Cybercrime as-a-service , Fraud Management & Cybercrime , Malware as-a-Service
More Ransomware-as-a-Service Operations Seek Affiliates
Lure of Massive Profits, RaaS Newcomers Join Long List of Operators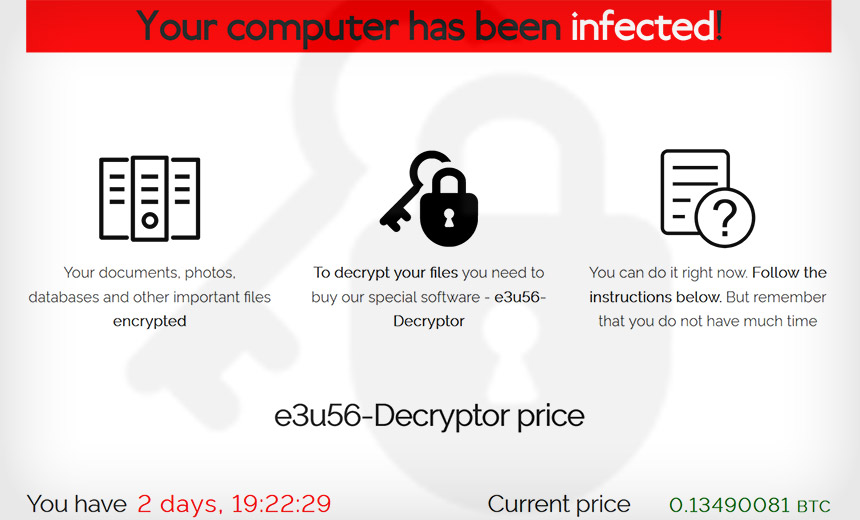
Ransomware developers continue to put highly automated attack toolkits into the hands of criminals, allowing even individuals without advanced technical skills to amass victims.
"The prospect of large profits drives a lot of criminals towards ransomware," says John Fokker, head of cyber investigations and red teaming for McAfee Advanced Threat Research. "Everyone wants a piece of the pie."
Some gangs develop and keep their code in-house. Others, however, offer ransomware as a service, via the cybercrime service economy. But these RaaS offerings have largely shifted over the past five or six years to take a more crowdsourced, profit-sharing approach.
"The older RaaS offerings - such as CTB-Locker - mostly focused on high quantities of infections through botnets, whereas the top-tier RaaS families now select affiliates with a different skillset," Fokker tells Information Security Media Group.
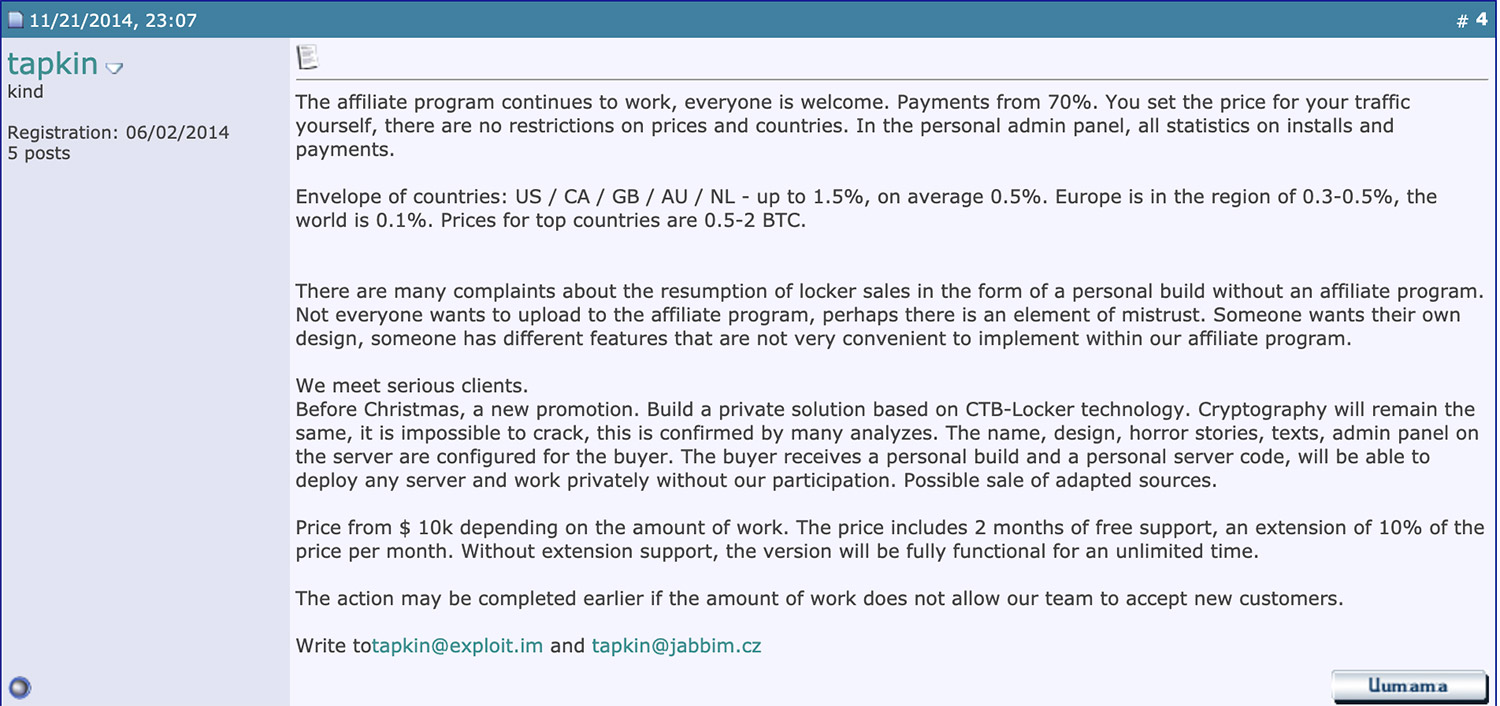
Previously, most RaaS offerings - like malware as a service - involved paying a subscription fee in return for an automated attack toolkit and regular updates.
