Cybercrime , Cybercrime as-a-service , Fraud Management & Cybercrime
Initial Access Brokers: Credential Glut Weakening Prices?
Criminal Services Facilitate Cybercrime Gangs' Rapid Access to Hacked Sites
Initial access brokers continue to ply their trade, selling immediate access to hacked sites to make it easier for gangs to steal data and crypto-lock systems. But security researchers say an overabundant supply of access credentials appears to be driving down the prices being commanded on cybercrime forums and markets.
See Also: The State of Organizations' Security Posture as of Q1 2018
Researchers say criminals, especially those waging ransomware attacks, are relying more than ever on the services of initial access brokers so they can compromise more victims and potentially generate greater profits via ransom payoffs.
Using initial access brokers also helps ransomware-wielding gangs practice big game hunting - taking down larger targets in an attempt to score larger ransoms - by giving them a menu of options from which to choose rather than having to take down victims themselves (see: Ransomware's Helper: Initial Access Brokers Flourish).
"When criminal malware operators purchase access, it eliminates the need to spend time identifying targets and gaining access, allowing for increased and quicker deployments as well as higher potential for monetization," cybersecurity firm CrowdStrike noted in a report issued earlier this year.
Ransomware incident response firm Coveware reports that in Q4 of last year, the average ransom paid by a ransomware attack victim was $154,108. So the investment in paying for access that someone else has already harvested is a fraction of the average payoff a gang receives when a victim does pay a ransom.
Buying Access, For Less
An overabundant supply of access credentials on criminal marketplaces appears to be driving down prices, according to Digital Shadows, which sells digital risk protection solutions.
The firm reports that while it found about 500 initial access listings throughout all of 2020 across cybercrime forums, darknet marketplaces and beyond, in the first quarter of this year, it has already counted 225 such listings. Of those, 45% were for victim organizations in Europe and 29% for those in North America.
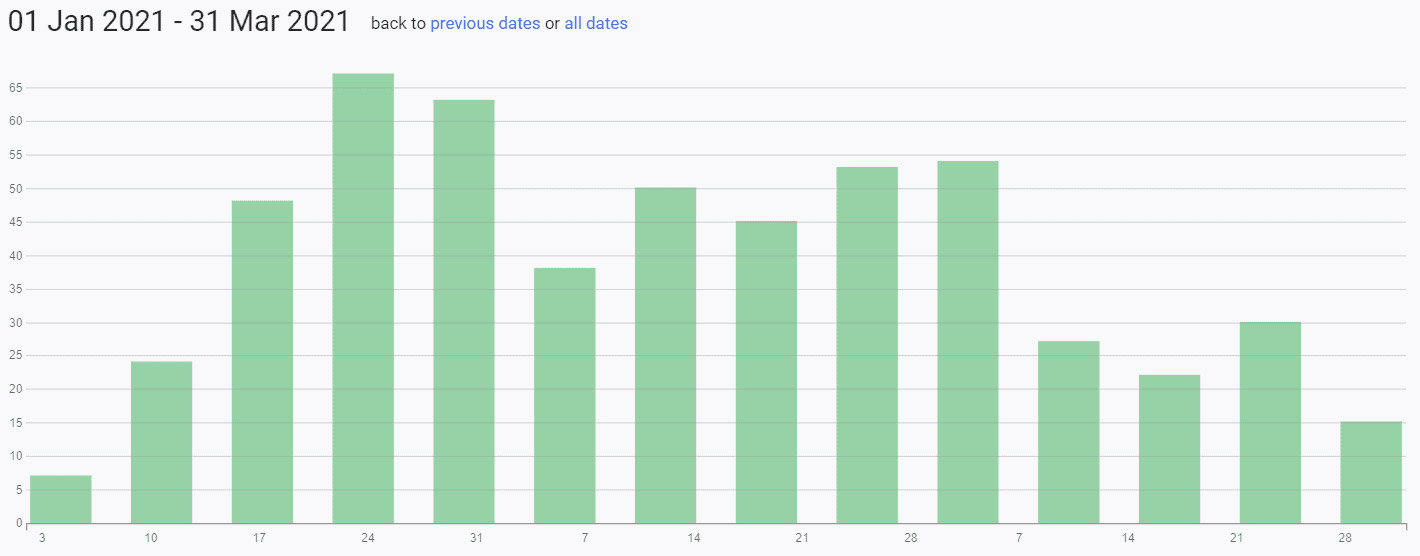
Meanwhile, Digital Shadows found last year that the average price for buying access credentials to a victim's website, when a listing named a price, was about $7,100 - typically payable in bitcoins. But in Q1 of this year, the average price had plummeted to about $1,900.
