Cybercrime , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks
North Korean Hackers Tapping Into TrickBot: Report
Researchers See Connections Between Lazarus Group and Crimeware Developers
Hackers linked to the North Korean government are now renting the botnet created by TrickBot malware, as well as access to a highly customized malicious framework, to help further their goals - including targeting payment systems. So says a new report from SentinelLabs.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
The report also points to growing cooperation among hackers backed by nation-states and cybercriminals, resulting in sharing data and profit.
The growing sophistication of crimeware and the ability of nation-state hackers to tap into these resources should make CISOs rethink their security defenses, Vitali Kremez, the head of SentinelLabs - the research arm of SentinelOne - tells Information Security Media Group.
"The maturity of the crimeware models and convergence of threats force us to rethink our defense focusing on how to thwart not only the most sophisticated threats but also crimeware threats that might mature into APTs," he says.
Blurring Lines
In another recent example of the blurring of the lines between cybercrime and nation-state attacks, the U.S. Department of Justice charged two Russian nationals, Maksim Yakubets and Igor Turashev, earlier this month with developing the notorious Dridex banking Trojan, which is believed to have helped the two steal more than $100 million from U.S. banks. Federal prosecutors believe that Yakubets now works with Russian intelligence and shares data that his malware takes from victims' devices (see: Two Russians Indicted Over $100M Dridex Malware Thefts).
"Many cybercrime groups try to achieve 'greatness' and earn millions. but only a few reach the level of Dridex and TrickBot," Kremez says. "The research demonstrates that the most sophisticated criminal groups get entangled with the nation-state actors - either it be the Dridex 'Evil Corp' and Russian [intelligence] and the TrickBot criminal enterprise with the North-Korean Lazarus Group."
TrickBot for Sale
SentinelLabs researchers say that the Lazarus Group, the advanced persistent threat group idely believed to be linked to the North Korean government, has been renting both the botnet created by the TrickBot malware as well as a customized framework developed by the criminal gang that oversees the TrickBot operation.
Since it was first developed in 2016, TrickBot has morphed from a banking Trojan into a versatile malware strain with worm-like capabilities that can act like a botnet, according to security researchers. It also has the ability to act as a dropper, meaning that after gaining a foothold on an infected system, it can install or "drop" additional malware - including ransomware - onto endpoints, as well as push additional functional modules (see: Malware Most Foul: Emotet, Trickbot, Cryptocurrency Miners).
The TrickBot gang has also created a crimeware-as-a-service model, renting out its capabilities to other cybercrime gangs and now hackers backed by nation-states, the SentinelLabs researchers note.
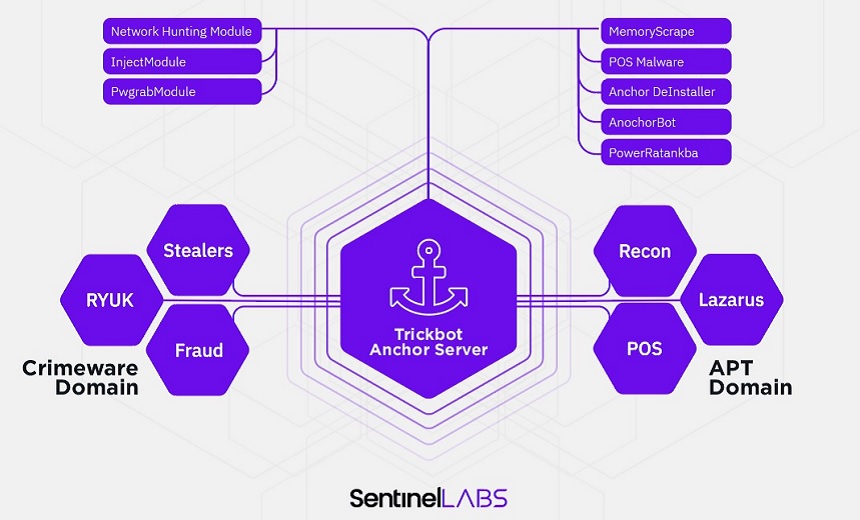
SentinelLabs researchers found that the gang behind TrickBot has also developed a new framework called "Anchor" that members of the Lazarus Group have rented out for their own purposes. The North Korean hackers also rented out the botnet created by the TrickBot malware to help better hide their activity, the researchers add.
The Anchor framework is a series of modules and malicious tools that work together to help keep the attackers hidden within an infected network, giving them time to steal data and map the IT infrastructure of the target, according to both the SentinelLabs study and a new report from Cybereason.
The framework is designed to target enterprise-grade systems used by large organizations, according to the SentinelLabs report.
Each of the modules in the Anchor framework has a different purpose. For example, one allows the attackers to persist in an infected network and avoid detection from security software. Another targets point-of-sale devices, while a different tool can scrape RAM memory from card data. Plus, another module has the ability to clean a system after an attack, according to the two reports.
A Dual Mission
The ability for Anchor to target point-of-sale and other payment systems is significant because the Lazarus Group - which also goes by the name Hidden Cobra among other aliases - reportedly has a dual mission of providing cyberespionage capabilities to the North Korean government as well as stealing money to generate financial resources to regime (see: UN Report: N. Korea Targets Cryptocurrency Exchanges, Banks).
"We suspect the end goal of this partnership is financial gain and target payment system intrusion," Kremez says. "The development and control of this 'Anchor' project with high confidence were reserved to the most trusted members of the TrickBot group. Lazarus is likely the user or beneficiary of this project."
The SentinelLabs report does not indicate if the attacks by the Lazarus Group using TrickBot and the Anchor framework have resulted in thefts.
Hackers’ Strategy
As part of their research into Anchor, SentinelLabs found the ties between TrickBot gang and the Lazarus Group.

In the case that SentinelLabs describes, the researchers found that hackers were using the TrickBot botnet and Anchor framework to install PowerRatankba, a specially designed PowerShell backdoor, within the network of an unnamed company. In 2018, several security analysts published reports tying PowerRatankba to the Lazarus Group; it was used to target point-of-sale machines (see: Report: Investigators Eye North Koreans for Exchange Hack).
"The integration of these tools into the Anchor implies that TrickBot was able to overcome the final barrier in integrating different domains into its model," according to the SentinelLabs analysis. "By integrating the [advanced persistent threat] approach to its model, the group turned its enterprise into a holistic ecosystem of cybercrime, becoming an essentially new phenomenon. In this ecosystem, crimeware and APT are no longer siloed; on the opposite, each type of crime creates added value for the other, each becomes a force multiplier."
Other Customers
The SentinelLabs and Cybereason reports leave open the possibility that the gang behind TrickBot and the Anchor framework have other customers besides the Lazarus Group.
In their report, the Cybereason researchers don't name North Korea, but note that a combination of attacks using the TrickBot malware and the new Anchor framework have been targeting financial, manufacturing and retail businesses since early October. In those cases, the researchers note that point-of-sale machines appear to be the main target, with attacks usually starting with a phishing email to gain access to the network.
The SentinelLabs analysis also left open the possibility that other nation-state backed groups could be renting TrickBot and its capabilties.
"The project is used by multiple APT groups. The Lazarus-affiliated deployment seems only one APT customer of their project," Kremez says.




















