched vulnerabilities help U.S. cyber spies infiltrate other systems. But failing to notify the vendors of those problems means it's possible other countries or cybercriminals will discover and exploit them.
Symantec announces that a Chinese APT group was using EternalRomance and EternalSynergy before being released by the Shadow Brokers. This completely kills the NOBUS argument and raises some serious questions about the Vulnerability Equities Process (VEP). https://t.co/seXMs8bHuw
— Jake Williams (@MalwareJake) May 7, 2019
The situation outlined by Symantec raises questions about software flaws that are tightly held by the U.S. or so-called NOBUS flaws, which stands for "nobody but U.S.", writes Jake Williams, a former operator with the National Security Agency's Tailored Access Operations unit and founder of Rendition Infosec, a security consultancy in Atlanta.
"This completely kills the NOBUS argument and raises some serious questions about the Vulnerability Equities Process (VEP)," Williams writes on Twitter.
Buckeye, aka APT3 and Gothic Panda
Symantec calls the Chinese hacking group Buckeye; it's also known as APT3 and Gothic Panda. Some cybersecurity companies, including Crowdstrike and Recorded Future, believe that APT3 works with China's intelligence agency, known as the Ministry of State Security.
Symantec has been tracking attacks linked to Buckeye in Belgium, Luxembourg, Hong Kong, Vietnam and the Philippines, including against telecommunication companies and science and technology.
As is customary, Symantec doesn't mention China in its report. The leaked exploits and tools came from the Equation Group, Symantec says. The Equation Group, discovered by Kaspersky, is strongly believed to be the NSA's offensive cyber operations unit, which used to be known as Tailored Access Operations.
It is unclear how Buckeye obtained the tools, but Symantec has two theories. Buckeye "may have engineered its own version of the tools from artifacts found in captured network traffic, possibly from observing an Equation Group attack," Symantec says.
Another less likely scenario is that Buckeye gained access to a poorly secured server used by the Equation Group, or that someone with the Equation Group leaked the tools.
But Buckeye's use of the tools and exploits predates their release by the Shadow Brokers. In August 2016, the Shadow Brokers released samples of exploits and software implants it claimed came from the Equation Group.
Security experts concluded that the tools were legitimate and likely came from a highly sophisticated group. It was theorized that perhaps a disgruntled NSA employee or contractor was the Shadow Brokers, or maybe the tool dump was a bold, provocative prank by Russia. So far, no one has been charged.
Buckeye began using a variant of the DoublePulsar backdoor in March 2016, Symantec says. The backdoor was delivered to victims using an exploit tool called Bemstour. Bemstour used two zero-day vulnerabilities for Windows, CVE-2019-0703, and CVE-2017-0143.
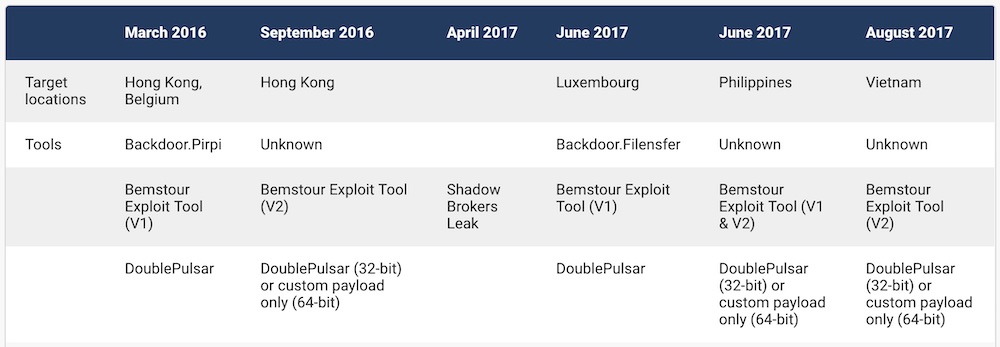
Bemstour continues to be developed. In fact, Symantec says it analyzed a sample that was compiled on March 23.
"The purpose of all the attacks was to acquire a persistent presence on the victim's network, meaning information theft was the most likely motive of the attacks," Symantec writes.
Buckeye also used two exploit tools known as EternalRomance and EternalSynergy, both of which were also released by the Shadow Brokers.
Tools Still in Use
Symantec says Buckeye appeared to stop its attacks around mid-2017. A few months later, in November 2017, three Chinese men believed to be part of the group were charged with breaking into U.S. companies, including Siemens, Moody's Analytics and Trimble.
The U.S. has no extradition agreement with China, so the men have not been arrested. The men worked for Bo Yu Information Technology Company Ltd., or Boyusec for short, which was based in Guangzhou. Boyusec was believed to have been connected with APT3 and Gothic Panda (see: Chinese Cybersecurity Workers Hacked Firms, US Charges).
Even though Buckeye's activity ceased, there are still risks. Another group began using the tools through the end of last year, Symantec says.
There's often vigorous debate over when the U.S. should disclose software flaws that give the U.S. an intelligence advantage. A more prompt notification process may have allowed Microsoft to patch the Server Message Block vulnerability (CVE-2017-0144) sooner, which may have given organizations more time to protect themselves from WannaCry. Microsoft patched the SMB vulnerability weeks before WannaCry was unleashed in May 2017.
But there's risk in developing exploits for vulnerabilities in the first place, argues Robert M. Lee, founder and CEO of Dragos, which specializes in securing industrial control systems. If those exploits are deployed, it may be possible for adversaries to reverse engineer or discover them.
My late night take: if we're going to yell at the NSA for making an exploit that an adversary saw in an intrusion and learned from as an example of "losing control of weapons" then we should just argue that no one should make exploits ever because they can all be lost in that way
— Robert M. Lee (@RobertMLee) May 7, 2019