Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
New JavaScript Skimmer Found on E-Commerce Sites
Visa Security Researchers Say 'Pipka' Is Good at Avoiding Detection
Security researchers at Visa have uncovered a new type of JavaScript skimmer that has infected the online checkout pages for at least 17 e-commerce websites in an effort to steal payment card data.
See Also: OnDemand | API Protection – The Strategy of Protecting Your APIs
This newly discovered skimmer, dubbed "Pipka," has the ability to remove itself from the HTML of a compromised payment website after it executes, enabling it to avoid security detection, according to the Visa researchers.
The researchers first discovered this skimmer in September after it infected an e-commerce checkout page belonging to a unnamed North American company, according to an alert from Visa. That page had previously been targeted by another JavaScript skimmer called Inter, the Visa researchers say.
After first finding Pipka, the Visa researchers discovered the skimmer on at least 16 other online checkout pages at e-commerce sites. As with other skimmers, Pipka is designed to extract payment card account number, expiration date, card verification value number, cardholder name and address, according to the report.
The creators of Pipka incorporated the self-removal technique as an extra layer of defense against security software. And while this type of avoidance technique has been spotted with desktop malware, it has not been previously incorporated into JavaScript skimmers, says Daniel Munson, a senior analyst with the payment fraud disruption team at Visa.
"The code itself was not taken from any binary malware and was specifically crafted to target e-commerce environments with JavaScript skimming," Munson tells Information Security Media Group. "The technique of self-removal is not new and has been used in binary malware before. However, this is the first time we have seen JavaScript skimming malware employ the self-removal technique, which is what makes it unique."
Rash of Skimmer Attacks
While credit card skimmers generally have relied on hardware installed at the point of sale or in ATMs, the used on malicious JavaScript to skim credit cards from payment sites is a much more lucrative approach and a growing concern for online stores (see: Surge in JavaScript Sniffing Attacks Continues).
These types of virtual skimmers, which are also referred to as JavaScript skimmers, JavaScript sniffers or JS sniffers, can be purchased inexpensively on underground sites.
Munson notes, however, that the Visa researchers have not found evidence that the Pipka malware is available for sale or rent on dark net sites. "The malware was configured consistently across the attacks, and Visa's payment fraud disruption team believes the infections are from a single actor or group of actors," Munson says.
And while Visa hasn't attributed Pipka to a particular cybercriminal group, other security researchers, such as RiskIQ, have attributed the increase in these types of skimming attacks to Magecart, an umbrella organization consisting of about a dozen criminal groups that has been increasingly active over the last year in targeting e-commerce sites to syphon off customer data.
Over the past year, RiskIQ says that 18,000 website domains have been breached using Magecart code.
Some of the major companies targeted by these attacks are British Airways, Ticketmaster and Newegg, researchers say.
In September, a security researcher uncovered credit card skimming attacks targeting websites that use a cloud-based payment platform from Volusion. One of the sites targeted during these attacks is Sesame Street Live, which has a checkout function hosted on the Volusion platform (see: Volusion Payment Platform Sites Hit by Attackers).
Tracking Pipka
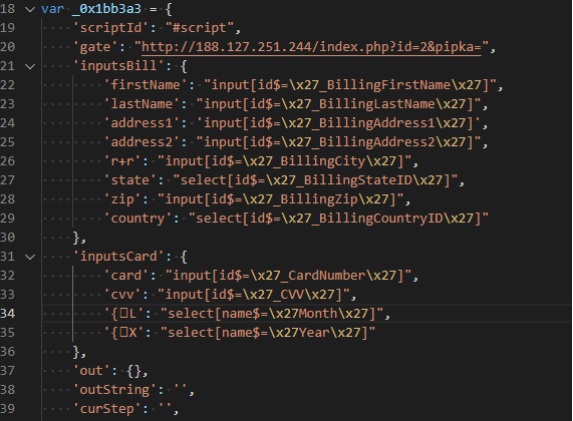
An examination of the Pipka JavaScript code by the Visa researchers shows that its creators are able to configure the malware to target fields in the online checkout page from which they want to extract data from as part of the scam, according to Visa’s security alert.
"The skimmer checks for these configured fields before executing, and in the cases investigated by [Visa], the skimmer is configured to check for the payment account number field," according to the alert.
Once the JavaScript is injected into the payment page, it begins to harvest and copy the data from different form fields. Once that data is gathered, it's encoded and encrypted before being sent to a command-and-control server, the researchers note.
Pipka double-checks the data string before sending the information back to the attackers to avoid sending duplicate data, the Visa research shows.
After the stolen data is uploaded and sent to the command-and-control server, Pipka then activates what the researchers call a "clear" function – a self-cleaning feature that removes traces of the code from the HTML, according to Visa. This makes the skimmer more difficult to detect and remove, the researchers say.
The rapid spread of these skimmers should be a security concern for online merchants, Munson says. "Regional victimology can shift quickly, which is why Visa distributed the security alert about the malware broadly," he says.
Visa suggests e-commerce sites run more frequent checks of their checkout pages to see if any code is attempting to communicate with known command-and-control servers.





















