Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
Okta, Microsoft Confirm Breaches Connected to Lapsus$ Hack
Okta Is Facing Increasing Pressure to Release More Details
Identity management company Okta and Microsoft have confirmed breaches by the Lapsus$ group, which has been on a high-profile hacking spree.
See Also: The State of Organizations' Security Posture as of Q1 2018
Microsoft saw some of its source code released after Lapsus$ compromised an account, but it says that the code isn't sensitive. Okta says that attackers in January gained access to a support engineer’s laptop for five days, which resulted in the exposure of data for some of its customers.
Lapsus$ has been behind a number of recent incidents, including supposed breaches of LG, Nvidia and Samsung.
On Tuesday, images allegedly stolen from Okta appeared on a Telegram page apparently run by Lapsus$. Subsequently, however, Lapsus$ revised the contents of the page to instead claim that "we did not access/steal any databases from Okta - our focus was only on Okta customers."
The crime group claimed to have gained "superuser/admin" access to multiple systems used by Okta.
Later in the day on Tuesday, Okta released an updated statement, saying about 2.5% of its customers may have been affected but did not give a precise figure. It said the data of those customers "may have been viewed or acted upon."
The Okta breach has raised alarm across the security community. Okta's authentication and identity management software is widely used by enterprises. Some have called on Okta to be more transparent about the incident and its possible effects.
Okta spokesman Chris Hollis tells Information Security Media Group that in late January, "Okta detected an attempt to compromise the account of a third-party customer support engineer working for one of our sub-processors."
"The matter was investigated and contained by the sub-processor," Hollis says. "We believe the screenshots shared online are connected to this January event. Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January."
Okta declined to comment on how an attacker might have compromised one of its contractors, or its identity.
Forbes, however, reports that the breached contractor was Sykes Enterprises, which provides customer services for Okta from Costa Rica. Sykes Enterprises did not immediately respond to ISMG's request for comment.
Security researcher Bill Demirkapi, who works in offensive security at Zoom, says it is possible that Lapsus$ might have gained access by using Okta's own remote-control tooling, which may be used to monitor contractors' activities. The screenshots appear to show a user who is actively logged in.
"It would explain things like why the Chrome browser is signed in to a user," Demirkapi says.
List of Potentially Affected Customers
One of the screenshots shared by Lapsus$ indicates that affected downstream customers may have included Atlassian Jira, Amazon Web Services, Google's Gmail, Salesforce, Splunk and Zoom. The attacker also appeared to have the ability to change some passwords.
Atlassian, in a statement to ISMG, says it does not currently use Okta as an identity provider. "While Lapsus$ may have been able to access Okta’s internal Atlassian products, Atlassian has found no evidence of a compromise to our systems or cloud products," a spokesperson for the company says.
The other potentially affected companies did not immediately respond to Information Security Media Group's requests for comment.
Some screenshots published by Lapsus$ indicate that Cloudflare, which uses Okta's services, could be affected.
"We've confirmed no compromise," says Cloudflare CEO Matthew Prince. But "out of abundance of caution," the company has chosen to reset the password for any employee who changed their Okta password in the past four months.
On Tuesday, Cloudflare published a blog post detailing how it uses Okta and the steps it took to address the impact of the compromise. The post also offers mitigation advice to other Okta customers.
We are resetting the @Okta credentials of any employees who've changed their passwords in the last 4 months, out of abundance of caution. We've confirmed no compromise. Okta is one layer of security. Given they may have an issue we're evaluating alternatives for that layer.— Matthew Prince (@eastdakota) March 22, 2022
Microsoft Confirms Breach
Hours before the claimed Okta breach came to light, Lapsus$ released on Telegram what it claims is the source code of products belonging to Microsoft.
