Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
Crypto-Locking Kraken Ransomware Looms Larger
Ransomware-as-a-Service Operation Joins Forces With Fallout Exploit Kit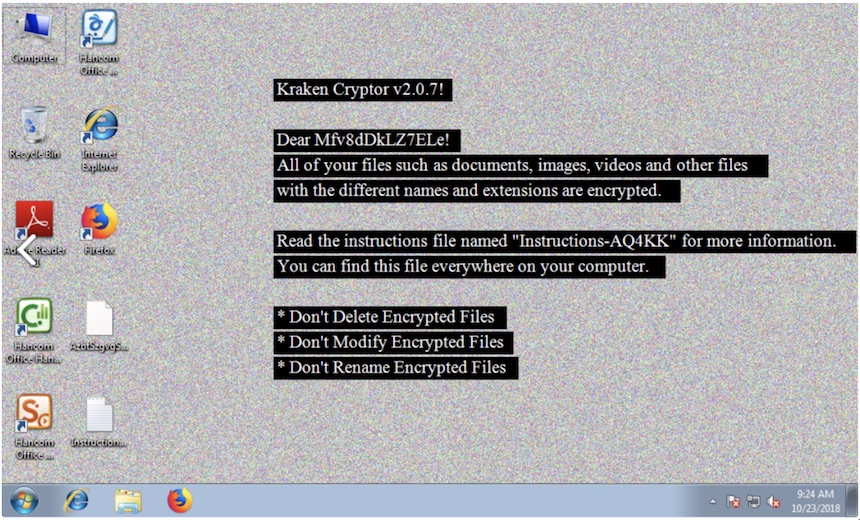
A slick ransomware-as-a-service operation called Kraken has begun leveraging a new exploit kit to help it score fresh victims, and unfortunately, that combination may prove challenging to defend against, according to new research released by analysts at McAfee and Recorded Future.
See Also: Beating the Business of Ransomware
The two security vendors have collaborated on a new report into the Kraken Cryptor, which the companies say first appeared on a top Russian-language forum in August.
Many of the insights into the ransomware come from one of its customer service representatives, who goes by the nickname "ThisWasKraken." That individual runs Kraken Cryptor as an affiliate program, which enables others to license fresh versions of the ransomware that have been designed to avoid anti-virus software.
"Kraken's goal is to encourage more wannabe cybercriminals to purchase this RaaS and conduct their own attacks, ultimately leading to more money in the developers' pockets," writes Gary Davis, chief consumer security evangelist for McAfee, in a blog post.
Decryption Fee: Up to $7,800
Once it infects a system, Kraken quickly encrypts all files without regard for the size of any file, the analysts say.
The primary target for Kraken is computers running Windows 8, 8.1 and 10. It can also touch shared storage devices on the same network as an infected system. Once it crypto-locks a system, recovering files without paying a ransom is impossible unless victims can wipe systems and restore them from backups.
Forum posts written by ThisWasKraken provide more insight into how the affiliate business model works, involving the group that develops Kraken as well as partners who pay to use it.
Here's the business model: Partners sign up for $50, and agree to send 20 percent of all ransoms paid to the Kraken team. In return, the partner receives fresh versions of the Kraken malware payload, which are designed to not trigger anti-virus software, every 15 days, according to the report. Partners also receive 24/7 customer support.
The interactions between a victim and a Kraken affiliate partner occur over email. When a partner signs up with Kraken, the partner supplies an email address for communicating with a victim, which the Kraken development team builds into the individual partner's custom version of Kraken.
The partner also specifies their the desired ransom amount, which ranges from 0.075 to 1.25 bitcoin, worth $470 to $7,845 as Wednesday. Partners can also request certain countries be added to an exclusion list so people there are not targeted.
A slew of countries are already on that list, presumably to help whoever has been developing and distributing the ransomware avoid the attention of local authorities. The countries on the mandatory "do not target" list are Armenia, Azerbaijan, Belarus, Estonia, Georgia, Iran, Kazakhstan, Kyrgyzstan, Latvia, Lithuania, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine and Uzbekistan.
