Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Kaspersky: Banks, Governments, Telcos Hit by Fileless Malware
Same Attack Techniques Used to Command ATMs to Dispense Cash
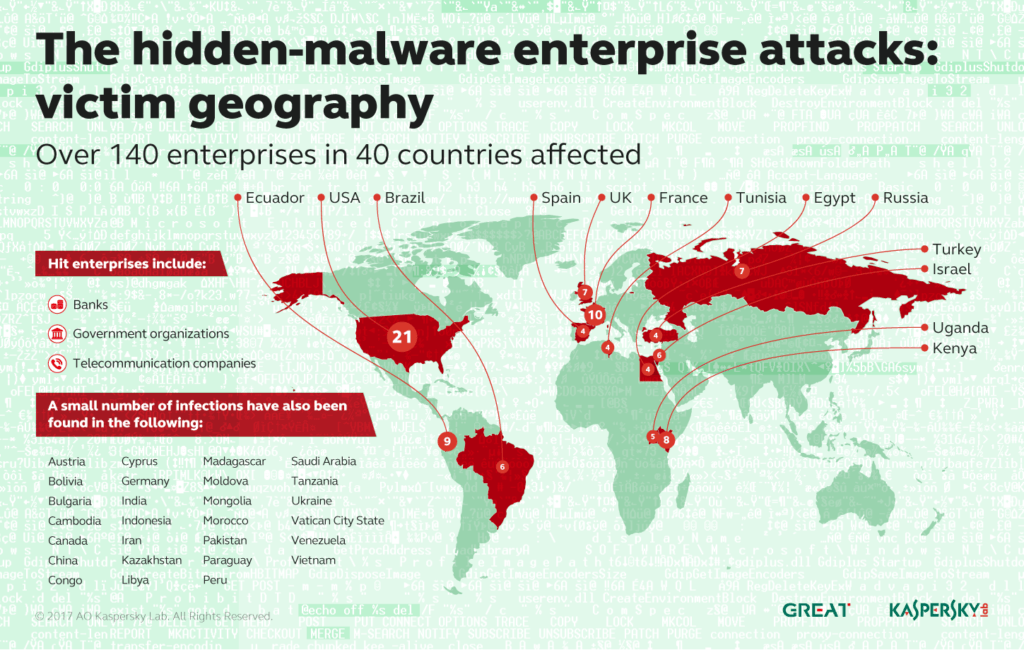
Russian security vendor Kaspersky Lab says hackers using fileless malware to stay undetected have compromised as many as 140 banks, government organizations and telecommunications companies.
See Also: Revealing the Dark Web: How to Leverage Technologies to Alert and Block Dark Web Access
Except for an initial software exploit used to gain access to systems, the hackers revert to using standard Microsoft utilities and other open-source penetration testing tools to keep a low profile.
Malware never touches a computer's hard disk, and a reboot of a computer erases traces of malicious activity left in memory, leaving few clues for investigators.
Similar techniques were used by a notorious cybercriminal group called Carbanak, which plundered banks of more than $1 billion through fraudulent wire transfers and back-end attacks that implanted malware on ATMs. Kaspersky revealed Carbanak in February 2015.
The latest finding "comes as no surprise to us," says Peter Brady, general manager of Kaspersky Lab. "History has shown us that cybercriminals are going to keep getting more creative."
Kaspersky unveiled some details in a blog post on Feb. 8 and plans to release a full report at its Security Analyst Summit in early April.
It did not share the names of the organizations attacked but said countries affected included the U.S., U.K., Ecuador, Brazil, Tunisia, Egypt, Russia, Turkey, Israel, Uganda, Kenya, France, Morocco, Saudi Arabia and the Vatican City State.
The Sneaky Toolbox
Because security applications have improved their ability to detect malicious software, attackers are increasingly using tools commonly used by computers administrators once they've compromised a machine.
"Unfortunately the use of common tools combined with different tricks makes detection very hard," according to Kaspersky's blog.
The investigation kicked off after one of Kaspersky's clients found a tool called Meterpreter running in memory.
Meterpreter is part of Metasploit, the penetration testing toolkit. It's used post-exploitation for mischief, such as stealing passwords or files. It sits in memory, which can avoid triggering alerts from intrusion prevention or detection systems.
To gain broader access across a target's network, these attackers also use Mimikatz to obtain the passwords and credentials for other machines, and PowerShell, Microsoft's scripting language, for control. Malicious PowerShell scripts were found in Windows registries, Kaspersky says.
Traffic from infected machines was tunneled to command-and-control servers controlled by the attackers using NETSH, another Microsoft utility. Another standard Microsoft utility, SC, is used to manage services, Kaspersky writes.
After the initial incident was uncovered, Kaspersky found more than 100 other organizations also had malicious PowerShell scripts. The discovery was based on anonymous technical information it collects from its customers.
It wasn't clear from Kaspersky's post why it took an alert from one of its clients to uncover such a high number of infected organizations within its own customer base.
So Who Did It?
The approach and methods used in these latest attacks are reminiscent of state-sponsored attacks. Kaspersky referenced the Duqu family of malware, which is closely related to Stuxnet - a worm allegedly designed by the U.S. and Israel to wreck Iran's uranium centrifuges (see Duqu 2.0 Espionage Malware Discovered).
Kaspersky has predicted that advanced techniques used in so-called advanced persistent threat attacks would be embraced by advanced cybercriminals. The company says it isn't sure if all of the infections discovered resulted from the same attacker and is uncertain about the identity of the attackers.
"This attack shows how no malware samples are needed for successful exfiltration of a network and how standard and open source utilities make attribution almost impossible," Kaspersky writes.
