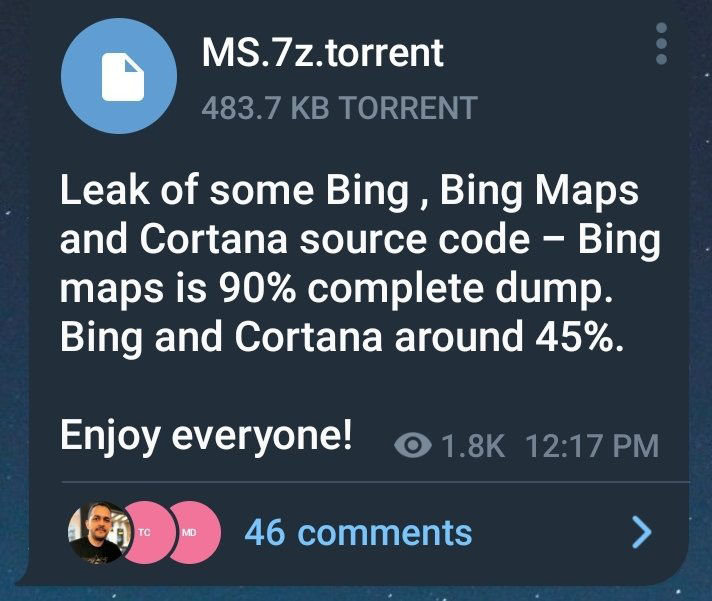
"Leak of some Bing, Bing Maps and Cortana source code - Bing Maps is 90% complete dump. Bing and Cortana around 45%. Enjoy everyone!" the message reads.
Lapsus$ on Sunday also posted and later deleted what appeared to be an Azure DevOps repository containing source code for Cortana and Bing projects.
Late Tuesday, Microsoft told ISMG that its investigation did find an account that had been compromised, which granted limited access. "Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity," a spokesperson says.
The release of the source code "isn't tied to elevation of risk," Microsoft says. The company says it doesn't rely on keeping code secret as a security measure.
Also on Tuesday, Microsoft published an in-depth blog post on Lapsus$, which it calls DEV-0537. Microsoft say the group doesn't deploy ransomware but rather employs "a pure extortion and destruction model."
How Group Publicizes Victims
Lapsus$ uses its Telegram channel to broadcast victims' identities and try to recruit insiders to infiltrate companies in return for a cut of the proceeds, says Chris Morgan, a senior cyberthreat intelligence analyst at threat intelligence firm Digital Shadows.
"Most extortion groups - primarily ransomware groups - set up their own data leak website on The Onion Router network - aka Tor - for data leaking purposes. This comes with its own risks and limitations, such as being targeted by law enforcement and being exposed to a limited audience of users who know how to navigate Tor," Morgan says.
"Abusing a legitimate tool like Telegram ensures the Lapsus$ data leak channel on Telegram will see limited disruption and that their victims' identities can be exposed to anyone with an internet connection," he says. "Lapsus$ also run polls on their data leak channel, providing members with the ability to decide whose data should be breached next; among cyber extortion groups, few also involve their followers or the public in such a direct manner."
Okta's Explanation
On Monday, Okta detailed the results of a forensic investigation it had commissioned from a third party, which it says was completed this week. But some are calling for Okta to give a fuller account of the impact of the incident.
In a blog post, David Bradbury, CSO at Okta, says:
"In January, Okta detected an unsuccessful attempt to compromise the account of a customer support engineer working for a third-party provider. As part of our regular procedures, we alerted the provider to the situation, while simultaneously terminating the user's active Okta sessions and suspending the individual's account. Following those actions, we shared pertinent information (including suspicious IP addresses) to supplement their investigation, which was supported by a third-party forensics firm.
"Following the completion of the service provider's investigation, we received a report from the forensics firm this week. The report highlighted that there was a five-day window of time between Jan. 16 to 21, where an attacker had access to a support engineer's laptop. This is consistent with the screenshots that we became aware of yesterday.
"The potential impact to Okta customers is limited to the access that support engineers have. These engineers are unable to create or delete users, or download customer databases. Support engineers do have access to limited data - for example, Jira tickets and lists of users - that were seen in the screenshots. Support engineers are also able to facilitate the resetting of passwords and MFA factors for users, but are unable to obtain those passwords."
Okta says its investigation remains ongoing.
Lapsus$, in an updated statement posted at 6:31 p.m., PDT on Tuesday, refuted some of Okta's statements.
Saying that the compromise attempt was indeed successful, the threat actor says: "Logged in to superuser portal with the ability to reset the Password and MFA of ~95% of clients isn't successful?" Further debasing the company, the threat actor says that "for a company that supports zero trust, support engineers seem to have excessive access to Slack…," adding that it was also "rather a bad security practice to store AWS keys in Slack channels."
Addressing Okta's statement that the potential impact of the breach was limited, the threat actor says: "I'm pretty certain resetting passwords and MFA would result in complete compromise of many clients systems."
Executive Editors Mathew Schwartz and Jeremy Kirk contributed to this story.
The story has been updated to include new statements from Okta, Microsoft, Lapsus$ and Atlassian.