Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware
Ransomware Operators Using SystemBC Malware as Backdoor
Researchers Have Seen Commodity Malware Used With Ryuk and Egregor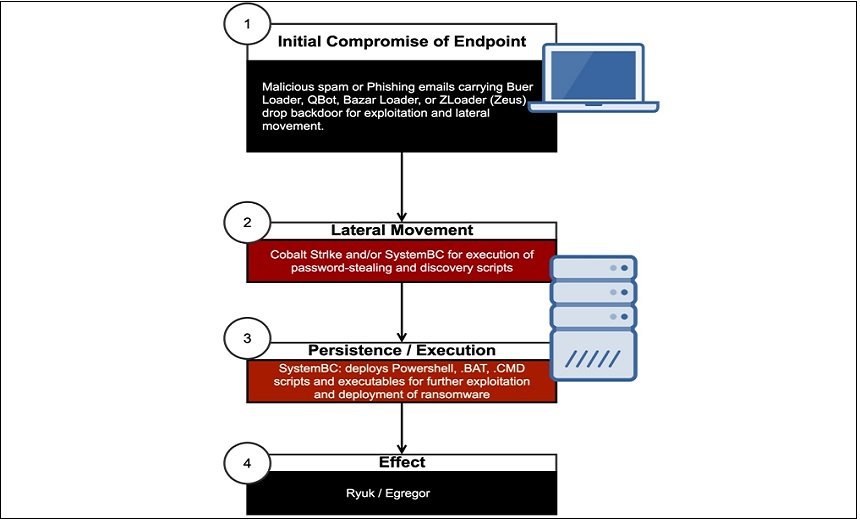
Several recent ransomware attacks, including those involving Ryuk and Egregor, have used a commodity malware variant called SystemBC as a backdoor, security firm Sophos reports.
See Also: 2022 Elastic Global Threat Report
First uncovered by security firm Proofpoint in August 2019, SystemBC works as a network proxy for concealed communications and as a remote access Trojan, or RAT, that allows threat actors to deploy additional commands and scripts to infected Windows devices and to gather data.
While researchers have tracked SystemBC over the years, the Sophos report finds that its creators have added new features, which ransomware operators and their affiliates are taking advantage of to deploy their crypto-locking malware.
Sophos found that the SystemBC malware now uses the Tor anonymizing network to encrypt and conceal the destination of command-and-control server traffic. This not only helps obfuscate the attackers’ communications but also allows them to better hide when data is gathered and exfiltrated, according to the report.
"Collectively, these capabilities give attackers a point-and-shoot capability to perform discovery, exfiltration and lateral movement with packaged scripts and executables - without having to have hands on keyboard," Sophos analysts Sean Gallagher and Sivagnanam Gn note in the report. "These capabilities were originally intended for mass exploitation, but they have now been folded into the toolkit for targeted attacks - including ransomware."
Ransomware Deployments
Since September, the Sophos researchers have found SystemBC deployed in separate ransomware attacks and delivered using different methods, according to the report.
During a September Ryuk attack, for example, the SystemBC malware was deployed in phishing emails along with other malware, such as the Buer loader and the Bazar backdoor, the report notes (see: Ryuk Ransomware Delivered Using Malware-as-a-Service Tool).
In an Egregor incident in November, the attackers deployed Buer along with Qbot, another type of banking Trojan that can also deliver other malicious code as a secondary payload, the analysts note (see: Qbot Banking Trojan Now Deploying Egregor Ransomware).
Once deployed, SystemBC gathers basic information about the device, such as the active Windows username, the build number of the compromised system and whether the operating system is 32- or 64-bit, according to the report. The malware also connects to a command-and-control server over the Tor network and allows the attackers to send additional commands and scripts.
"The operators of the bot can use the command-and-control server to send a number of payloads back to the infected system for execution," according to Sophos. "SystemBC can parse and execute Exe or [Dynamic Link Library] data blobs passed over the Tor connection, shellcode, VBS scripts, Windows commands and batch scripts, and PowerShell scripts."
The researchers also noted that the ransomware gang combined SystemBC with legitimate but weaponized tools such as Cobalt Strike to move laterally through the networks and maintain persistence, the report notes.
In both cases seen by Sophos, the SystemBC malware allowed the attackers to target as many potential victims as possible by automating parts of the ransomware attack.
"SystemBC is an attractive tool in these types of operations because it allows for multiple targets to be worked at the same time with automated tasks, allowing for hands-off deployment of ransomware using Windows built-in tools if the attackers gain the proper credentials," the threat researchers note.
Ryuk and Egregor
Ryuk and Egregor ransomware attacks have increased significantly this year. The security firm Intel 471 notes that Ryuk might be responsible for one-third of all ransomware attacks over the last 12 months (see: More Ransomware-as-a-Service Operations Seek Affiliates).
Ryuk has also been linked to recent attacks that targeted hospitals throughout the U.S. and Canada in October and the Baltimore County Public Schools system just before the Thanksgiving holiday.
Egregor has been tied to more than 70 attacks worldwide since September, with the majority taking place within the U.S., security firm Digital Shadows reports. Earlier this month, a Canadian public transportation agency and a Dutch human resources and staffing firm were both involved in Egregor attacks (see: Egregor Ransomware Slams HR Firm and Transport Agency).





















