Account Takeover Fraud , Cybercrime , Fraud Management & Cybercrime
Magecart Card Skimmer Hidden in Image's EXIF Metadata
Malwarebytes Researchers Find Malicious JavaScript in WordPress Plugin
Payment card hackers are now hiding malicious JavaScript inside an image's EXIF metadata and then sneaking the image onto e-commerce sites, according to the security firm Malwarebytes.
See Also: Account Takeover Attacks: How to Protect your Reputation and Revenue
Malwarebytes suspects the hacker gang known as Magecart 9 is responsible, according to the report. “Magecart” is the umbrella name for cybercriminals who plant JavaScript skimmers in the check-out functions of e-commerce sites to steal payment card data.
Jérôme Segura, Malwarebyte's director of threat intelligence, says the new campaign’s use of steganography to hide a card skimmer is a new development for Magecart-style attacks. Additionally, the payment card data was exfiltrated through an image, he points out.
Malwarebytes found malware in the WooCommerce WordPress plugin for one online store, which it did not name in the report. WooCommerce is popular with small and midsized e-commerce businesses, the report notes.
Injecting the Skimmer
Getting the skimmer malware on the site required that the malicious actors first weaponize a favicon, a small branding image often used in browser tabs that’s often downloaded from third-party sites. In this case, Segura found extraneous code had been appended to a legitimate script hosted by the merchant. This code loads a favicon from a malicious site.
Using a favicon is a relatively new tactic, but one previously used in other Magecart attacks (see: JavaScript Skimmers Found Hidden in 'Favicon' Icons).
The favicon in this campaign is an image of the word "copyright," according to Malwarebytes. We can see a field called ‘Copyright’ from which data is getting loaded. Attackers are using the Copyright metadata field of this image to load their web skimmer," the report notes.
The malware can be seen when the image is looked at through an Exchangeable Image File, or EXIF, viewer, according to Malwarebytes.
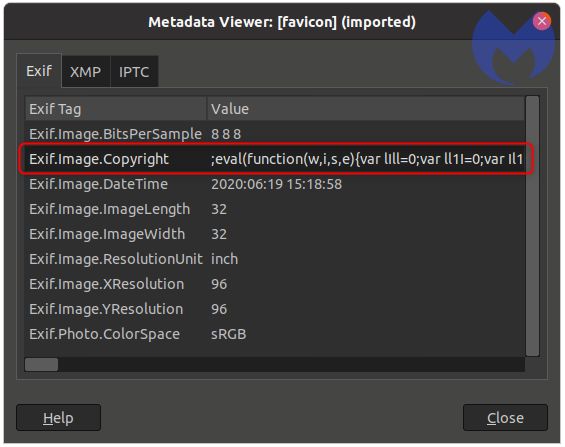
"The abuse of image headers to hide malicious code is not new, but this is the first time we witnessed it with a credit card skimmer," Segura says, adding the word "eval" indicates that the code is an executable; it’s also heavily obfuscated.
A New Twist
This skimmer functions like others in the Magecart family, grabbing the content of the input fields in an ecommerce checkout function for such information as shoppers’ names, billing addresses and payment card details. It then encodes this information using Base64 – but then it does something unexpected, Segura says.
"It comes with a twist, as it sends the collected data as an image file, via a POST request. The threat actors probably decided to stick with the image theme to also conceal the exfiltrated data via the favicon.ico file," Segura notes.
Attackers Leave Clues
Segura used a skimmer toolkit the researchers discovered to help discover a great deal more about the malware and its creators. The skimmer's source code was found in a ZIP file and left exposed in the open directory of a compromised site, along with the gate.php containing the skimmer's entire logic, the report notes.
Using the information, Malwarebytes was able to track down other versions of the malware and start connecting the dots.
"This skimmer may have ties with Magecart Group 9. Security researcher @AffableKraut pointed out that a domain (magentorates[.]com) using this EXIF metadata skimming technique has the same Bulgarian host, same registrar, and was registered within a week of magerates[.]com," Segura writes.
Magecart-style attacks, which use digital card skimming or scraping capabilities to steal card data, have claimed many victims since 2017. Those include Ticketmaster, Macy's, British Airways and, most recently, the retail chain Claire's (see: Claire's: Magecart E-Commerce Hackers Stole Card Data).
Security firm Trend Micro recently found Magecart JavaScript skimmers on payment sites used by eight U.S. cities (Payment Card Skimmer Attacks Hit 8 Cities).