Cybercrime as-a-service , Fraud Management & Cybercrime , Mobile Payments Fraud
Fresh Card Skimmer Attacks Multiple E-Commerce Platforms
Researcher: Malware Found On Several Large Content Management Systems
A recently uncovered payment card skimmer is targeting several large content management systems that support the online checkout pages of dozens of e-commerce sites, according to researchers with Dutch security firm Sansec.
See Also: OnDemand Webinar | Defeat Application Fraud and Improve User Experience
To date, this new skimmer has been found on a dozen online stores' checkout pages that are supported by content management systems hosted on platforms from Shopify, BigCommerce, Zen Cart and WooCommerce, according to the report.
These types of payment card skimmers, or JavaScript skimmers, are typically deployed by a cybercriminal organization dubbed by several researchers as Magecart, which is an umbrella term for several separate gangs that use similar techniques and tools to target e-commerce checkout pages to steal credit card information and other data (see: Claire's: Magecart E-Commerce Hackers Stole Card Data).
So far, Sansec has not directly tied this recently uncovered skimmer to one particular Magecart group. And while it’s not clear who is exactly behind this malware, the report notes that its operators have created an unusual skimmer that can target multiple content management systems all at once instead of individually.
How Skimmer Works
The Sansec report does not detail how the fraudsters using this payment skimmer initially compromise the content management system, such as by using other malware or taking advantage of a particular vulnerability.
The report does note that hosted platforms such as BigCommerce and Shopify do not allow custom JavaScript on the e-commerce checkout pages they support.
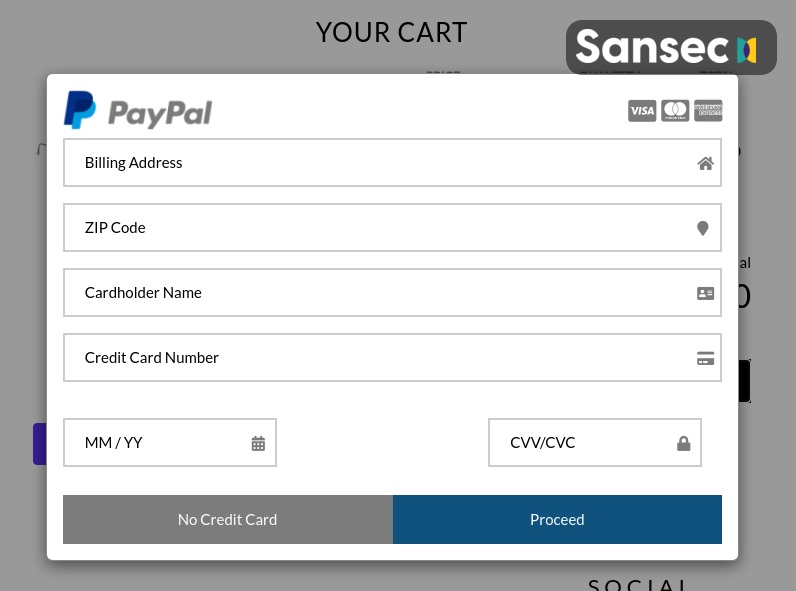
Once the skimmer is planted on the site, the malware will display a fake payment form before the victim enters the actual checkout page. In one example that is designed to look like a PayPal account, the form asks for a billing address, ZIP code, credit card number and the name of the customer along with the CVV or CVC code.
Once that data is entered, the victimized customer is shown an error message and is then redirected to the actual e-commerce checkout site. The payment card, however, is harvested and stored by the JavaScript skimmer.
The Sansec researchers also found that the malware will automatically create specific domains that will store the encrypted data using Base64 encoding, as well as create a way for the fraudsters to then exfiltrate the data later.
These automatically created domains first appeared on Aug. 31, which is believed to be the start date for this particular campaign, the report states.
"To summarize: this campaign shows that platforms are no boundary to the profitable fraud of online skimming," the Sansec researchers note. "Wherever customers enter their payment details, they are at risk."
Other Techniques
Over the past several months, security researchers have shown that the fraudsters who use these malicious JavaScript skimmers have developed new techniques to hide the malware within e-commerce checkout sites.
In June, for example, Malwarebytes found a group called Magecart 9 hid JavaScript inside an image's EXIF metadata and then snuck that image onto e-commerce sites to steal payment and credit card data (see: Magecart Card Skimmer Hidden in Image's EXIF Metadata).
In another instance, researchers with RiskIQ found a new variant of the Grelos skimmer that co-opted the infrastructure that Magecart uses for its own skimming attacks against e-commerce sites (see: Grelos Skimmer Variant Co-Opts Magecart Infrastructure).