Cybercrime , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Phishing Campaign Uses Outlook Migration Message
Researchers: Campaign Looks To Harvest Users' Office 365 Credentials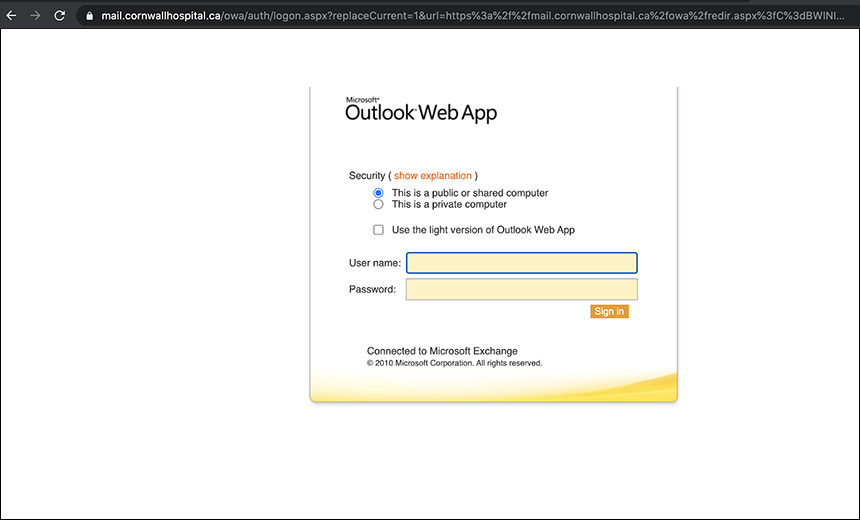
An ongoing phishing campaign designed to harvest Office 365 credentials is using a Microsoft Outlook migration message, according to researchers at Abnormal Security.
See Also: Combating Cyber Fraud: Best Practices for Increasing Visibility and Automating Threat Response
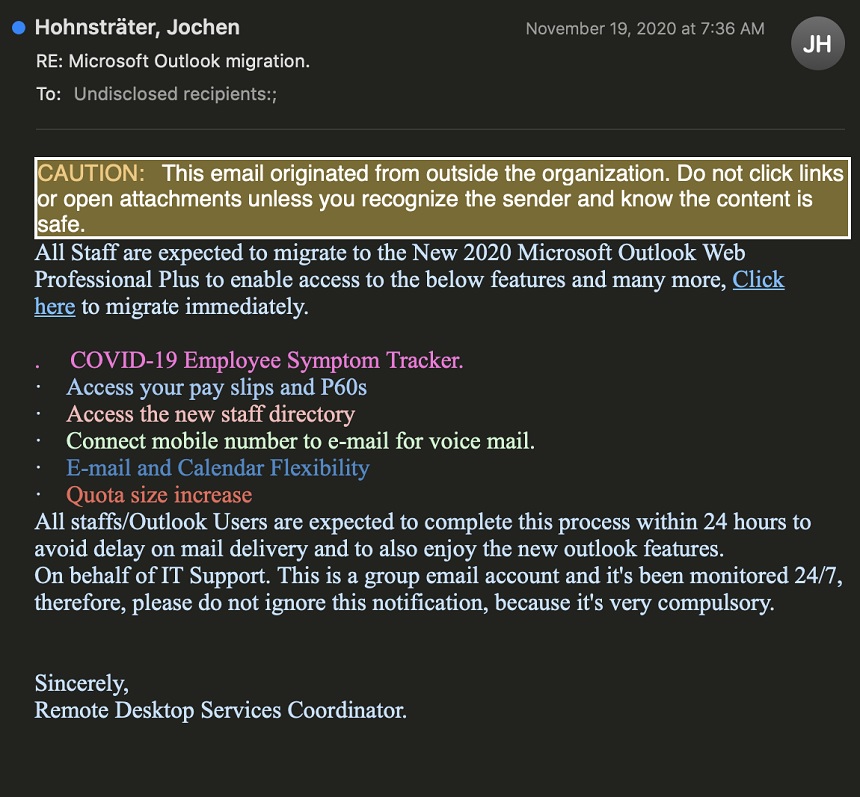
The phishing emails, which are designed to look as if they come from the IT department of the victims' organizations, say the recipient must update to the latest version of Microsoft Outlook, according to the report.
When victims click a link within the phishing email, they are directed to a malicious domain that shows an older version of the Outlook sign-up page that’s designed to steal credentials, such as usernames and passwords, the researchers note.
"If the login page is filled out, the attacker will now have access to any platform that uses the victim’s Microsoft credentials," according to the report.
The Abnormal Security researchers note that phishing emails, written in English or German, have landed in about 80,000 inboxes so far.
"The attacker says that the recipient has 24 hours to complete the 'migration,'" the Abnormal Security report notes. "Attackers know that they are more likely to see success when creating a sense of urgency on the part of the recipient: Moving quickly means that recipients will let their guard down and are less likely to inspect emails for any red flags."
COVID-19 Lure
In addition to the Microsoft Outlook migration theme, the campaign uses the COVID-19 pandemic as a lure to get more recipients to click the malicious link, the report says.
"The attack leverages the COVID-19 pandemic by mentioning a new 'COVID-19 Employee Symptom Tracker' to incentivize concerned recipients to click on the link," the researchers note.
Other Office 365 Attacks
In November, Microsoft's Security Intelligence team warned Office 365 users about a phishing campaign that appeared to be harvesting victims' credentials (see: Microsoft Warns of Office 365 Phishing Attacks).
In September, Microsoft provided additional details about how a hacking group affiliated with Russian military intelligence was attempting to harvest Office 365 credentials associated with election campaigns in the U.S. and U.K (see: Russia-Backed Hackers Try to Harvest Office 365 Credentials).
In that same month, the U.S. Cybersecurity and Infrastructure Security Agency issued a report describing how a threat actor used a well-known VPN vulnerability and compromised Office 365 credentials to gain administrative privileges to a federal agency's network (see: Federal Agency Hacked Using Stolen Office 365 Credentials).
Phishing attacks targeting Office 365 have increased significantly since the start of the COVID-19 pandemic, according to Microsoft. In September, the company reported that, in the first half of 2020, its researchers saw an approximate 35% increase in total attack volume compared to the second half of 2019.





