"The most surprising piece of data that we observed in the first months of 2021 is the drastic drop of the average price per listing - by 73%," Stefano De Blasi, a threat researcher at Digital Shadows, tells Information Security Media Group.
"Why the change? We chalk it up to the laws of supply and demand," De Blasi says in a Tuesday blog post.
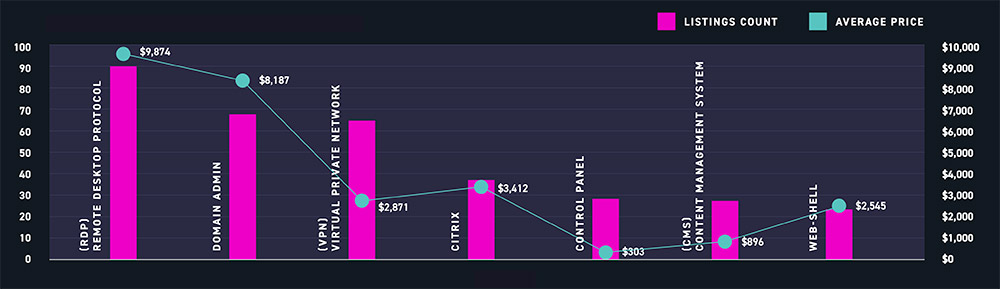
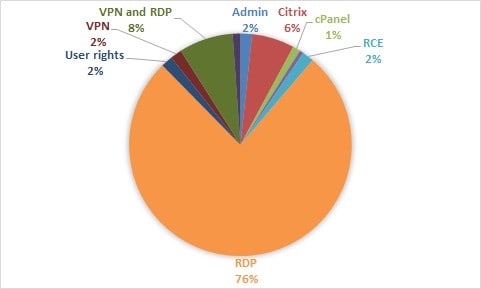
One of the steepest declines came in the average price paid for remote desktop protocol credentials, which Digital Shadows says accounted for 76% of all access being offered in Q1. These were selling for $481 each, which was a fraction of what they typically cost in 2020.
"So it might be that criminals have increasingly noted the business opportunity in just selling access to organizations but have been met with more competition - and hence lower prices - in the market," he says. "However, differences in the geographic location and industry of the targeted companies likely influenced the observed, average price."
Supply Continues to Increase
The apparent rise in Q1 supply mirrors a trend that security firms previously reported: The number of initial access vendors appears to increasing year after year, and the overall number of hacked sites for which access is being sold continues to increase.
In 2018, the sum of all prices for access information being offered by about 37 initial access brokers was about $1.6 million, according to cybersecurity firm Group-IB. But for the first half of 2020, the sum of all such access being sold had increased to $6.2 million.
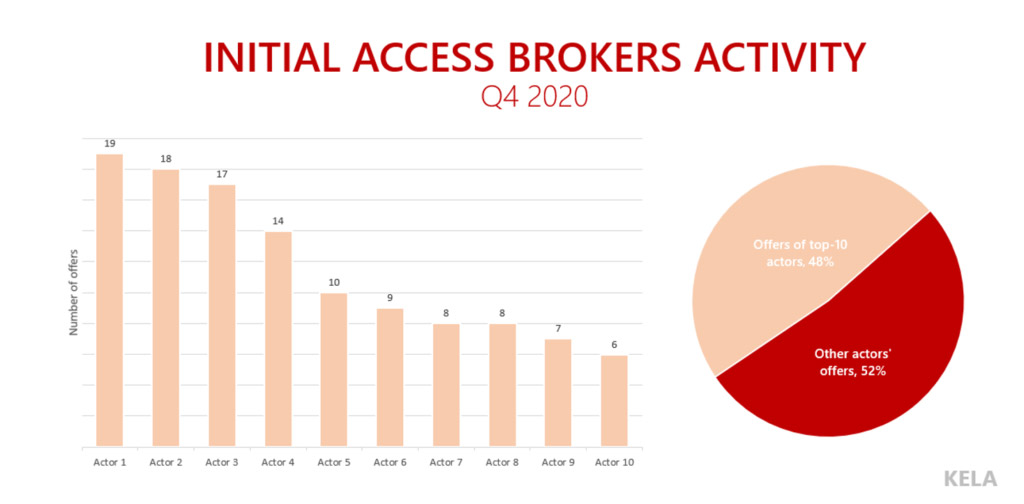
For Q4 of 2020, threat intelligence firm Kela found that 10 sellers dominated the initial access broker landscape, accounting for more than half of all listings.
