Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime
Malicious Crypto Apps Target Mobile Users, Mainly in China
Both Android and iOS Users at Risk From Trojanized Fake Cryptocurrency Wallets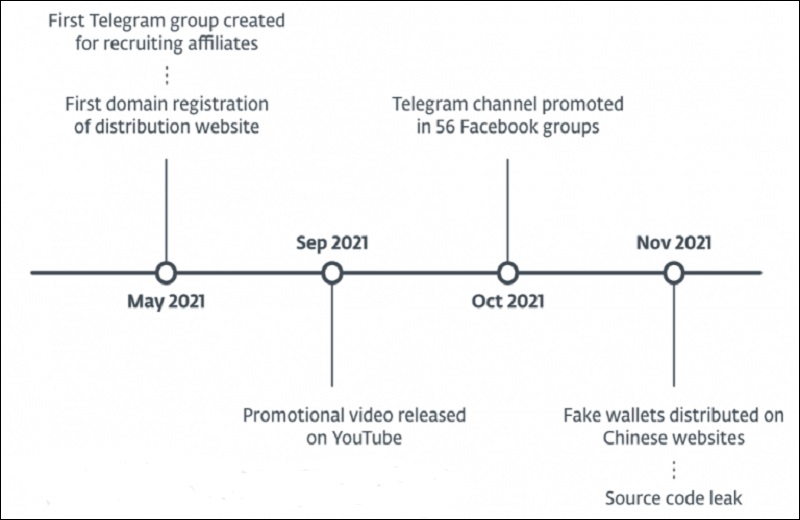
The ban on cryptocurrency transactions in China has led many users in the country to look for alternatives. But researchers from cybersecurity firm ESET say that threat actors have leveraged this scenario and targeted Chinese users by delivering them Trojanized cryptocurrency wallet apps.
See Also: Rising IoT Botnets and Shifting Ransomware Escalate Enterprise Risk
Scheme Began in 2021
In early March 2021, researchers began discovering dozens of malicious cryptocurrency apps in a scheme that was specifically targeted at Android and iOS mobile devices. The main goal of these malicious apps is to steal users' funds, the researchers say.
The first stage in any such malicious scheme is the distribution of the apps, which the threat actor accomplished by using fake websites; mimicking legitimate wallet services, such as MetaMask, Coinbase, Trust Wallet, TokenPocket, Bitpie, imToken and OneKey; and advertising on legitimate sites using "misleading" articles, the researchers say.
For better outreach, the threat actors also recruited intermediaries or distribution partners through Telegram channels and Facebook groups, the researchers say.
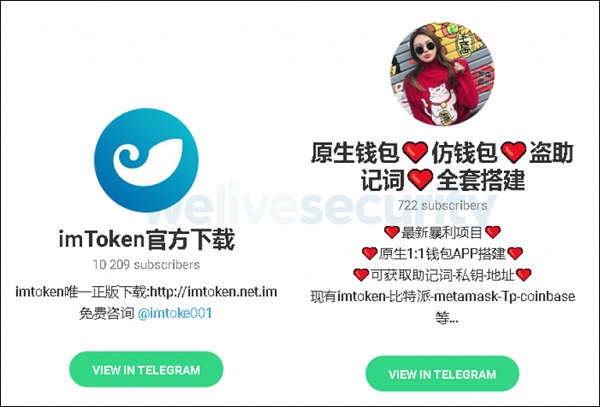
The researchers say that since May 2021, they have found at least a dozen Telegram groups that were created by the threat actor behind this scheme to promote it. The threat actor also advertised in at least 56 Facebook groups, they say.
Besides these distribution vectors, the researchers also found several other counterfeit wallet websites that are exclusively targeting mobile users.
Work of a Sophisticated Actor
"This is a sophisticated attack vector since the malware's author carried out an in-depth analysis of the legitimate applications misused in this scheme," the researchers say. The analysis enabled them to insert malicious code into the legitimate code and make it hard to detect while ensuring that the functionality of the apps remained the same as that of the originals.
"At this point, ESET Research believes that this is likely the work of one criminal group," the researchers tell Information Security Media Group.
An Open Steal Deal
"These malicious apps also represent another threat to victims, as some of them send secret victim seed phrases to the attackers' server using an unsecured HTTP connection. This means that victims' funds could be stolen not only by the operator of this scheme, but also by a different attacker eavesdropping on the same network,” says Lukas Stefanko, the ESET researcher who discovered the scheme. "We also discovered 13 malicious apps impersonating the Jaxx Liberty wallet. These apps were available on the Google Play store," he adds.
And although anyone can steal by eavesdropping and there is no need to manually have a different code, researchers warn users that other threat actors may tweak and start using this code as they have found evidence of the front-end and back-end source code, along with the recompiled and patched mobile apps included in these schemes, being publicly shared on at least five Chinese websites and in a few Telegram groups in November 2021.
"Since the code is already shared publicly for free, it might attract other attackers - even outside of China - and target a wider spectrum of cryptocurrency wallets using an improved scheme," the researchers say.
Different Tactics for Android and iOS
The malicious app behaves differently depending on the operating system it is installed on, the researchers say. "On Android, it appears to target new cryptocurrency users who do not yet have a legitimate wallet application installed on their devices. On iOS, the victim can have both versions installed - the legitimate one from the App Store and the malicious one from a website."
In iOS, these malicious apps are not available on the App Store, probably because of the security perimeter and stringent checks in place before an app is uploaded, the researchers say. "They must be downloaded and installed using configuration profiles, which add an arbitrary trusted code-signing certificate."
But in Google Play, sometimes the security checks are bypassed using obfuscation techniques, although Play Protect is used by Google to verify the safety of the app, the researchers say. "Based on our request as a Google App Defense Alliance partner, in January 2022, Google removed 13 malicious applications found on the official store," they add.
In August 2021, Google removed eight fake cryptomining mobile apps from its Play Store, but researchers at security firm Trend Micro flagged 120 other apps on users' phones purporting to also be cryptominers (see: Google Removes Fake Crypto-Mining Apps)
How to Stay Safe
Stefanko shared the following tips with ISMG on how to stay safe online:
Download and install apps only from official sources, such as the Google Play store or Apple's App Store. A reliable mobile security solution should be able to detect this threat on an Android device.
There are no security solutions for iOS, so download apps only from the official App Store, be especially cautious about accepting configuration profiles, and avoid a jailbreak on this platform.
If any of these apps are already installed on your device, the removal process differs based on the mobile platform:
On Android, regardless of the source from which you downloaded the malicious app - official or unofficial, if you doubt the legitimacy of the source, uninstall the app.
On iOS, after you uninstall the malicious app, remove its configuration profile by going to Settings > General > VPN & Device Management. Under the Configuration Profile, you will be able to find a name of the profile that needs to be removed.
If you either already created a new wallet or restored an old one using a malicious application, immediately create a brand-new wallet with a trusted device and application and transfer all funds to it.





















