Heartbleed: Gov. Agencies Respond
U.S., Canada Issue Statements on OpenSSL Vulnerability
As news of the Heartbleed bug sinks in, government agencies in the U.S. and Canada are reacting to the newly discovered Internet vulnerability.
See Also: Threat Protection and Data Loss Prevention: Strengthening Office 365 Email Security
The Department of Homeland Security posted a blog on Heartbleed April 11, warning that malicious actors could exploit un-patched systems. "That is why everyone has a role to play to ensuring our nation's cybersecurity," says Larry Zelvin, director of the National Cybersecurity and Communications Integration Center.
NCCIC also shared several tips that organizations can take to protect themselves, including changing passwords after the vulnerability has been addressed; closely monitoring sensitive online accounts, including e-mail and bank accounts; and ensuring that visited websites requiring personal information such as login credentials or credit card information are secure with the HTTPS identifier in the address bar.
The Federal Financial Institutions Examination Council issued a statement April 10 expecting financial institutions to incorporate patches on systems and services, applications and appliances using OpenSSL and upgrade systems as soon as possible to address the Heartbleed vulnerability.
"Financial institutions should consider replacing private keys and X.509 encryption certificates after applying the patch for each service that uses OpenSSL and consider requiring users and administrators to change passwords after applying the patch," the FFIEC says. "Financial institutions relying upon third-party service providers should ensure those providers are aware of the vulnerability and are taking appropriate mitigation action."
The Federal Deposit Insurance Corp. on April 10 issued a press release urging financial institutions to utilize available resources to combat threats tied to the Heartbleed bug.
Greg Hernandez, spokesperson at the FDIC, says the advisory was issued because of vulnerabilities with OpenSSL. "The [vulnerability] could expose banks and their customers to risks such as compromise of sensitive information or fraud," he says. "Many banks rely upon this technology for web-based banking, e-mail, authentication and other critical or sensitive banking functions."
Hernandez says: "Banks should ensure that OpenSSL vulnerabilities are covered in their patch management, software maintenance or security update procedures as described in existing FFIEC guidance, as well as their risk assessments."
The FDIC highlights several resources banks should utilize, including U.S. CERT, the Secret Service's Electronic Crimes Task Force, FBI InfraGard and information sharing and analysis centers.
Canada Halts Online Tax Returns
The Canada Revenue Agency on April 9 shut down public access to its online services, halting online tax returns until the situation has been remedied.
"After learning ... about the Internet security vulnerability named the Heartbleed Bug that is affecting systems around the world, the CRA acted quickly, as a preventative measure, to temporarily shut down public access to our online services to safeguard the integrity of the information we hold," the CRA says in a statement posted to its website.
Minister of National Revenue Kerry-Lynne D. Findlay says individual taxpayers will not be penalized for the service interruption. "Interest and penalties won't be applied to individuals filing 2013 tax returns after April 30 for [the] period equal to length of service disruption," she says in a Twitter post.
Meanwhile, the U.S. Internal Revenue Service issued a statement April 9 saying it will continue to accept tax returns as normal. "Our systems continue operating and are not affected by this bug, and we are not aware of any security vulnerabilities related to this situation."
The IRS is continuing to monitor the situation and remains in contact with its software partners. "The IRS advises taxpayers to continue filing their tax returns as they normally would in advance of the April 15 deadline."
Experts Weigh in
Security thought-leaders continue to offer insight into the Heartbleed bug. Avivah Litan, fraud analyst at Gartner Research, calls the issue "mega-serious."
"I'm just trying to understand why all the news reports are focused on individual communications with websites," Litan says. "SSL protocols, including OpenSSL, are used in most 'trusted' machine to machine communications. The bug affects routers, switches, operating systems and other applications that support the protocol in order to authenticate senders and receivers and to encrypt their communications."
What the vulnerability means, Litan says, is any trusted communications traffic using the protocol is not trustworthy. "Forget having to plant back doors in encryption libraries, as the NSA allegedly did," she says. "The backdoors are already built in. So criminals and other naysayers can essentially eavesdrop on any sensitive communications using Open SSL 1.0.1 such as payment processing, conversations, file sharing and more."
David Bailey, chief technology officer at BAE Systems applied Intelligence, says Heartbleed is "dangerous" for organizations. "The vulnerability is not just found on a single site," he says. "It is in a software library called OpenSSL which is used by many websites for security."
He continues: "Only time will tell whether digital criminals are able to exploit this to acquire sensitive personal data, take over user accounts and identities and steal money."
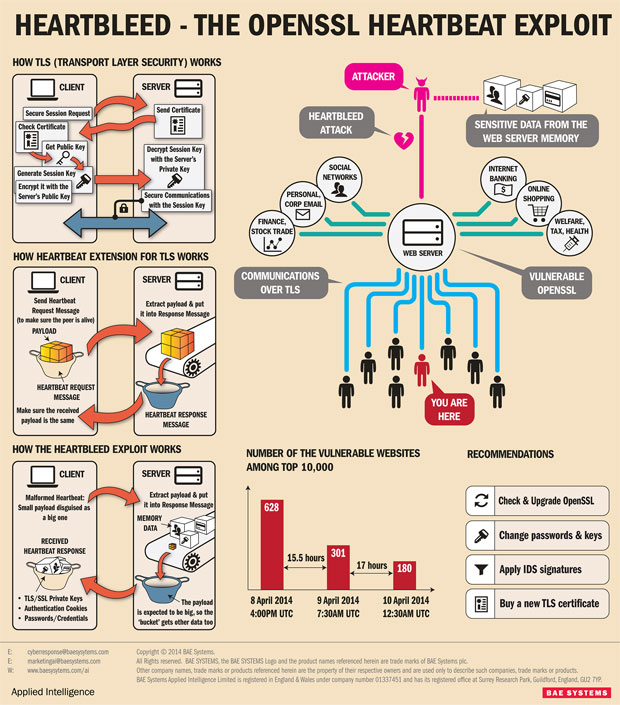
BAE Systems Applied Intelligence has released an infographic that details and deconstructs the vulnerability:
Information Security Media Group polled security experts in banking, government and healthcare, as well as the research and vendor communities, for insights on Heartbleed and how organizations should respond to it (see: How to Treat the Heartbleed Bug).
About Heartbleed
Heartbleed exposes a flaw in OpenSSL, a cryptographic tool that provides communication security and privacy over the Internet for applications such as web, e-mail, instant messaging and some virtual private networks (see: Heartbleed Bug: What You Need to Know).
"The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software," says Codenomicon, the Finland-based security vendor that discovered the bug, along with a researcher at Google Security. "This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users."
Codenomicon says Fixed OpenSSL has been released and needs to be deployed now across websites vulnerable to the bug. Operating system vendors and distribution, appliance vendors and independent software vendors need to adopt the fix and notify their users, Codenomicon says. "Service providers and users have to install the fix as it becomes available for the operating systems, networked appliance and software they use."
David Chartier, CEO of Codenomicon, the company that uncovered the Heartbleed bug, says organizations need to properly test and vet the critical software components and applications to identify unknown weaknesses in them. "The best defense is to have secure software," he says (see: Heartbleed Discoverer Speaks Out).
Additionally, organizations can use this online tool to see if their website is vulnerable.
(Executive Editor Tracy Kitten contributed to this story).