Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Despite Doxing, OilRig APT Group Remains a Threat
Researchers Describe What They've Learned From Data Dump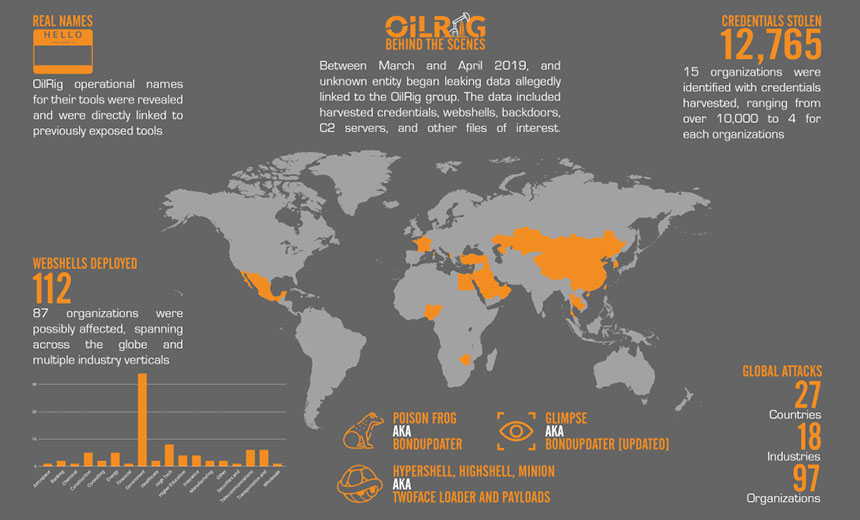
Despite a doxing of its targets and tools in March, the advanced persistent threat group known as OilRig remains a significant threat to governments and businesses, researchers at Palo Alto Network's Unit 42 report.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
The dumping of source code, malicious tools and a list of target victims on Github and Telegram in mid-March has given security researchers the ability to gain greater insights into OilRig, which has been in operation since at least 2016 (see: Leak Exposes OilRig APT Group's Tools).
And while not as sophisticated as some other APT groups, OilRig has been prolific, stealing about 13,000 credentials over the last three years, spreading out from the Middle East to other parts of the globe, and deploying a number of malicious tools, including over 100 web shells for creating backdoors and communicating with compromised systems, Unit 42 researchers report.
Now that some of its methods and targets have been exposed, OilRig is likely to deploy new tools and to keep its operations going, according to Unit 42 researchers Bryan Lee and Robert Falcone.
"While we haven't observed any known OilRig attacks since the leak, that is not indicative of whether OilRig is still in operation or not," Lee and Falcone tell Information Security Media Group. "There is no way of knowing what they may do moving forward, whether that is regrouping, changing their methodologies, shutting down their current operations or even continuing as they were. Generally, we expect an adversary that has had this level of operational data publicized to - at the minimum - develop new tools."
Learning From Leaks
In March, a group calling itself Lab Dookhtegan started leaking tools and lists of targets belonging to OilRig. Since then, Unit 42, which has tracked OilRig since 2016, has been verifying the data and looking for additional insights into the APT group.
OilRig, also known as APT34 and HelixKitten, has targeted organizations in many sectors, including government, news media, energy, transportation, and logistics and technology service. All this is part of an ongoing spying and espionage operation, with the threat actors gathering more information and credentials in order to penetrate deeper into whatever networks they target, the Unit 42 researchers say.
By studying the web shell tools the group uses to communicate with compromised servers, Unit 42 has found that the APT group has not only been active in the Middle East, but also in China, parts of Europe and Africa. It also appears that some of the tools have been used against targets in the U.S., although it's not known if these operations were successful.
Unit 42 researchers found "nearly 13,000 stolen credentials, over 100 deployed web shells, and roughly a dozen backdoor sessions into compromised hosts across 27 countries, 97 organizations and 18 industries," according to an analysis published April 30.
Other data in the dump includes command-and-control server components of backdoor tools, scripts to perform DNS hijacking, documents identifying specific individual operators and screenshots of OilRig operational systems, the analysis found.
While OilRig does not use sophisticated tactics, techniques and procedures, Lee and Falcone note that the scale of the operation is much larger than previously known.
"The scale of the operation is certainly much wider than expected, but not necessarily surprising," Lee and Falcone note. "OilRig is still not a particularly sophisticated actor, but they do seem open to using less well-known TTPs to execute their attacks. They have deviated very little from their playbooks over the last several years, which may suggest these TTPs are highly effective."
Even after the unusual doxing by Lab Dookhtegan, researchers believe that OilRig will continue its operations, likely changing its tactics, techniques and procedures and perhaps reconstituting under a different name.
Malicious Tools
While the Unit 42 analysis does not draw a specific conclusion about the nation-state that backs OilRig, a 2018 report from the United States National Counterintelligence and Security Center tied the group to Iran.
Unit 42's analysis provides a much deeper look at some of the tools that OilRig has used. These include Glimpse, which is an updated version of BondUpdater - a PowerShell-based Trojan first discovered by FireEye.
The researchers say OilRig also used PoisonFrog, a backdoor that's an older version of the BondUpdater Trojan, as well as Hypershell, a newer version of the TwoFace web shell toolset that enables the attackers to gain remote access to a network.
The analysis of these tools, combined with the list of targets, provides insight into the scale of OilRig's operations and the group's focus on stealing credentials, which gave it the ability to move laterally through networks and focus on compromising Exchange servers, the Unit 42 researchers say.
"The most interesting aspect of the data dump was the wide scale of attacks OilRig had been carrying out over time, affecting multiple regions of the world," Lee and Falcone add. "The dump allowed us to gain additional insight into the operational side of OilRig's tools and really showcased their emphasis on stealing credentials and moving laterally to attack exchange servers."