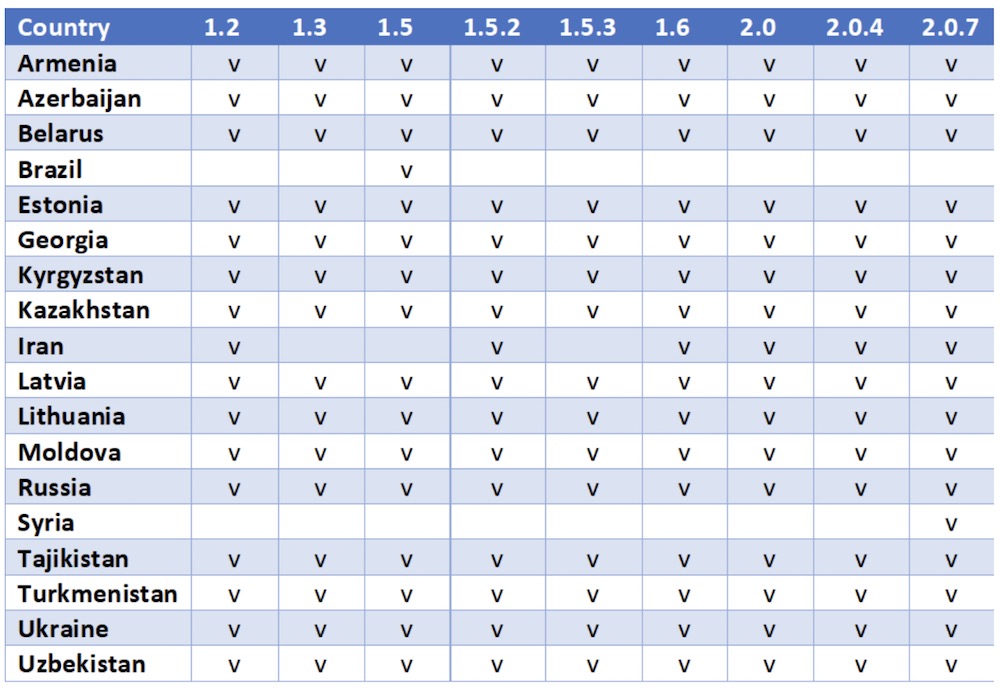
Curiously, Syria was also excluded in the latest 2.0.7 version of Kraken. That follows the lead from another group that runs the prevalent GandCrab ransomware. According to Bleeping Computer, GandCrab stopped targeting people there after victims of the long-running conflict complained. Shortly thereafter and separately, a team of researchers and police managed to capitalize on errors in GandCrab's code and once again created a free decryptor for the latest version of the ransomware (see: Fresh GandCrab Decryptor Frees Data for Free).
"Regarding Syria: We believe that the Kraken actors have had the same change of heart as the actors behind GandCrab, who recently released decryption keys for Syrian victims after a tweet claimed they had no money to pay the ransoms," researchers from McAfee and Recorded Future write in a joint blog post.
To ensure that partners don't try to deal directly with victims - to avoid remitting their 20 percent cut of proceeds to the Kraken team - the developers have put in a process designed to ensure compliance. In a forum post, ThisWasKraken notes that victims can ask for a sample file to be decrypted. The partner then sends one of the victim's files to the Kraken Cryptor ransomware service, which then sends back a decrypted file that can be sent to the victim.
"After the victim pays the full ransom, the affiliate member sends 20 percent of the received payment to the RaaS to get a decryptor key, which is then forwarded on to the victim," McAfee and Recorded Future write. "This system ensures the affiliate pays their percentage to the affiliate program and does not simply pocket the full amount for themselves."
Fallout Exploit Kit Distribution
Researchers have also noticed a development that may intensify instances of Kraken seen in the wild.
Around the end of August, a researcher going by the nickname nao_sec flagged a new exploit kit. Nao_sec dubbed it Fallout because its behavior appeared close to the Nuclear exploit kit. Nao_sec linked Fallout with the distribution of GandCrab (see: GandCrab Ransomware Partners With Crypter Service).
