Cybercrime , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks
North Korean APT Group Steps Up Espionage Ops in 2021
TA406 Targets Diplomats, Policy Experts, in Asia, UK and US, Researchers Say
North Korea-associated advanced persistent threat group TA406, aka Kimsuky or Thallium, has ramped up its cyberespionage operations in 2021, targeting diplomats and policy experts across Asia, the U.K. and the U.S, according to researchers.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
In the early part of the year, the threat group launched weekly campaigns featuring themes that included nuclear weapon safety, U.S. president Joe Biden, and Korean foreign policy, researchers at security firm Proofpoint say.
The group also "attempted to collect credentials, such as Microsoft logins or other corporate credentials, from the targeted individuals. In some cases, the emails were benign in nature, [but] these messages may have been attempts by the attackers to engage with victims before sending them a malicious link or attachment," the researchers note.
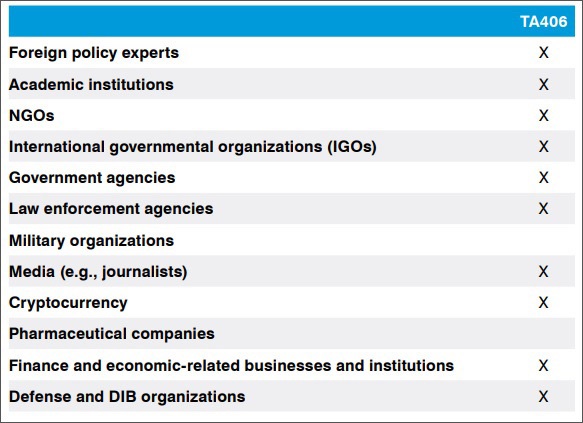
The TA406 group also was involved in frequent credential theft campaigns against research, education, media, finance and nonprofits, the researchers say. The latest addition to this list, they add, is "individuals and organizations related to cryptocurrency for the purpose of financial gain."
History and Traits
The Proofpoint researchers say they consider "TA406 to be one of several actors that make up the activity publicly tracked as Kimsuky, Thallium and Konni Group." While the TA406 APT group has been in operation since at least 2012, the Kimsuky hackers were the subject of a joint alert issued by the FBI and the U.S. Cybersecurity and Infrastructure Security Agency in October 2020, owing to its gradual rise in activity (see: Sizing Up Activities of North Korea's Kimsuky APT Group).
The alert raised speculation about the threat actor having links to the Democratic People's Republic of Korea and being a state-sponsored entity. But Proofpoint's report says that it has "high confidence that TA406 operates on behalf of the North Korean government." It also has linked Kimsuky with two other APTs - TA408 and TA427 - that seem to work in tandem and also share a lot of attack vectors and infrastructure, according to Proofpoint.
The researchers say that TA406 has used spear-phishing campaigns in 2021 to deliver both credential harvesting links and malware such as Konni, Sanny, Carrotbat/Carrotball, Babyshark, Amadey and Android Moez.
TA406 leverages a variety of different messaging platforms in order to carry out its spear-phishing campaigns, including its own infrastructure based on PHP servers, such as PHPMailer and Star, and it uses major service providers, such as GMail or Yandex, along with stolen or synthetic identities to fool targeted individuals, the researchers say.
While many APT groups launch spear-phishing attacks using malicious attachments or fake login pages, TA406 goes one step ahead and creates fake LinkedIn accounts too, the researchers say.
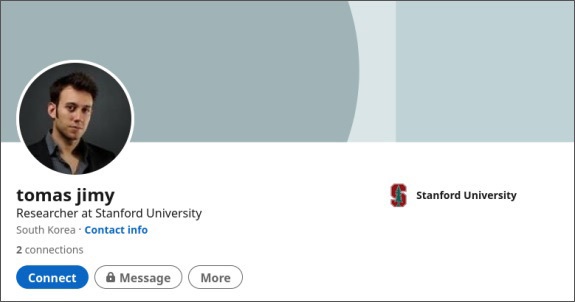
One such LinkedIn account disclosed by the researchers is for “Tomas Jimy,” who the account claims is a researcher from Stanford University. Proofpoint's researchers did not find any physical existence of a person with this name and title.
Other Malicious Tools
In November 2020, researchers at cybersecurity firm Cybereason uncovered a new set of malicious tools tied to the Kimsuky group (see: Additional Hacking Tools Tied to North Korea-Linked Group).
The Kimsuky-linked tools included a modular spyware suite called "KGH_SPY," a malware downloader dubbed "CSPY Downloader," as well as additional infrastructure that overlapped with a previous campaign that targeted a U.S. think tank in 2018, according to the Cybereason report.
In June, researchers at Malwarebytes uncovered another set of tactics, techniques and procedures used by Kimsuky, which was at the time using an AppleSeed backdoor to carry out its espionage operations (see: APT Group Kimsuky Has New Attack Technique, Researchers Say).