Today, however, many RaaS affiliates, instead of paying a premium to subscribe, agree to split the proceeds of any ransom that gets paid by a victim. The operator, in return for a 30%, 40% or even 90% cut of every ransom paid, not only maintains the crypto-locking malware - each copy will have a unique ID tied to the affiliate so they can get paid - but also the accompanying infrastructure. This often includes a self-service payment portal for victims to pay their ransom - almost always in bitcoin, but sometimes monero or another more privacy-preserving digital currency - and accompanying "customer support" operations. Many operations also maintain a dedicated blog where non-paying victims can be named and shamed and stolen data leaked to try to make victims pay.
Active RaaS Operations
Which affiliate-driven RaaS operations are most prevalent?
Cybercrime intelligence firm Intel 471, in a new report, says that over the past year, it's been tracking more than 25 RaaS crews, ranging from the most well-known "tier 1" groups, to "tier 2" groups tied "to newly formed variants that have risen from the failures of old," to "tier 3," which it uses to describe "completely new variants that may have the ability to unseat the current top-level cabals."
Tier 1: The Big Players
The largest ransomware operations are often referred to as being "big-game hunters," meaning they regularly seek to take down the largest organizations in return for the potential of earning the biggest possible ransom payoffs.
Intel 471 places five affiliate-driven RaaS operations into this tier, and notes that all have blogs for naming and shaming victims and have earned millions by extorting victims into paying them a ransom. They are:
- DopplePaymer (aka DoppelPaymer): Since its debut in 2019 as an offshoot of the cybercrime operation called Evil Corp, DoppelPaymer - which appears to be a variant of BitPaymer - has hit a number of big targets, including Mexico's state-run oil company Pemex, Chile's Ministry of Agriculture and Germany's Düsseldorf University Clinic, which led to patients having to be rerouted, during which time one of them died. German prosecutors opened a negligent homicide case against the hackers, although they later dismissed it.
- Egregor/Maze: Whether Egregor is the direct successor to - or an offshoot of - Maze remains unclear. But the ransomware has been tied to numerous high-profile attacks, including against Barnes & Noble, Canon USA, Crytek and Ubisoft. Maze is one of the few gangs that attacks victims directly as well as using affiliates. But Intel 471 says the gang has found affiliates to be a much easier and more reliable way to maximize profits.
- Netwalker: Since its debut in September 2019, the operation has become "one of the more prolific affiliate services" that Intel 471 says it's been tracking. The gang has allegedly been tied to at least 25 attacks in the last month alone - including against Michigan State University, which refused to pay. Intel 471 notes that the group's ransomware features two modes: "network mode," which allows the attacker to either hold individual systems or an entire network to ransom, with victims being able to buy decryption keys either for the whole network or specified systems; as well as "individual mode," via which attackers demand a separate ransom for every infected system.
- REvil (aka Sodinokibi): Since debuting in April 2019 - potentially as a GandCrab successor - REvil has become one of the most-seen RaaS variants. Affiliates often bring advanced network penetration skills to bear, with infections traced not just to commonly used remote desktop protocol exploitations but also exploits of unpatched Citrix and Pulse Secure remote-access software.
- Ryuk: "Ryuk has exploded over the past year, responsible for millions of ransomware incidents around the world," and by some estimates, one-third of all ransomware attacks over the last 12 months, Intel 471 notes. The ransomware has often been installed as a final hit following Trickbot and Emotet infections, although more recently seems to be getting delivered primarily via BazarLoader infections.
Ransomware incident response firm Coveware says that of the thousands of cases it investigated from July to September, Sodinokibi was the most prevalent ransomware tied to successful attacks, followed by Maze and Netwalker.
Big Players Recruit Specialists
Increasingly, the bigger ransomware operators also recruit affiliates with specialist skills.
Fokker says skills in high demand include penetration testing - using tools such as Metasploit and Cobalt Strike - as well as the ability to use system administration tools and environments, including network-attached storage and backups - for example, using Microsoft Hyper-V.
