Business Continuity Management / Disaster Recovery , Cybercrime , Fraud Management & Cybercrime
Ransomware Attacks: STOP, Dharma, Phobos Dominate
GlobeImposter 2.0 and Sodinokibi Strikes Also Common, Researchers Find
Nearly two years after cryptocurrency-mining malware displaced ransomware as the chief tool in online attackers' arsenal, ransomware has returned to being the No. 1 threat.
See Also: Cybersecurity for the SMB: Steps to Improve Defenses on a Smaller Scale
In a new report, Europol, the EU's law enforcement intelligence agency, says ransomware is the top online threat that it's tracking. And it expects crypto-locking malware to keep reigning supreme well into 2020 (see: How Cybercriminals Continue to Innovate).
Criminals are launching ransomware attacks using strains that weren't seen even two years ago, the report notes.
Most-Seen Ransomware
For much of this year, the most prevalent types of ransomware seen in the wild have been STOP, variants of Dharma as well as the Dharma-like Phobos, says New Zealand-based anti-virus firm Emsisoft. That's based on 230,000 malware samples spotted by the firm's software from April 1 and Sept. 30, as well as samples sent to the free ID Ransomware service run by Michael Gillespie (@demonslay335), a security researcher at the firm. Uploading a ransom note or encrypted file to the service can help identify it, as well as provide potential decryption or mitigation options.
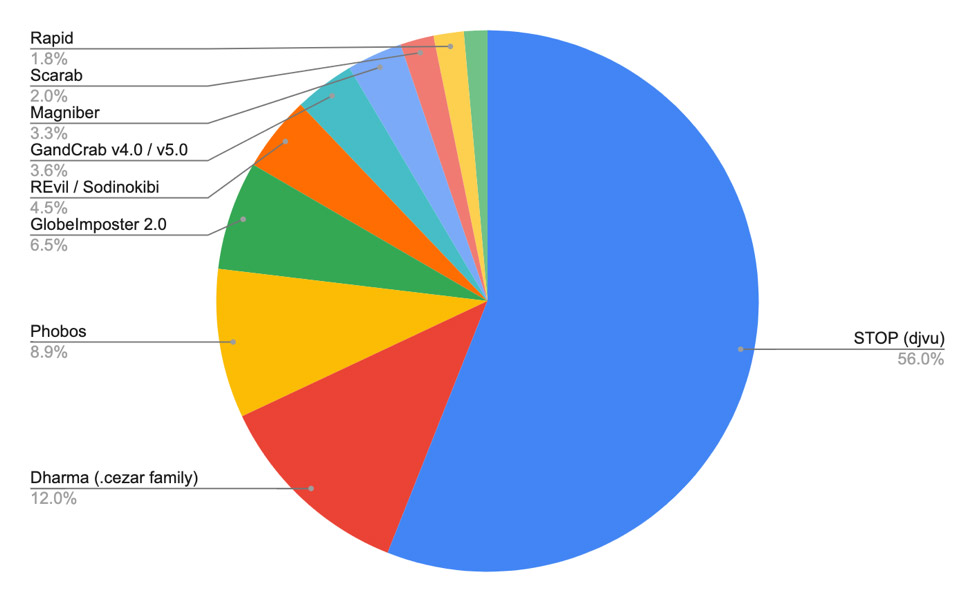
Ransomware is a global phenomenon, with the Emsisoft researchers finding the greatest number of ransomware samples in Indonesia, India, the U.S., Brazil, South Korea and Egypt.
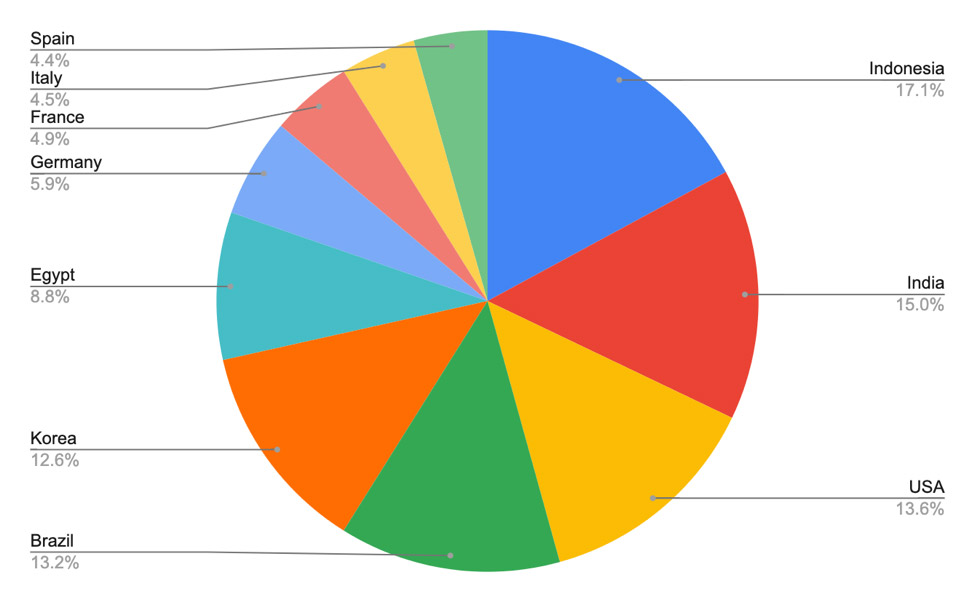
Attackers' targeting tactics have also evolved in recent years. Dharma - of the .cezar family variety - as well as Phobos and Ryuk are among the dominant strains used primarily to extort not individuals but organizations over the past six months, researchers say. "In contrast to the spray-and-pray campaigns of the past, threat actors are increasingly targeting larger and more profitable targets, such as businesses, schools and government organizations," Emsisoft reports in a blog post.
