Dridex Banking Trojan: Worldwide Threat
Phishing Campaign Uses Malware Embedded in Word Documents
Attackers are targeting online banking users' account information worldwide through sophisticated phishing attacks designed to deliver Microsoft Word documents containing malicious macro code known as Dridex.
See Also: New OnDemand | Cyber Risk Graph: Solving the Data Problem of Proactive Security
So far, Australia, the United Kingdom and the United States are the top three targets for the worldwide Dridex malware campaign, according to Trend Micro, an Internet security firm.
"Attackers leveraging this new banking malware have dusted off a legacy tactic in which infection occurs through a believable spamming campaign," says JD Sherry, vice president at Trend Micro. Dridex is a variant of the Cridex malware, which is also designed to steal personal information.
Adam Kujawa, head of malware intelligence at Malwarebytes, says the new banking Trojan isn't as significant as other variants because it relies heavily on social engineering to get someone to open an infected file, "something that in our modern times of security awareness isn't as successful as it used to be." However, once installed, the malware "is just as dangerous as other variants currently in the wild."
Still, accountholders can be fooled through this latest social engineering scheme, so institutions must continue to educate their customers about phishing threats, experts say.
How It Works
To launch an attack, criminals send a spam message with a Word document attached that contains the Dridex malware, Trend Micro explains in a blog. If a user opens the Word document, they must enable the macro feature, which is disabled by default, in order for the malware to be downloaded. Some malicious attachments state that the content will not be visible unless the macro feature is enabled, Trend Micro says.
Once downloaded, Dridex monitors for activity related to online banking. The malware then performs information theft through such methods as form grabbing, screenshots and site injections, Trend Micro says.
By collecting online banking data, cyber-attackers can access bank accounts and transfer funds to their own accounts, Enigma Software, a cybersecurity firm, says in a blog. "[Like] any Trojan infection, Dridex is a highly harmful infection that must be removed upon detection," the company says.
Top Countries Affected by Dridex
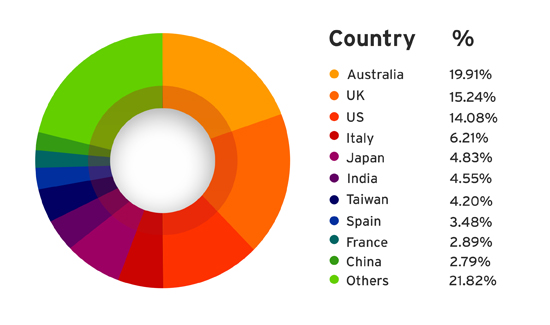
Source: Trend Micro
Analyzing the Malware
Attackers are looking to circumvent both end-user and business defense mechanisms by crafting the phishing message to sound like it is of financial importance, Sherry says. In addition, many organizations and end-user devices don't usually block Word documents. "The attackers are counting on this, coupled with the fact that nearly a third of end users' PCs across the globe don't even have any form of anti-malware on their devices," he says.
Dridex also uses an older tactic of infection by attaching a Word document that utilizes macros to install malware, Kujawa says. "However, once new versions of [Microsoft] Office came out and users generally updated, such a threat subsided because it was no longer simple to infect a user [with] this method," he says. That's because the default setting nowadays is to require the user to accept the use of macros.
Banking institutions need to educate their customers about scams involving social engineering, including phishing, says Al Pascual, a fraud and security analyst at the consultancy Javelin Strategy and Research. "To encourage the necessary security behaviors on the part of accountholders, banks should prominently display comprehensive and current educational messaging, to be accompanied by direct notification on high-profile issues," he says.
Prevention Strategies
The adoption of sandboxing helps mitigate this type of malware threat, Sherry of Trend Micro says. "Sandboxing allows for e-mails to be placed in 'padded cells' to truly detonate and see the end goal of the campaign before sending [them] off to the end user's mailbox," he says.
Sherry also recommends that end users and corporations alike "turn on the specific Microsoft Word macro security features to help defend against this particular exploit."
Dridex, although it's relatively new, is routinely detected by major anti-virus products, Kujawa says. "Keeping an up-to-date anti-virus is the best bet," he says. "Utilizing common security practices in regards to phishing e-mails is also a top defense."






















