Governance & Risk Management , Insider Threat
4 Components of the Insider Threat
I3P's Shari Lawrence Pfleeger: Beyond the IndividualShari Lawrence Pfleeger, research director at the Institute for Information Infrastructure Protection, is helping direct a multi-institution research project to leverage human behavior to reduce cybersecurity risk. Simply, how can the insider threat be diminished?
"We look at the insider threat from a variety of perspectives, and particular we look at behavioral sciences as well as computer sciences," Pfleeger says in an interview with GovInfoSecurity.com. "It's relevant to the WikiLeaks problem in that somebody who obliviously had access inside an organization managed to get documents outside the organization. We tend to look at things like this as unwelcome behavior, and the problem in general of how do you keep people who work for you or to whom you have given legitimate access? How do you give them incentives to do only what you want them to do and not what you don't want them to do?"
In the interview, with Information Security Media Group's Eric Chabrow, Pfleeger:
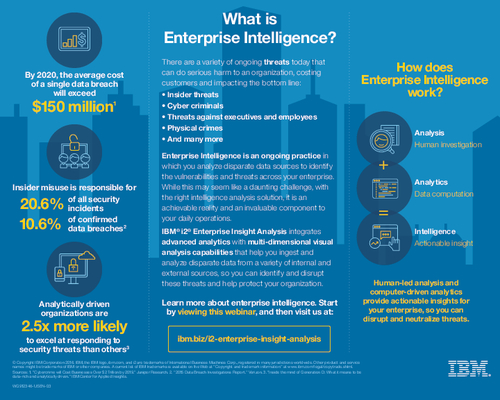
- Defines the taxonomy of four components I3P created to explore ways to limit or eliminate the insider threat: organization, individual, information technology system and environment;
- Delves into conflicting IT security policies most organizations implement: one codified, the other unwritten but widely followed; and
- Reveals a large percentage of employees practice some sort of workplace misbehavior.
An internationally recognized expert in software engineering, system quality and computer science research methods, Pfleeger joined the Dartmouth College-sponsored Institute for Information Infrastructure Protection, known as I3P, in September, though she has had a long working relationship with the institute. For the previous eight years, Pfleeger had built the Rand Institute's capabilities in software measurement and cyber security. During that time, she led I3P-funded projects on the economics of security and on assessing insider threat.
For 20 years prior to joining Rand, Pfleeger led a consultancy specializing in assessing whether and how information technology supports government and business goals. Pfleeger is the author of more than 100 papers and a dozen textbooks and professional books, including Security in Computing, co-authored with her husband Charles, which is a widely used textbook.
Pfleeger received a bachelor degree in mathematics from Harpur College, master degrees in mathematics and planning from the Pennsylvania State University and a Ph.D. in information technology and engineering from George Mason University. She was also awarded an honorary doctorate by Binghamton University for her philanthropy and social activism.
I3P is a national consortium of leading academic institutions, national laboratories and not-for-profit research organizations founded in 2002, serving as a cornerstone in the coordination of cybersecurity research and development. The I3P brings together researchers, government officials and industry representatives to address cybersecurity challenges affecting the nation's critical infrastructures.
Drawing from its member institutions, I3P assembles multi-disciplinary and multi-institutional research teams able to bring in-depth analysis to complex and pressing problems. I3P shares research findings at institute-sponsored workshops and professional conferences and in peer-reviewed journals as well as through technology transfer to end users. I3P also supports programs to promote education and public awareness.