Hacker Sheds Light on Attack Method
U.S., International Chemical Companies Latest Target
In a paper published Monday, Eric Chien and Gavin O'Gorman of Symantec's Security Technology and Response Division said they contacted the man they call Covert Grove, a literal translation of his name. He lives in the Hebei region of China, about 180 miles southwest of Beijing. Chien and O'Gorman said Covert Grove briefly attended a vocational school, specializing in network security and has limited work experience, most recently maintaining multiple network domains of the vocational school.
According to the paper, Covert Grove claims to have leased for $32 a month a virtual private server in the United States to log into QQ, a popular instant messaging system in China. The server provides a static IP address, which would restrict login access to particular IP addresses. "While possible, with an expense of 200 Chinese yuans a month for such protection and the usage of a U.S.-based VPS, the scenario seems suspicious," the paper's authors said.
The Symantec security specialists said they weren't able to recover any evidence the virtual private serve was used by any other authorized or unauthorized users. "When prompted regarding hacking skills, Covert Grove immediately provided a contact that would perform 'hacking for hire'. Whether this contact is merely an alias or a different individual has not been determined," Chien and O'Gorman wrote. "We are unable to determine if Covert Grove is the sole attacker or if he has a direct or only indirect role. Nor are we able to definitively determine if he is hacking these targets on behalf of another party or multiple parties."
The latest attacks started in July and continued into mid-September, Symnatec said, though artifacts of the attack wave such as command and control servers were used as early as April against targets outside the chemical industry. Symantec said the goal of the attackers appears to be to collect intellectual property such as design documents, formulas and manufacturing processes. The same attackers appear to have a lengthy operation history including attacks on other industries and organizations
Chemical Companies Targeted
Symantec said it believes the attackers behind the attack on the chemical industry computers are the same ones who targeted last spring non-governmental organizations supporting human rights. They next targeted the automotive industry in late May, but remained dormant from June to mid-July. "At this point," the paper said, "the current attack campaign against the chemical industry began. This particular attack has lasted much longer than previous attacks, spanning two and a half months."
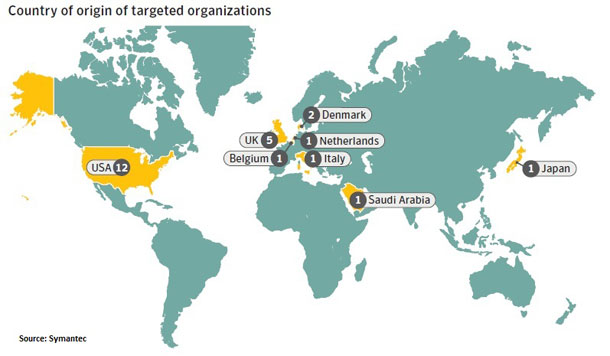
Symantec said it confirmed attackers targeted at least 29 chemical companies in the latest attack wave as well as 19 companies in other sectors, primarily defense. In a recent two-week period, 101 unique IP addresses contacted a command and control server with traffic consistent with an infected machine, the paper said, adding that these IPs represented 52 different unique Internet Service Providers or organizations in 20 countries. Among the businesses affected: Fortune 100 companies involved in R&D of chemical compounds and advanced materials, including those used for military vehicles.
The attackers sent e-mails to either an individual or a group of employees with an attachment with a self-extracting executable file containing PoisonIvy, a common backdoor Trojan developed by a Chinese speaker, Symantec said. When the attachment was opened, and PoisonIvy installed, it contacted a command and control server using an encrypted communications protocol. Using the command and control server, the attackers then instructed the compromised computer to provide an infected computer's IP address, the names of all other computers in the workgroup or domain and dumps of Windows cached password hashes. Typically, the paper's authors said, the attackers' primary goal was to obtain domain administrator credentials and/or gain access to a system storing intellectual property.

