Attackers Seek Extortion Payoff
While the strains in play might change, attackers' use of ransomware as a tool for making a profit continues.
Here's the well-worn MO: Attackers infect one or more systems with crypto-locking malware, then demand a ransom, typically payable in bitcoins, for the promise of a decryption tool. Law enforcement and security experts continue to recommend that organizations maintain offsite backups and fast-restore capabilities, so they never need to consider paying (see: Baltimore Ransomware Carnage Compounded by Local Storage).
If that fails, they may be able to avail themselves of free decryption tools (see: No More Ransom Thwarts $108 Million in Ill-Gotten Profits).
If victims do choose to pay, however, they may discover that even if they receive the promised decryption tool, not all files may be restorable.
Top 5 Ransomware Strains
Over the past six months, Emsisoft says, these have been the five most-seen types of ransomware in the wild.
- STOP, aka DJVU: First spotted in late 2018, this ransomware often gets hidden in adware bundles being distributed via "cracked software" sites as well as torrents. Dozens of STOP variants have been found in the wild. "Once executed, STOP encrypts files with AES-256 encryption and instructs the victims to pay a ransom of $490 worth of bitcoin in exchange for decryptor software and a private decryption key," Emsisoft says. "After 72 hours, the ransom demand doubles to $980. Free decryption tools are available for a limited number of variants, but newer versions cannot be decrypted."
- Dharma (.cezar family): While variants of Dharma have been spotted since 2016, this one appends the extension .cezar to encrypted files, lists no specific ransom amount and is primarily used to target businesses, Emsisoft says. Attackers have been increasingly using this strain of ransomware in recent months, it adds, perhaps "due to threat actors making more effective use of multiple attack vectors such as malicious email attachments, infected installers and weak or leaked remote desktop protocol login credentials." (See: Dharma Gang Pushes Phobos Crypto-Locking Ransomware)
- Phobos: Sharing a name with the Greek god of fear, Phobos first appeared in December 2018 . It closely resembles Dharma, including using nearly the same ransom note, according to ransomware incident response firm Coveware (see: Ransomware Gangs Practice Customer Relationship Management). Phobos often gets distributed via "well worn, open or weakly secured RDP ports," it adds. Like the .cezar variant of Dharma, Phobos ransom notes do not demand a specific amount, but instead instruct victims to email attackers to discuss pricing. "There have been instances of no decryption tool being delivered after payment," Emsisoft warns, noting that businesses and public entities have been particularly targeted by this strain.
- GlobeImposter 2.0: Not to be confused with GlobeImposter or Globe, Emsisoft says this strain uses AES-256 encryption to crypto-lock files and has been seen demanding a ransom amount from 1 to 10 bitcoins ($8,100 to $81,000) in exchange for the promise of a decryptor.
- Sodinokibi: This strain stormed onto the scene after the operators of the prolific GandCrab ransomware-as-a-service offering announced their retirement in May. Like GandCrab, Sodinokibi - aka REvil and Sodin - is supplied to "affiliates" who infect systems with the malware and then share a cut of their proceeds with organizers. Some affiliates specialize in not just hitting individuals or organizations, but also hacking into IT and managed security service providers, allowing them to infect many endpoints across many different organizations at once, as was seen in the attack against 22 Texas municipalities in August (see: Texas Ransomware Responders Urge Remote Access Lockdown).
Ryuk Keeps Bagging Ransoms
While not on the list of the top 10 most-seen ransomware strains over the past six months, Ryuk continues to top earnings charts.
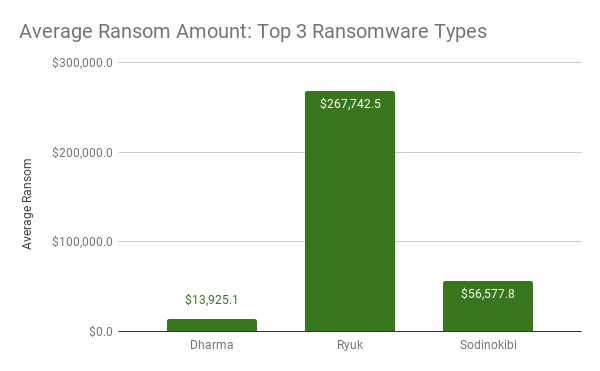
The ransomware has been tied to some pricey ransom payoffs over the last six months, including $600,000 paid by Riviera Beach, Florida, as well as $460,000 paid by Lake City, Florida, among many others (see: More US Cities Battered by Ransomware ).
"Decryption may be possible in a small number of cases," Emsisoft says, saying data recovery appears to work in 3 percent to 5 percent of all cases. "Organizations that have been affected by Ryuk can check if their case is decryptable by submitting a sample to Emsisoft or ID Ransomware," it says.























