Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Fresh Python-Based Trojan Designed as Information Stealer
Researchers: 'PyMicropsia' Malware Targets Outlook, Web Browsers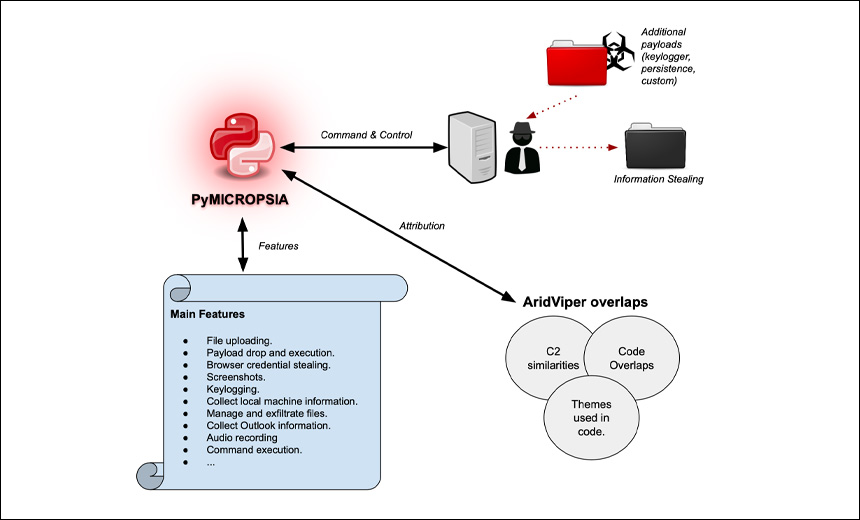
A new Python-based information-stealing Trojan dubbed "PyMicropsia" is linked to a hacking group called AridViper, which is active mainly in the Middle East, according to Palo Alto Networks' Unit 42.
The PyMicropsia malware has the potential to target Microsoft Windows devices and can exfiltrate data and information from the victim's web browser as well as Outlook, the report notes. The malware is also capable of taking screenshots, recording audio and killing running programs, the researchers say
PyMicropsia is linked to another Windows malware variant called Micropsia, which has been active in the Middle Eastern region since 2016, according to the Unit 42 report. The researchers also note both PyMicropsia and Micropsia are linked to the malware family deployed by the AridViper hacking group - also known as Desert Falcon or APT-C-23 - which has been conducting cyberespionage campaigns in the Middle East since 2015.
Targeting Victims
While the PyMicropsia Trojan is still under development, the Unit 42 researchers note that its operators are likely using spear-phishing emails to deliver the malware to potential victims or tricking targets into visiting websites that host the malicious code.
Once PyMicropsia is delivered to a targeted device, it appears as a Windows executable by using by PyInstaller - code that converts applications into stand-alone executables, according to the report.
In addition to its data-stealing features, the malware also uses built-in Python libraries, PyAudio for audio stealing and managed security services to take screenshots, the report adds.
Although the malware extensively uses Python features, the researchers note many of the malicious software's capabilities remain unused, which is considered a sign that its operators are still developing the malware and adding capabilities.
Other Targets
PyMicropsia has been mainly designed to target Windows devices, but the researchers note the malware also contains code that checks if the device is running other operating systems that use POSIX, a standard that allows for interoperability between operating systems, or Darwin, which is a Unix-like OS.
"This is an interesting finding, as we have not witnessed AridViper targeting these operating systems before and this could represent a new area the actor is starting to explore," the Unit 42 report notes.
In September, the security firm ESET uncovered Android spyware used by AridViper for reading notifications from messaging apps and recording calls and screens. The attackers were spreading this malware as an Android app, the report said.
In February, Israeli security firm Check Point revealed that the Palestinian group Hamas used AridViper malware disguised as dating apps to target soldiers in the Israel Defense Forces.






















