Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service
'MountLocker' Ransomware Adds to Affiliate Extortion Racket
Researchers: Latest Ransomware-As-A-Service Scheme First Appeared In July
BlackBerry researchers are tracking a relatively new ransomware variant called MountLocker and the operators behind it, who are using affiliate cybercriminal gangs to help spread the malware, exfiltrate data and extort victims, sometimes for millions of dollars.
See Also: Beating the Business of Ransomware
The ransomware was first spotted by BlackBerry's Incident Response Team in July, and its code was updated in November to allow MountLocker to better target certain files and evade security tools, according to the researchers' report.
BlackBerry researchers note that only five victims are listed on MountLocker's "News & Leaks" site hosted on the darknet, but the report warns that its operators and affiliates are poised to expand, and there's likely more victims than currently known.
The operators and affiliates associated with MountLocker are demanding bitcoin from victims, says Tom Bonner, a threat researcher at BlackBerry.
"The MountLocker operators are clearly just warming up," according to the BlackBerry report released Friday. "After a slow start in July, they are rapidly gaining ground, as the high-profile nature of extortion and data leaks drive ransom demands ever higher. MountLocker affiliates are typically fast operators, rapidly exfiltrating sensitive documents and encrypting them across key targets in a matter of hours."
MountLocker
The BlackBerry researchers describe MountLocker ransomware as both lightweight and simply constructed, although its operators are now adding features and becoming more sophisticated, the report notes.
The crypto-locking malware is about 100 kilobytes in size and is typically deployed either as an x86 or x64 Windows portable executable file. It is also distributed as a Microsoft Installer package.
The ransomware also used the ChaCha20 stream cipher for file encryption and RSA-2048 for key encryption, BlackBerry notes. Once initially deployed, MountLocker will try and terminate several security processes, including ones used with applications, databases and web browsers.
"Based on the samples analyzed this is a new malware developed from scratch with no link to defunct families like Maze," Bonner tells Information Security Media Group. "From our analysis, these threat actors are new. This is just the early days of their campaign, and they are improving their toolset as they go based on the fixes they've added in the second version."
The MountLocker ransomware also seeks out a list of over 2,600 file extensions that it will target for encryption, including known file extensions for databases, documents, archives, images, accounting software, security software, source code, games, backups and various custom data formats.
"After initializing the encryption keys, MountLocker will create the ransom note from a template and add the ransomware file extension to the registry. When a user double clicks an encrypted file, the ransom note is opened via Explorer," according to the report. "The file extension is a hex encoded 4-byte (or 8 character) 'Client ID,' which is unique per victim organization."
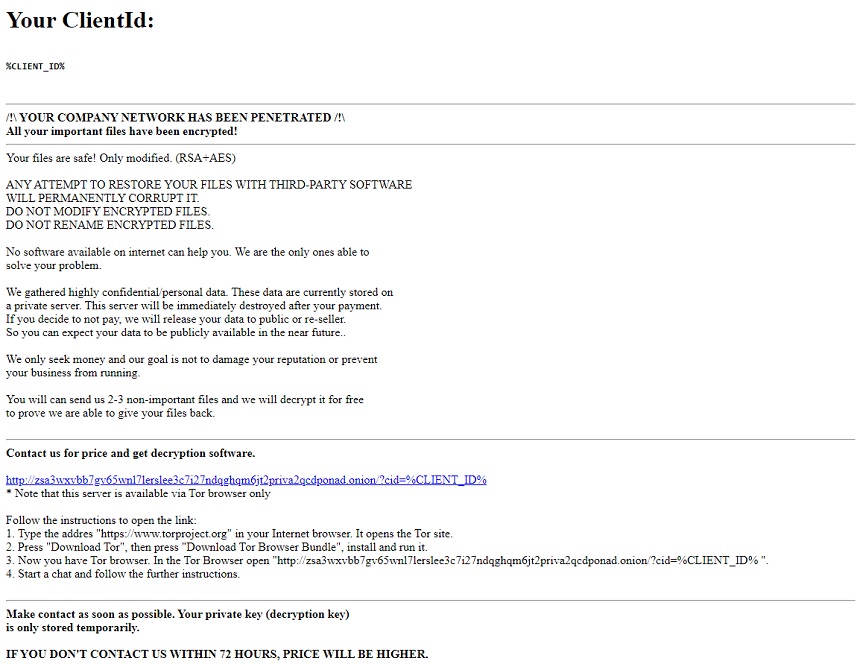
The ransom note sent to victims typically contains an anonymous Tor URL address that allows a victimized organization to contact the attackers through a darknet chat service. On some occasions, the note misstates that AES encryption has been used, the report notes.
Affiliates
As with other types of ransomware-as-a-service schemes, the operators behind MountLocker are relying on affiliate cybercriminal gangs to help target and extort victims and split a share of the profits.
Several security analysts note that these types of RaaS affiliate schemes are now thriving on the darknet as ransomware operators look to cash in on as many attacks as possible. In return, the affiliated gangs can take 30% to 40% of the profits when victims pay (see: More Ransomware-as-a-Service Operations Seek Affiliates).
Operators behind ransomware variants such as DopplePaymer, Netwalker, and REvil all have affiliates working with them, although the now-defunct Maze gang was one of the first to popularize the technique along with creating a darknet "name-and-shame" portal to pressure victims into paying ransoms or have their data released (see: Maze Claims to End Its Ransomware and Extortion Operations).
"Affiliate-powered ransomware was an inevitable evolution of malware. A sophisticated ransomware attack doesn’t just 'happen,'" Mike Weber, vice president of security consultancy Coalfire, tells ISMG. "To successfully execute a ransomware attack, it requires a fairly broad reaching set of skills, just like any business. The model mimics development shops where there's a research and development team, an engineering team, an operations and delivery team, and an accounting team on the backend."
In the case of MountLocker, affiliate gangs are typically using compromised Remote Desktop Protocol connections with stolen credentials to gain access to a device and eventually the network, according to the report.
After the initial compromise, the attackers use legitimate tools such as AdFind, a command-line tool for querying Active Directory, to perform network reconnaissance, and Cobalt Strike, a penetration testing tool, to move laterally and then deploy the ransomware, according to the report.
Victim data is then usually exfiltrated through an FTP server.
In some of the attacks that BlackBerry has documented, the operators of MountLocker or the affiliated gangs have asked for million-dollar ransoms from victims, although it's not clear if any have been paid as of now. This could mean that the MountLocker attackers or their partners aspire to become "big-game hunters," such as the ProLocker gang (see: Operators Behind ProLocker Ransomware Seek 'Big Game').
"Since its inception, the MountLocker group have been seen to both expand and improve their services and malware," the BlackBerry researchers note. "While their current capabilities are not particularly advanced, we expect this group to continue developing and growing in prominence over the short term."