Fraud Management & Cybercrime , Fraud Risk Management , Next-Generation Technologies & Secure Development
Phishing Kit Can Change Lures and Text
Researchers: 'LogoKit' Found on 700 Domains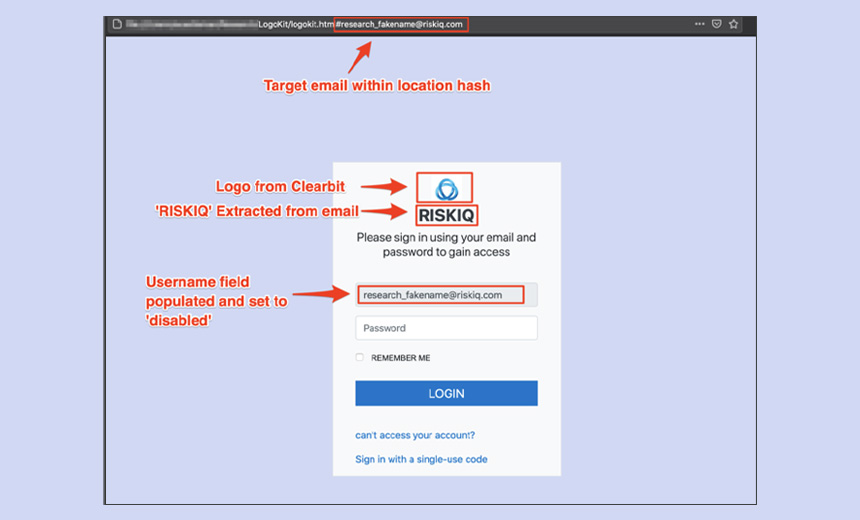
Researchers at the security firm RiskIQ have discovered a phishing kit they call "LogoKit" that fraudsters can use to easily change lures, logos and text in real time to help trick victims into opening messages and clicking on malicious links.
See Also: Is Your Email Security Keeping Up with Attackers? Protecting your Microsoft 365 Investment
RiskIQ has spotted LogoKit running on 700 domains over the last month. Analysts are tracking hackers that are likely selling and distributing the kit through underground forums to other cybercriminal gangs, says Adam Castleman, a threat researcher at the security company.
Unlike other phishing kits that use static templates to spoof brands and services, LogoKit offers fraudsters a way to tailor their attacks to specific individuals and change the look of the domain or the messages in the phishing email.
"What sets LogoKit apart is the use of legitimate object storage services to host the pretext pages and JavaScript code to then pass credentials to an attacker-controlled domain," Castleman says. "The ability to actively change logos based on the target allows an attacker to reuse the same pretext on other targets without any changes to the overall phishing page."
In recent weeks, LogoKit has been used to create generic login portals for phishing attacks and malicious domains designed to spoof brands and services, such as Microsoft SharePoint, Adobe Document Cloud, OneDrive and Office 365, as well as cryptocurrency exchanges, according to RiskIQ.
How LogoKit Works
LogoKit offers an embeddable set of JavaScript functions designed to interact within the Document Object Model, which is a website's presentation layer, the researchers say.
"Integrating with the [Document Object Model] allows for the script to dynamically alter the visible content and HTML form data within a page, all without user interaction," the report notes. "This capability gives attackers a wide range of options for visually deceiving their victims by easily integrating it into existing HTML pretext templates or building fake forms to mimic corporate login portals."
Fraudsters using LogoKit can send victims a personalized, specially crafted URL containing their email address as part of the initial phishing email. If the recipient clicks on the link in the message, the kit will fetch a company or brand logo from a third-party service, such as Clearbit or Google's favicon database, to ensure that it appears authentic, RiskIQ notes.
"The victim email is also auto-filled into the email or username field, tricking victims into thinking it's a familiar site they've already visited and logged into," according to the report.
If victims enter their credentials or other data into the domain, LogoKit then performs an AJAX request that sends that information to the fraudster's command-and-control server before redirecting the user to the corporate website they intended to visit when clicking the URL, the report notes.
"LogoKit versions will play additional tricks, such as telling a user that their password is incorrect and prompting them to enter the password again," the RiskIQ report adds. "Another AJAX request can then perform new tasks, such as sending the credentials to the attacker's email."
Phishing Kit Market
An April 2020 report from security firm Group-IB found that the average price of a phishing kit on underground forums in 2019 was $304, with the prices generally ranging between $20 and $880.
The price for phishing kits varies based on their complexity (see: Demand for Phishing Kits Is Strong: Report).



















