Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service
LockerGoga Ransomware Suspected in Two More Attacks
Chemical Manufacturers Hexion and Momentive Still Recovering from Cyberattacks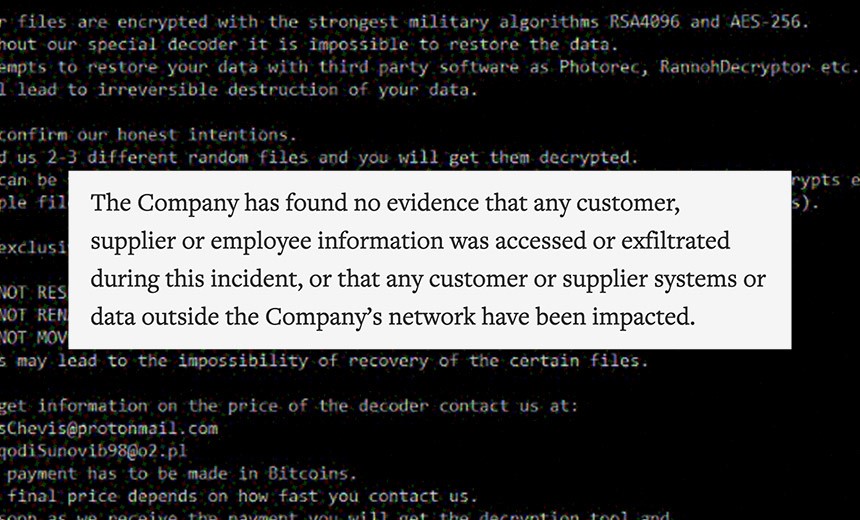
A pair of U.S. chemical manufacturing companies have reportedly been struck by the LockerGoga ransomware over the past month and continue to recover from the same cyberattack that took down part of aluminum giant Norsk Hydro last week.
See Also: Beating the Business of Ransomware
The attacks against Hexion and Momentive started on March 12, according to Vice Motherboard, which first reported the two incidents on Friday. The report cites an internal company email, which explained that some of the company's files had been encrypted during a cyberattack.
The two companies, which share a common owner in Apollo Management Holdings, each issued similar press releases on Friday , citing "a recent network security incident that prevented access to certain systems and data within the company's network." Both firms noted that the attack affected corporate systems, not the networks associated with its manufacturing facilities, and their security teams were working to restore those systems, which include corporate email.
When reached on Monday by Information Security Media Group, a spokesman for both companies declined to comment further and referred back to the previously released statements.
The Vice report noted similarities between the ransom emails sent to Hexion and Momentive and those found during the investigation of the incident at Norsk Hydro.
Additionally, the MalwareHunterTeam posted similar ransom emails on its Twitter account Saturday, which all appear related to LockerGoga.
So, the news says Hexion & Momentive got LockerGoga on March 12.
— MalwareHunterTeam (@malwrhunterteam) March 23, 2019
There's this sample: https://t.co/gltv5EfI3m
Uploaded to VT 12th evening, has the same email addresses as the ones seen in the news...
First screenshot is from @lorenzofb's tweet, second is from this sample's run. pic.twitter.com/ibNeI2D46X
Understanding LockerGoga
If the attacks against Norsk Hydro, Hexion and Momentive are indeed connected to the same form of malware, LockerGoga is a strain of ransomware to watch during the first half of this year.
First spotted by the MalwareHunterTeam, it appears that LockerGoga has also been used to target Paris-based Altran earlier this year. This particular strain of ransomware is different from others, in that it's used as more of a targeted attack against a victim rather than spreading from one PC to another across the network.
In the case of LockerGoga, the attackers might use stolen remote desktop protocol (RDP) credentials or brute-force methods to crack into the network in order to plant the malware. Additionally, phishing emails or unpatched vulnerabilities might also allow the ransomware to enter the network, according to Cisco Talos, which published its own analysis on LockerGoga.
In its analysis, the Talos team notes that while the initial infection vector of LockerGoga is not known, it seems that during the infection process, the ransomware executable is coped onto the %TEMP% directory of the target system.
The ransomware then attempts to clear the Windows Events Logs. From there:
"The ransomware then creates the ransom note and begins the encryption process. LockerGoga supports many of the common types of files that organizations typically use to store important data. As files are encrypted, the originals are deleted and replaced with the encrypted data, which is stored as files with the "*.LOCKED" file extension. Unlike many ransomware variants commonly observed, LockerGoga also encrypts the contents of the victim's Recycle Bin directory," according to Talos.
The Talos analysis also notes that LockerGoga encrypts each file within an infected system, which is not a common practices and can be time consuming and require additional overhead for the individual or group behind the attack.
Unlike other types of ransomware, the Talos team found that the LockerGoga ransom note does not include a specific bitcoin or Monero wallet address to pay the ransom, but instructs that victim to contact the attackers through an email address.
Finally, there is also no evidence of a command-and-control server that would allow remote connectivity between the infected network and the attackers, according to Talos.
Norsk Hydro Update
While it's not clear the extent of the damage against Hexion and Momentive, Norsk Hydro has been offering periodic updates on the company's cleanup of LockerGoga, including its work with Microsoft to help unlock files and recover IT systems.
The company remains determined to not pay the ransom and is using its backup system to restore various IT systems throughout its facilities.
"We are continuing to make progress towards a resolution, but the situation remains serious and we are still dependent on extraordinary measures to run many of our operations. This is particularly challenging within our Extruded Solutions business area, where the implementation of work-around solutions is both challenging and time-consuming," Norsk Hydro CFO Eivind Kallevik says in statement released Friday.
So far, Norsk Hydro has managed to isolate the attack. The company also continues to work various investigative authorities, including Norway's National Investigation Service (Kripos) and the Norwegian National Security Authority (NSM)
The one part of the company's operations that are still only running at 50 percent are the divisions that produce extruded and rolled aluminum products, according to Friday's statement.