Breach Notification , Cybercrime , Fraud Management & Cybercrime
Maze Ransomware Gang Names More Alleged Victims
Criminals Confirm Florida City of Pensacola Hit, Dump 2 GB of Stolen Data
The gang behind Maze ransomware is continuing to increase the pressure on victims to pay a ransom. Last week, the gang launched a website via which it's trying to name and shame victims, including the Florida city of Pensacola. The site also lists samples of stolen data, and a threat to dump it all online if victims do not pay (see Maze Ransomware Gang Dumps Purported Victim List).
As of Monday, the gang's site listed 21 organizations, all listed as having falling victim to Maze attacks dating from Oct. 21 to Dec. 14. Information Security Media Group is not going to link to the victim-naming site, since it furthers the gang's aims.
But the threat from the gang is clear: Pay up, or we'll make the data we stole publicly available.
That list of Maze ransomware victims now includes Pensacola, which on Dec. 7 announced that it had suffered a crypto-locking malware attack. Subsequently, the Pensacola News Journal reported that the city's infection appeared to trace to Maze ransomware (see City of Pensacola Recovering From Ransomware Attack).
On Sunday, Maze released "proofs" of stolen Pensacola data in the form of two timesheets - in Excel file format - in the name of an individual whose name matches a LinkedIn profile for an employee in the city's human resources department. The files are dated Oct. 21 and Nov. 18. On Monday, the Maze gang said it had exfiltrated 33.2 GB of data, and posted a 2 GB archive with samples of the stolen data. It's organized into two folders: "Council Office" and "Finance." But it's not clear if any of the dumped data is sensitive or non-public - or if the ransomware gang extracted any such data from the city.
"They may have only released what they consider to be the minimum necessary to push the city into giving in to their demands," Brett Callow at anti-virus firm Emsisoft tells ISMG. "Indeed, a kidnapper need only send a lock of hair of a pinky finger to prove he has a hostage. So the bottom line is, it’s impossible to say how much data the group may or may not have.”
Bird Construction Named
The same goes for another alleged victim: Bird Construction Inc., based in Ontario, Canada, which trades on the Toronto Stock Exchange. On Saturday, the large construction firm was added to Maze's list of victims, in an entry that said its systems had been crypto-locked on Dec. 2, and 60 GB of corporate data stolen.
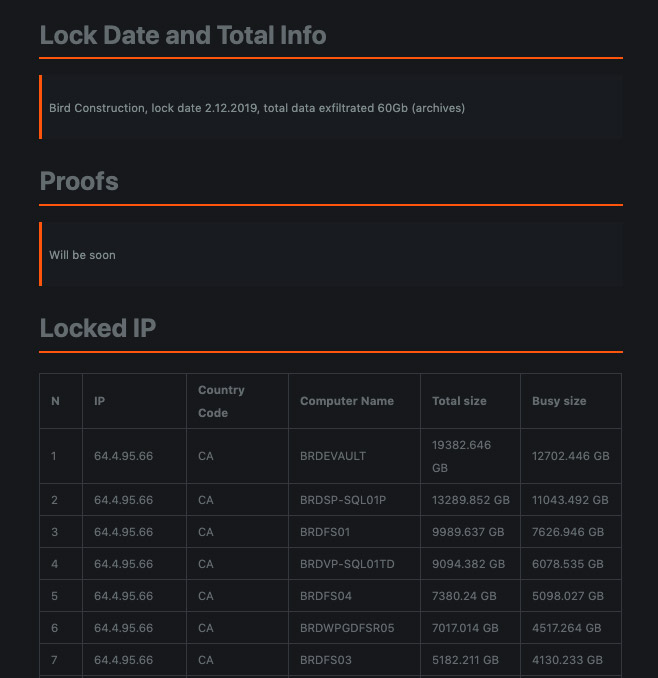
But by Monday, Bird's name had disappeared from the list of victims.
Does that mean Bird Construction paid the Maze gang? The company didn't immediately respond to a request for comment.
Under Canadian privacy regulations- the Personal Information Protection and Electronic Documents Act - any firm that suffers a certain type of data breach is required to notify officials and alert victims "as soon as feasible." In particular, PIPEDA tells organizations that they must "report any breach of security safeguards involving personal information under your control if it is reasonable in the circumstances to believe that the breach of security safeguards creates a real risk of significant harm to an individual."
Reached for comment about any potential ransomware infection or data breach suffered by Bird Construction, a spokeswoman for the Office of the Privacy Commissioner of Canada tells ISMG: "I don’t have any information for you at this time."
'Maximize the Payout'
While threatening to dump stolen data might seem like a natural fit for ransomware-wielding attackers, perhaps surprisingly, there was no confirmed case of such tactics being used, at least until last month. That’s when the Maze gang followed through on its threat to dump 700 MB of data it stole from Allied Universal, a California-based security services firm, after Allied refused to pay a ransom demand of 300 bitcoins, now worth about $2.3 million. (In what may or may not be a coincidence, Allied has an office in Pensacola.)
Experts say these types of shakedown tactics are not surprising. "Ransomware is a game of how to maximize the payout," says cybersecurity expert Jake Williams, president of Georgia-based Rendition Infosec (see Ransomware 2.0: Cybercrime Gangs Apply APT-Style Tactics).
Biggest Threat: Lost Business
If a tactic works, expect criminals to use it. But it's not yet clear if threatening ransomware victims with doxing, unless they pay up, is an effective strategy.
"Data exfiltration as an extortion tactic is not terribly lucrative as compared to ransomware," says Bill Siegel, CEO of ransomware incident response firm Coveware. That's because what organizations often fear more than the cost of a ransom payment is the total cost of excessive downtime (see Ransomware Attackers Leak Stolen Data).
"If a company finds out its data has been breached, the damage is done. Paying the criminal is pointless, and the criminals know that," Siegel says. "Ransomware, on the other hand, causes downtime, and downtime can bankrupt a company."
In addition, it's not clear how many ransomware gangs take the time, or have required technical sophistication, to not just deploy crypto-locking malware, but also to first identify and exfiltrate high-value data without being detected by security teams and forcibly ejected from the network.
Skilled Attackers at Work
Ransomware strains do not include data exfiltration capabilities. To steal data, criminals must first hack into a network. Security experts say that more advanced gangs already do this, for example, by using stolen or brute-forced remote desktop protocol credentials.
"If threat actors have gained access via RDP, for example, they have full access to the network," says David Stubley, CEO at 7 Elements, a security testing firm and consultancy in Edinburgh, Scotland. For such attackers, stealing data is one option, and leaving systems crypto-locked, together with a ransom demand, is another.
Some ransomware-wielding attackers have demonstrated relatively advanced hacking prowess, experts say. "The mega-ransomware breach kind of thing that you're hearing about in the news, these are relatively skilled attackers," says Rendition Infosec's Williams. Beyond having network-penetration chops, for example, some gangs are using botnets such as Emotet to better distribute their ransomware.
But Williams also emphasizes that for victim organizations, the cost of paying a ransom - whether or not they opt to pay it - can be a fraction of the bigger costs facing victims. "We often focus on the ransom costs, and the ransom costs are negligible - negligible - compared to loss of business opportunity and the business disruption caused by those attacks," he says.




