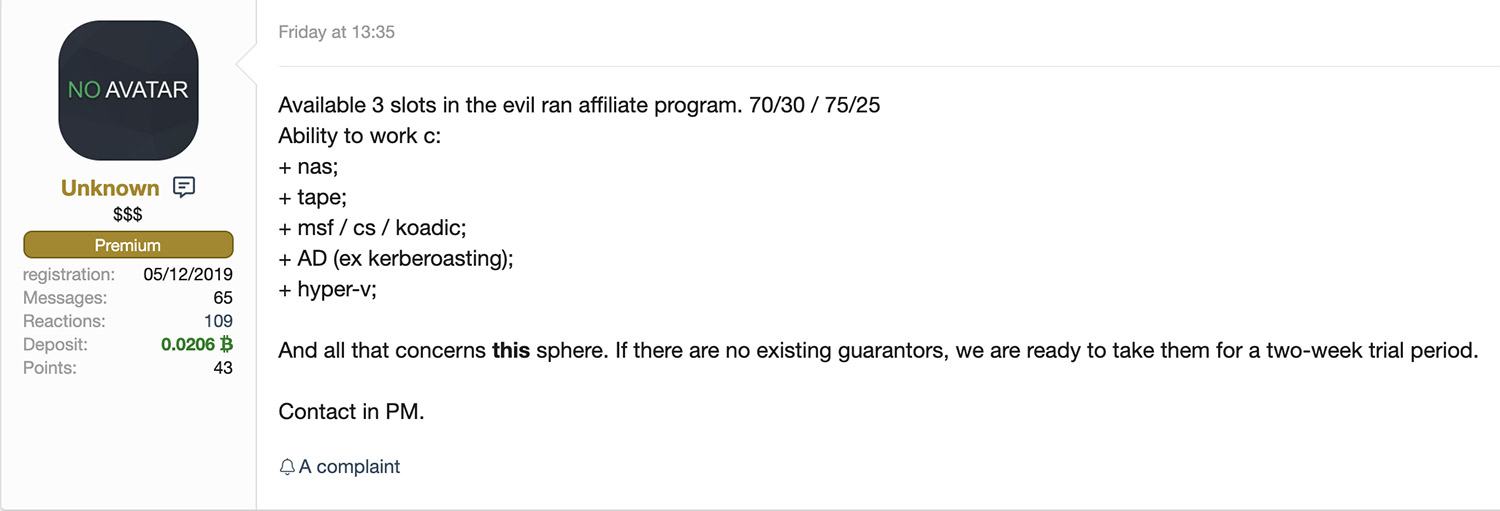
"You can compare it to the regular job market where a company is hiring a new employee who brings in a large network of contacts," he says. "Affiliates that bring in experience or a certain skill to the ransomware group will open up collaboration options. We have seen instances where RaaS operators are opening up slots or seats to new affiliates that are bringing in access to large networks or providing new exploits."
Tier 2: Up and Coming RaaS
Beyond the big players, Intel 471 counts nine mid-level RaaS operations, almost all of which now have name-and-shame blogs to use against non-paying victims. Almost all of these offerings can be procured via various cybercrime markets.
| Name | Date Discovered | Attack claims | Markets Sold | Blog |
|---|---|---|---|---|
| Avaddon | March 2020 | Under 10 | Exploit | Yes |
| Conti | August 2020 | 142 | Private | Yes |
| Clop | March 2020 | Over 10 | n/a | Yes |
| DarkSide | August 2020 | Under 5 | Exploit | Yes |
| Pysa/Mespinoza | August 2020 | Over 40 | n/a | Yes |
| Ragnar | December 2019 | Over 25 | Exploit | Yes |
| Ranzy | October 2020 | 1 | Exploit & XSS | Yes |
| SunCrypt | October 2019 | Over 20 | Mazafaka | Yes |
| Thanos | August 2020 | Over 5 | Raid | No |
Tier 3: RaaS Newcomers
Given the potential profits, new ransomware operations regularly appear, including the following grab bag of 10 RaaS offerings. Intel 471 says that "at the present time, there is limited - to no - information on successful attacks, volume of attacks, payments received or cost of mitigation," for the RaaS affiliate-driven operations in this tier.
| Name | Date Discovered | Notable Incidents | Markets Sold | Blog |
|---|---|---|---|---|
| CVartek.u45 | March 2020 | None | Torum | No |
| Exorcist | July 2020 | None | XSS | No |
| Gothmog | July 2020 | None | Exploit | No |
| Lolkek | July 2020 | None | XSS | No |
| Muchlove | April 2020 | None | XSS | No |
| Nemty | February 2020 | 1 | XSS | Yes |
| Rush | July 2020 | None | XSS | No |
| Wally | February 2020 | None | Nulled | No |
| XINOF | July 2020 | None | Private Telegram channel | No |
| Zeoticus | Dec. 2019 (v1), Sept 2020 (v2) | None | XSS/Private channels | No |
Breaking In
One difference between the different tiers of ransomware operations, beyond the relative profits they see, is who they allow to join their affiliate program.
The operators behind the top-tier ransomware offerings "are definitely much stricter as to who they allow in their crime group," McAfee's Fokker says.
Others apparently can't afford to be too choosy. "We have seen examples of new and upcoming ransomware families being more open to less experienced or professional affiliates just to gain traction and become established," he says.






