Ties to DNS Attacks
Over the years, OilRig has taken advantage of some of the weaknesses found in DNS, an older protocol that acts as the "phone book" for the internet by taking domain names and translating them into a numeric code.
Because DNS was designed when the internet was still in its early stages, it has a number of security flaws that attackers have leveraged. For instance, OilRig uses DNS tunneling to communicate between the victim and the group's command-and-control servers. This is also the method for delivering Trojans to the target systems.
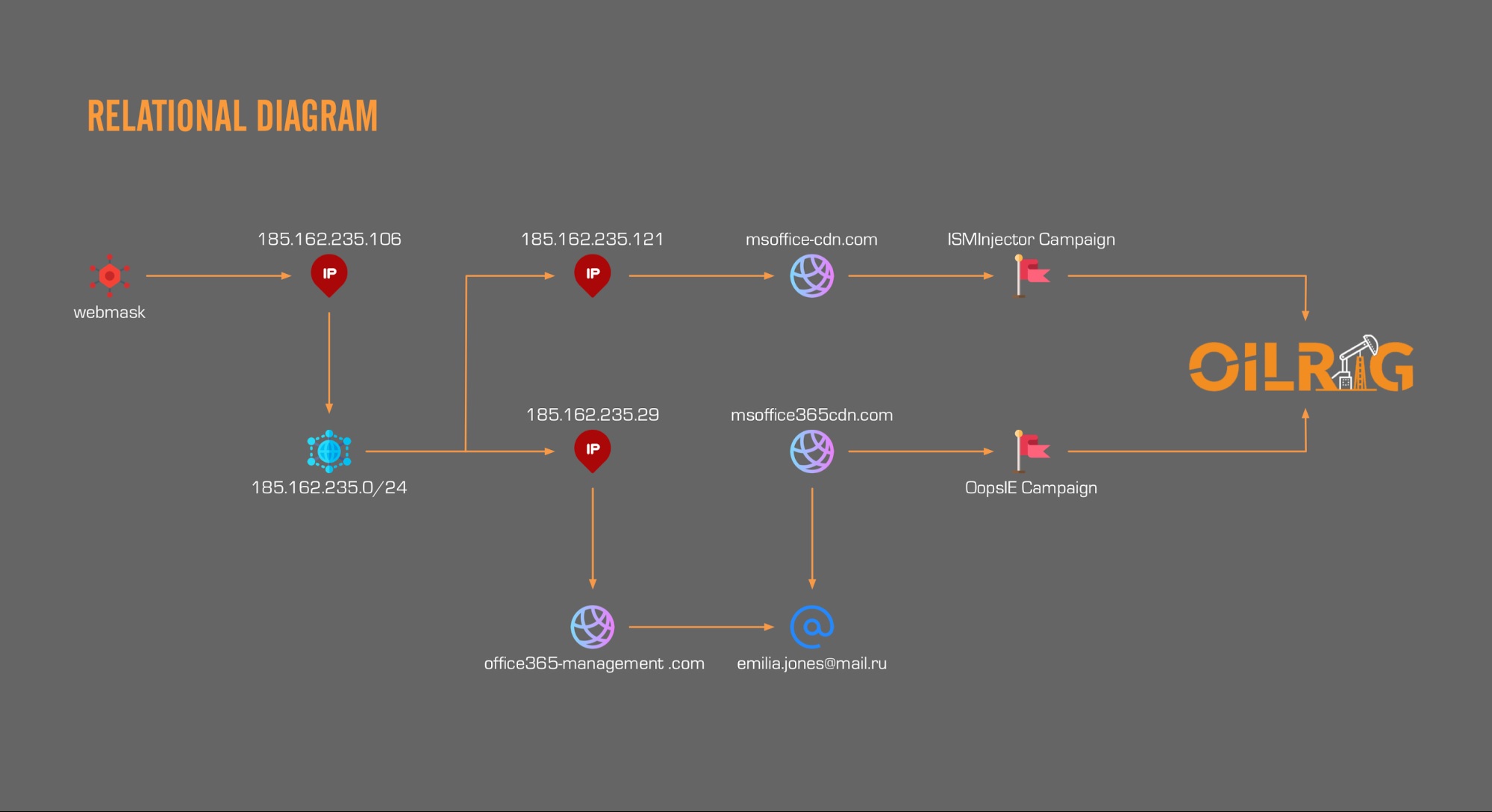
In 2018, Cisco Talos first described a DNS attack called DNSpionage. This particular campaign used malware to compromise individual endpoints, but the group behind it also hijacked DNS entries of government agencies in order to redirect visitors to specific malicious systems.
Despite analysis by Talos, CrowdStrike and FireEye, researchers could not specifically tie DNSpionage to a particular group. In the OilRig dump, however, Unit 42 found a tool called webmask, which appears to be a series of scripts specifically meant to perform DNS hijacking. Additionally, researchers found a file called "guide.txt," which offers instructions on how to carry out a DNS attack.
These tools and instruction guides were both used by OilRig and the group behind DNSpionage.
A deeper examination by Unit 42 also uncovered similarities between the infrastructure that OilRig uses for its attacks and the one used by the group behind DNSpionage. Although there is no definitive tie between the two, these similarities illustrate the reach OilRig has gained, the researchers say.
"Although we are unable to say with certainty that the DNSpionage operations were absolutely executed by the OilRig group, it is possible based on the provided data that there may be some level of relationship between them," according to the Unit 42 analysis.




















