Endpoint Security , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Police Bust Five Ransomware Suspects in Romania
Suspects Accused of CTB Locker, Cerber Ransomware Attacks Against US and Europe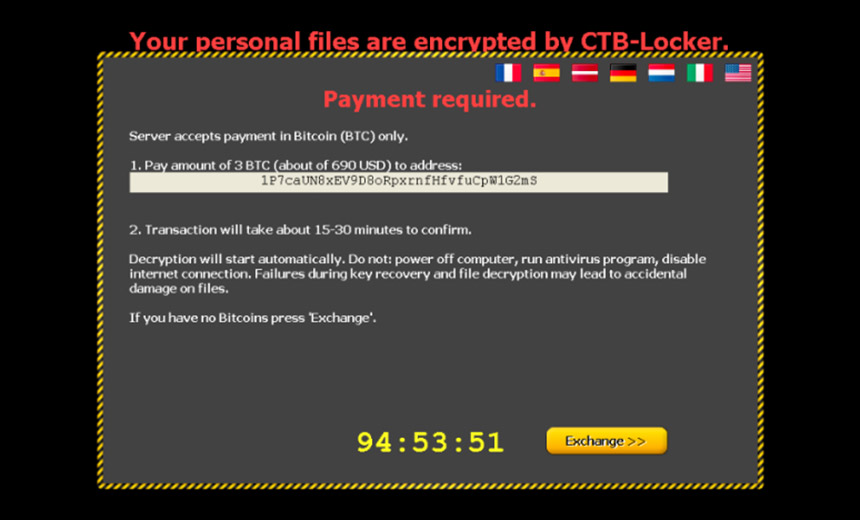
European police have arrested five individuals on suspicion of launching attacks that use crypto-locking ransomware.
See Also: Break the Attack Chain with XDR
As part of what authorities have dubbed operation "Bakovia," authorities in Romania have arrested three individuals on suspicion of infecting systems with ransomware called CTB Locker, aka Curve-Tor-Bitcoin Locker and Critroni, says Europol, the EU's law enforcement intelligence agency.
Police searched six houses and seized a number of laptops, hard drives and other external storage devices, SIM cards as well as cryptocurrency mining rigs.
As part of the investigation, police say they also arrested two suspects from the same criminal group in the Romanian capital of Bucharest on suspicion of infecting U.S. systems with Cerber ransomware. Europol says the U.S. Secret Service was running a separate investigation into the Cerber attacks that has since been merged with the CTB locker thanks to Romanian police locating the two suspects.
"After the U.S. authorities issued an international arrest warrant for the two suspects, they were arrested the day after in Bucharest while trying to leave the country," Europol says.
The suspects have not been accused of developing their own ransomware. Instead, they're accused of procuring it from developers via a ransomware-as-a-service arrangement that requires "affiliates" who use the software to remit about 30 percent of their profits to the developers. This approach can give even technically unsophisticated attackers access to the latest attack tools (see Cybercrime-as-a-Service Economy: Stronger Than Ever).
Operation Bakovia involved a joint investigation conducted by the Romanian Police Service for Combating Cybercrime, the Romanian and Dutch public prosecutor's offices, Dutch National Police, the UK's National Crime Agency and the FBI, assisted by Europol's European Cybercrime Center, EC3, as well as the Joint Cybercrime Action Taskforce, or J-CAT.
Spam Delivers Ransomware
Europol says the Dutch High Tech Crime Unit and other authorities alerted Romanian police early this year that they'd identified a group of Romanian nationals who were sending spam messages. "This spam was specifically drafted to look like it was sent from well-known companies in countries like Italy, the Netherlands and the U.K.," Europol says. "The intention of the spam messages was to infect computer systems and encrypt their data with the CTB locker ransomware."
The ransomware took the form of an attachment, often disguised to resemble an archived invoice. Opening the attachment on a Windows system could then enable the malware to execute and begin crypto-locking files on the victim's system.
Security firm McAfee assisted in the investigation. "Emails in Dutch seemed to originate from one of the largest telco providers," Christian Beek, lead scientist and principal engineer in the McAfee's Office of the CTO, and Raj Samani, McAfee's chief scientist, write in a Wednesday blog post. "The emails claimed to have the latest bill attached. There was no bill, of course, rather CTB Locker asking for around $400 of ransom to return files. The grammar and word usage was near perfect - not what we commonly observe - and the names in the email were proof of a well-prepared campaign."
Dutch authorities alone logged more than 200 successful infections in the Netherlands due to this campaign.
CTB Locker Teardown
McAfee says CTB Locker was one of the world's three most common ransomware families in 2015 before becoming top dog in 2016 after a coordinated law enforcement effort, Operation Tovar, disrupted the infrastructure responsible for spreading CryptoLocker.
"CTB Locker and CryptoWall malware families helped to fill the gap," Beek and Samani say in a blog post.
CTB Locker was among the first types of ransomware to use Tor to disguise communications between infected endpoints and command-and-control servers. The malware can infect numerous versions of Windows, including XP, Vista, 7 and 8. After infecting a system, the ransomware crypto-locks many different file types on a PC, including documents as well as photo, music and video files (see FBI Warning: Ransomware Is Surging).
In mid-2014, McAfee says the malware authors began advertising their wares on underground forums, including the ability to purchase the code for $3,000.
"The authors also offered an affiliate program, which made CTB Locker infamous," Beek and Samani say. "By sharing a percentage of the received ransoms, the affiliates ran the greater risk - because they had to spread the ransomware - but they also enjoyed the higher profits. By using exploit kits and spam campaigns, the malware was distributed all over the world, mostly targeting 'Tier 1' countries, those in which the victims could afford to pay and most likely would pay the ransom."
Recommendation: Never Pay
Authorities recommend that all PC users run up-to-date anti-virus software with the latest signatures and keep up-to-date and offline backups of their data in the event that they become infected with ransomware. Having backups means that affected individuals and organizations can restore their data without having to consider paying a ransom to attackers (see Please Don't Pay Ransoms, FBI Urges).
If systems do become infected, the No More Ransom project maintains free decryptors for some types of ransomware (see Two New Ransomware Decryptors Give Victims a Free Out).




