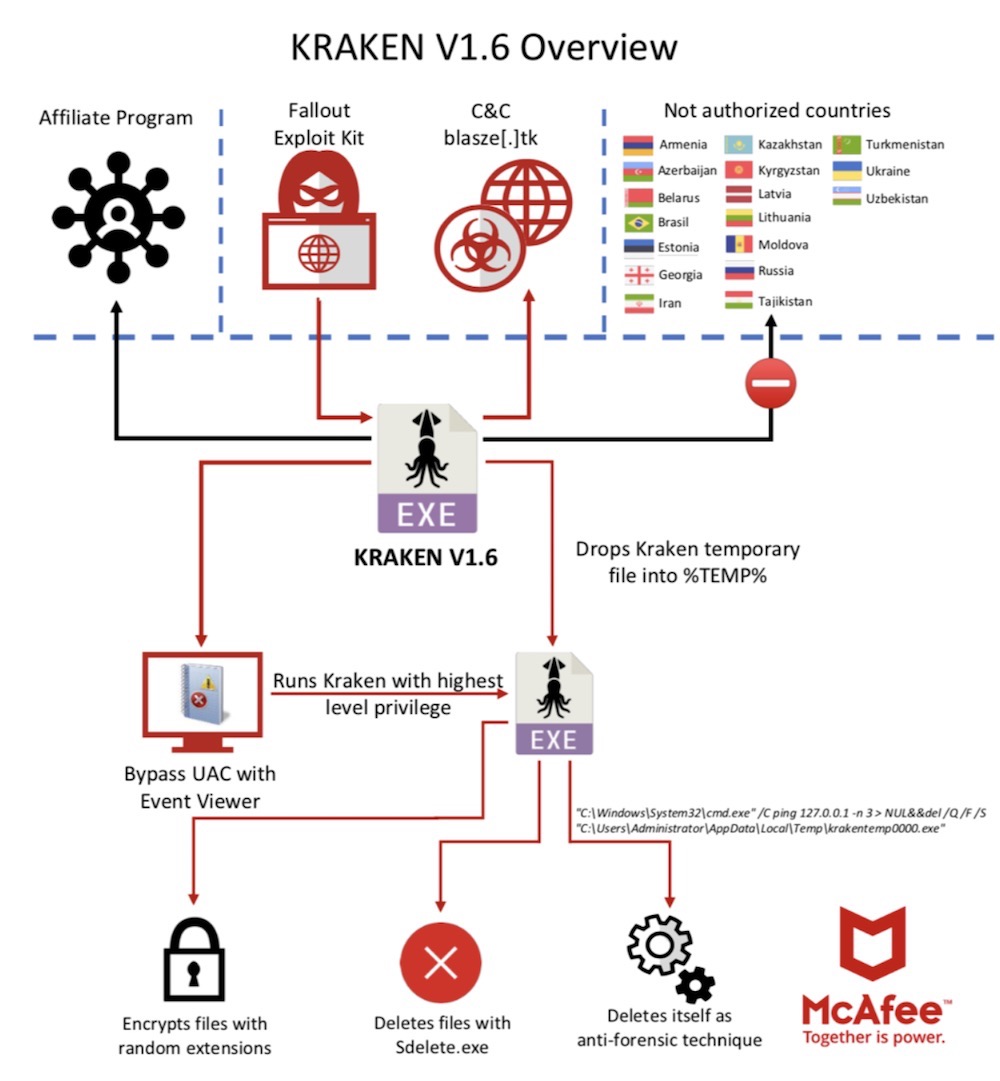
In early September, researchers at the cybersecurity firm FireEye wrote in a blog post that Fallout in part leverages malvertisements, or malicious advertisements, to redirect selected victims to the kit's landing page. Once on a landing page, an exploit kit often tests out a range of recent software vulnerabilities to see if a computer is vulnerable. If it is, a payload gets delivered.
When nao_sec observed Fallout in late August, it used a vulnerability for Adobe's Flash player, CVE-2018-4878, and one for Microsoft's Windows VBScript Engine, CVE-2018-8174.
ThisWasKraken indicated in a forum post that the group was interested in joining up with Fallout. "It should be noted that on multiple occasions, ThisWasKraken mentioned the Fallout exploit kit and praised it for its high infection rate," according to McAfee and Recorded Future's report. "At one point, ThisWasKraken even stated, 'One of our partners joined the Fallout exploit kit, which is good for us.'"
Exploit kits aren't effective as in days' past, due in part to better automatic updating, leading to fewer exploitable vulnerabilities in browsers, together with a steep decline in the use and install base of Flash Player (see: Neutrino Exploit Kit: No Signs of Life).
But exploit kits haven't completely disappeared from the cybercrime scene and can apparently serve up enough fresh victims to make their use compelling enough for the likes of the GandCrab and Kraken ransomware-as-a-service operators.