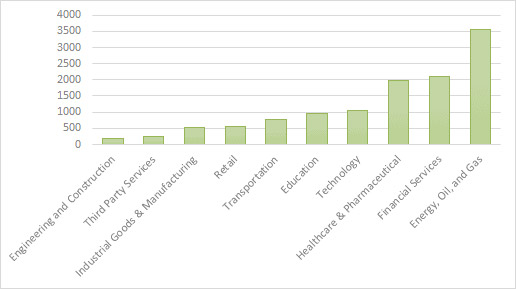
Also, credential prices vary widely depending on the type of organization involved. "For example, the engineering and construction sector targets consisted mainly of European countries and maintained a relatively low average access price of $193," Digital Shadows' De Blasi says. But access to victims in the technology sector, most of which were U.S.-based, commanded a much higher price - an average of $1,045, he said.
Gangs Seek Partners
Reviewing access brokers' listings doesn't provide a complete picture of how brokers and gangs work together.
Victoria Kivilevich, a threat intelligence analyst at Israeli cyberthreat intelligence monitoring firm Kela, earlier this year reported that crime gangs don't just communicate with initial access brokers via darknet markets, forums and other cybercrime sites. Some also appear to be partnering with gangs to give them first right of refusal on new offerings.
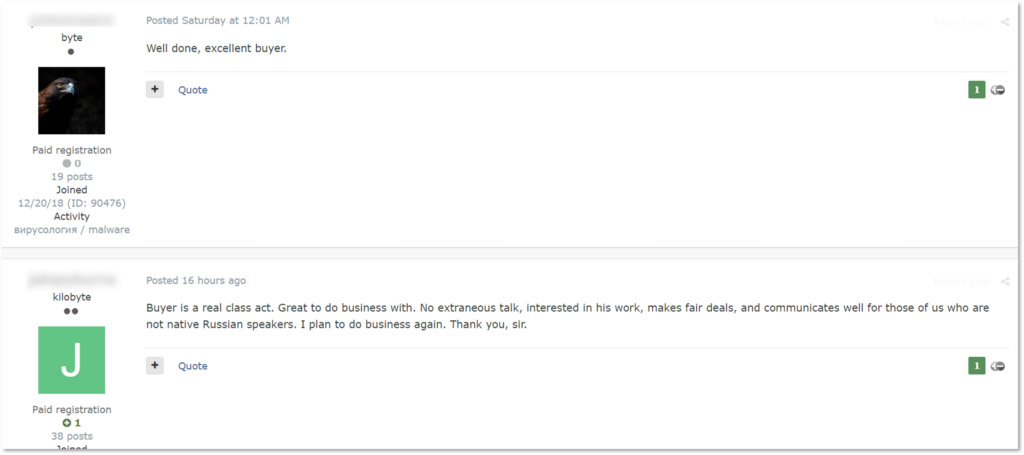
In addition, much sales activity apparently happens outside of a crime forum. "Brokers often offer a bunch of accesses in one thread and request potential buyers contact them privately to get the whole list," Kivilevich says. "Some of them are looking for one buyer and state that they’re ready to work for a percentage, most likely meaning a share from the amount gained in a successful ransomware attack."






















