Cybercrime as-a-service , Fraud Management & Cybercrime , Fraud Risk Management
Hacking-for-Hire Group Expands Cyber Espionage Campaign
Kaspersky Says 'DeathStalker' Targets Smaller Law Firms, Financial Institutions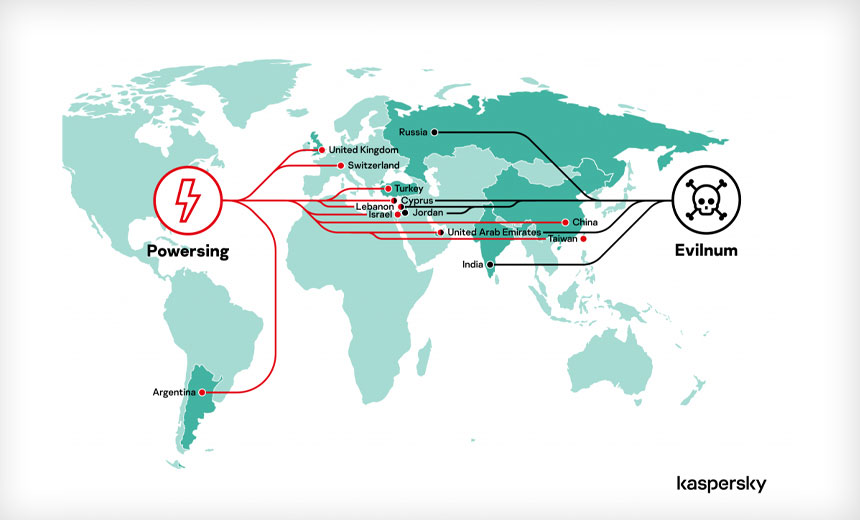
A hacking-for-hire group dubbed "DeathStalker" is expanding its cyber espionage operations around the world, targeting smaller law firms and financial institutions, according to research from security firm Kaspersky.
Deathstalker has been in operation since at least 2012, and Kaspersky researchers have been tracking its activities since 2018, according to the report.
Over the last two years, researchers have found that the group has expanded its efforts to target organizations throughout the world, from Europe to Latin America. The group targets smaller law firms and financial institutions on behalf of clients for whom it conducts corporate espionage, according to Kaspersky.
"The group is after business intelligence, financial information, accounting documents, private correspondence, etc.," Ivan Kwiatkowski, senior security researcher at Kaspersky, tells Information Security Media Group. "In competitive sectors, they would also be interested in client lists, product prices and ongoing negotiations. It's not easy for us to determine how successful they’ve been, but we know for a fact that they have been able to infiltrate a significant number of companies."
The Tactics
DeathStalker starts its espionage efforts using spear-phishing emails that contain what appears to be a legitimate Microsoft Word document.
In the most recent campaign, however, the Kaspersky researchers found that this Word document disguises a Microsoft LNK shortcut file that contains malicious scripts, which then download malware onto a compromised device. This malicious code, Powersing, is PowerShell-based malware that can take screenshots and run arbitrary code within an infected device.
Powersing has the ability to avoid detection by anti-virus software through the use of so-called "dead-drop resolvers," the researchers say. These allow the malicious code to communicate with the hacker's command-and-control server and blend with normal network traffic, according to the report. This works by sending instructions through seemingly benign social media posts that use encryption to hide instructions.
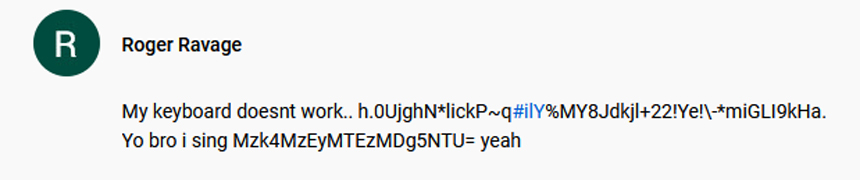
"When the malware establishes a connection to YouTube or Reddit to obtain information, it is completely impossible for a cautious systems administrator to separate this malicious traffic from the rest of the traffic," Kwiatkowski says. "In other words, they cannot tell whether it’s a user watching a cat video or the malware getting information from the dead drop resolver. Nobody is going to think twice about slightly more YouTube traffic, whereas connections to unheard of domains can raise suspicions."
When the Kaspersky researchers looked closer at Powersing, they found similarities between this malware strain and another variant called Janicab, which was the subject of a 2015 report by security firm F-Secure.
Janicab uses the same type of LNK file shortcut to disguise the malicious code in an attached Word document. Once installed within a compromised device, the malware also tries to communicate with a little-used YouTube channel to connect to a command-and-control infrastructure.
"Janicab also periodically sends screenshot captures of the victim's desktop to the command-and-control and appears to enable the execution of arbitrary Python scripts," according to the Kaspersky report.
Malware Similarities
Kaspersky researchers also noticed similarities between Powersing, Janicab and a third strain called Evilnum, which security firm ESET examined at length in a July report about attacks targeting fintech firms (see: APT Group Targets Fintech Companies).
The Kaspersky researchers found code overlap between all three malware variants, and Evilnum uses LNK shortened file links to disguise its presence. The malware also attempts to use dead-drop resolvers to connect with an IP address hosted on a GitHub page, according to the report.
The Kaspersky report notes that Evilnum targets fintech firms to gather intelligence and data, which is similar to the activities associated with DeathStalker.
"This report’s thesis is that the three malware families - Powersing, Evilnum and Janicab - are owned and operated by the same group, and this is something we assess with medium confidence," Kwiatkowski says.
The Kaspersky report notes researchers have detected Powersing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan and Turkey over the last two years. Evilnum has been spotted in Cyprus, India, Lebanon, Russia and the United Arab Emirates.






















