Endpoint Security , Incident & Breach Response , Managed Detection & Response (MDR)
Intel Confirms Fresh Spectre, Meltdown Patch Problems
Latest CPUs Also Suffer From Frequent Rebooting Problem
Intel says the firmware updates it developed to help protect users against Meltdown and Spectre flaws are causing stability problems in its newest chips.
See Also: Resolving Security's Biggest Productivity Killer
On Wednesday, the head of Intel's data center group, Navin Shenoy, said that the firmware updates were causing problems with Ivy Bridge, Sandy Bridge, Skylake and Kaby Lake, which are the codenames of its latest-generation chips .
"While the firmware updates are effective at mitigating exposure to the security issues, customers have reported more frequent reboots on firmware updated systems," Shenoy said in a blog post.
Those security issues are a trio of connected, speculative execution flaws in microprocessors known as Spectre and Meltdown (see Meltdown and Spectre Forecast: Patch Now and Keep Patching).
Intel says it's been working overtime with a number of other business partners -including Dell, HPE, HPI, Lenovo and Microsoft - to address the problems.
"We have reproduced these issues internally and are making progress toward identifying the root cause," Shenoy said. "In parallel, we will be providing beta microcode to vendors for validation by next week."
The stability problem in newer chips also exists in some older CPUs. On Jan. 11, Intel confirmed that some older Intel CPUs - specifically, Broadwell and Haswell - that had been updated with Intel's Meltdown and Spectre firmware patches were rebooting more frequently than they should be (see Spectre Reversal: AMD Confirms Chips Have Flaws).
"We have received reports from a few customers of higher system reboots after applying firmware updates," Shenoy said in a Jan. 11 blog post. "Specifically, these systems are running CPUs for both client and data center."
Patch Development, Deployment Continues
Meanwhile, Intel has not yet finished issuing all of the firmware updates it has promised. "We have now issued firmware updates for 90 percent of Intel CPUs introduced in the past five years," Shenoy says. "But we have more work to do."
In fact, many vendors are continuing to develop and distribute patches for Spectre and Meltdown.
Apple, Cisco, Dell, Fujitsu, Google, IBM, Juniper, Microsoft and Oracle are among the many vendors that must update users' firmware and operating systems with Meltdown and Spectre protections.
On Tuesday, as part of its quarterly patch update, Oracle released fixes for 237 flaws across its products, including its first batch of Spectre and Meltdown fixes.
But Oracle and many other vendors have yet to publish a full list of affected products or a timeline for when users can expect to see patches.
Performance Problems
Unfortunately, protecting CPUs from the speculative execution flaws has a performance impact, especially in data centers as well as on clients that don't have the latest and greatest chip architecture or operating system (see Performance Hit: Meltdown and Spectre Patches Slow Systems).
Intel says it's continuing to gauge the impact that its fixes are having. "To date, we have tested server platforms running two-socket Intel Xeon Scalable systems - code-named Skylake, our latest server microarchitecture," Shenoy says.
"Generally speaking, the workloads that incorporate a larger number of user/kernel privilege changes and spend a significant amount of time in privileged mode will be more adversely impacted," he says.
Intel has published the results of these tests and promised to issue more performance data and benchmarks of older systems as quickly as possible.
Patching: Performance Impact
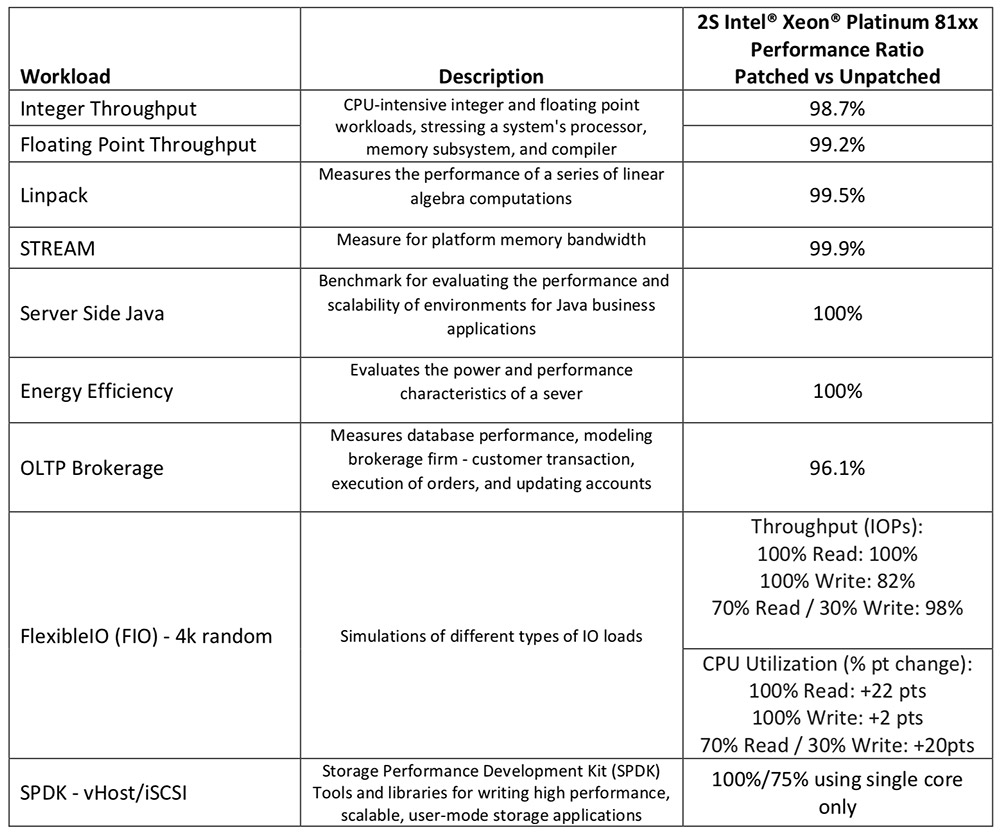
Intel says that it's trying to also identify workarounds for performance problems. "For example, there are other mitigations options that could yield less impact," Shenoy says, pointing to an Intel white paper for more information. In addition, Intel is moving to get Retpoline, a security approach discovered by Google that helps address part of the Spectre vulnerability, and which is short for "return trampoline," into place.















