Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Personal Data of 120,000 Russian Soldiers Published Online
Dataset Includes Names, Registration Numbers and Army Unit Details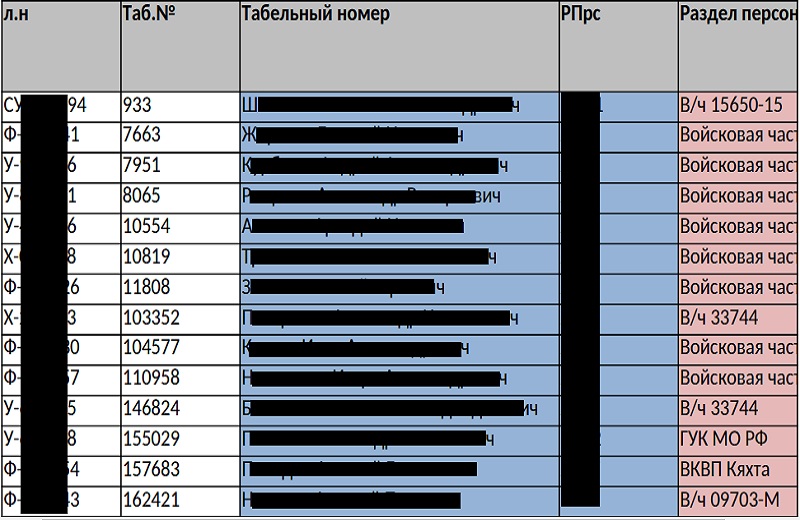
Ukrainian online newspaper Pravda has published what it says are details on 120,000 Russian soldiers, citing Ukraine's Center for Defense Strategies as the source. But chatter seen by Information Security Media Group on Telegram suggests that the source of the dataset is the hacker group ENIGMA.
See Also: 2018 Banking Threat Landscape: An Inside Look at How Cybercriminals Target Financial Services
The dataset was shared on the hacker group's Telegram channel "E_N_I_G_M_A." According to Telegram, the channel was created on Dec. 30, 2021. The data was published in two parts and presented in an Excel sheet.
Part 1
The first part was published on Feb. 10. The 3.1MB file contains personal data of 22,713 Russian soldiers. The Telegram post says, "Despite the fact that the Russian military is trying to be very careful and diligently conceal its involvement in the fighting in eastern Ukraine, they still leave traces and come into view. At the moment, we are publishing the first part of the Russian military personnel."
Part 2
The second part was published on Feb. 14. The 14.5MB file contains personal data of 97,266 Russian soldiers. The hacker group says it published the dataset because of "the destruction of freedom of speech, repression against the opposition, usurpation of power, external aggression, occupation and annexation of foreign territories, mass killings, ethnic cleansing and numerous war crimes [that] Putin's Russia is associated with today."
Dataset Details
Information Security Media Group viewed the datasets shared by the news agency and the hacker group, and they matched, but no connection between the Center for Defense Strategies and ENIGMA has been established, yet. The leaked dataset includes the following:
- Full names;
- Registration numbers;
- Details of the army unit including name, rank and unit numbers, in some cases;
- Passport details;
- Birthdates.
The leaked data has not been verified by Pravda Ukraine, but according to its article, "the Center for Defense Strategies has acquired [it] from reliable sources" and it belongs to the Russian soldiers "who are fighting the war" in Ukraine.
The news of the dataset being leaked online was highlighted when Thomas Rid, a political scientist who specializes in the risks of information technology in conflict, tweeted about it.
Just wow wow wow. The Ukrainian newspaper Pravda leaked what appear to be personal data of 120,000 Russian soldiers fighting in Ukraine — if confirmed as accurate, we're probably looking at one of the best-timed and most devastating leaks of all time https://t.co/LN9ei2RPUF
— Thomas Rid (@RidT) March 1, 2022
Rid compares the volume of data with that of Edward Snowden's findings (Snowden is the ex-NSA employee who famously leaked highly classified information in 2013). Rid analyzed the dataset shared by Pravda Ukraine and says the leak also exists in an Exchangeable Image File Format - or EXIF - that shows the creation and modification dates from April and June 2021 and contains a file that dates back to 2006. This raises speculation that although the dataset is legitimate, it may include data of past Russian soldiers as well as of those involved in the current conflict.
EXIF is a standard that defines specific information related to an image or other media captured by a digital camera. It is capable of storing such important data as camera exposure, date/time the image was captured and even GPS location, under certain conditions.
The Impact
Citing the chapter "The Book War" in his active measures section, Rid says that it is important to note that leaking lists of names of covert personnel is not new. "A leak of personnel names has a powerful psychological effect on the organization in question. It creates an acute sense of vulnerability, in a very personal way, for those in charge, and for those exposed," Rid says on Twitter.
He also says that such a leak creates a dilemma for leadership: "Do you tell your own people that they have been doxed, so they won't learn about it from social media, press, or families, and embarrass yourself now - or do you not tell them, and embarrass yourself later."
Brian Higgins, a security specialist at Comparitech, tells ISMG, "Sowing ideas of vulnerability in enemy troops is a standard military technique. The difference here is that cyberwarfare is a relatively untested phenomenon. It's no secret that critical national infrastructure can be vulnerable to cyberattacks during times of conflict, but modern cyberwarfare encompasses civilian assets as well. Social media, communications networks, utilities, payment/financial systems, etc., can all be leveraged to apply pressure and demoralize opposing forces and populations."
Old or New Dataset?
Rid's tweet caught the eye of Christopher Ahlberg, the CEO and co-founder of cybersecurity firm Recorded Future. He retweeted it and said, "If this is true it's the most epic hacktivism/doxxing ever."
Using the resources available at Recorded Future and Gigasheet, Ahlberg analyzed the leaked dataset and, a few hours later, said what he thinks the list contains:
Hot take: Analysis of 90,000 of the soldiers in the Ukrainska Pravda leak, done with @RecordedFuture and @gigasheet. Most of high count units are Motor Rifle Brigades (makes sense). Some of them are verified to be in region (e.g В/Ч 46108). Does not mean individual soldiers are. https://t.co/QRAYXhUG6n pic.twitter.com/x2k1SEPNJ2
— Christopher Ahlberg (@cahlberg) March 2, 2022
Ahlberg was able to analyze and confirm only 90,000 entries of the leaked data dump, citing an issue with the "file structure." But from the data he analyzed, Ahlberg confirmed Rid's findings regarding the data being an old list and said, "Could be an [old] collection of infantry/mech unit soldiers and given 75% of Russian army in region, random match is not crazy."
Higgins says, "It's doubtful this particular leak relates to any personnel currently involved in the conflict, but it is certainly an indication that cyberattacks may appear more frequently from now on."
Did Ukraine Cross the Line?
Russia has been known to conduct offensive cyber operations and even has the support of ransomware groups such as Conti. But Mendy Kupfer, the CEO of Gigabit Systems, says he has mixed feelings about whether Ukraine crossed the line by leaking sensitive data on adversary personnel. He asks, "How much is too much?"
"Is sharing personal information about soldiers ok, even during war? I am very aware that Russia is tied to some of the most advanced and ruthless hacks, cyberattacks, and ransomware attacks that the country has ever seen. It has stolen countless amounts of data and extorted billions of dollars in ransom payments. But I know that if this happened to American troops, I would not be ok with this," Kupfer says in a LinkedIn post.






















