Cybercrime , Fraud Management & Cybercrime , Ransomware
Data Breach Extortion Campaign Relies on Ransomware Fear
Scammers Look to Trick Victims Into Paying Without an Actual Breach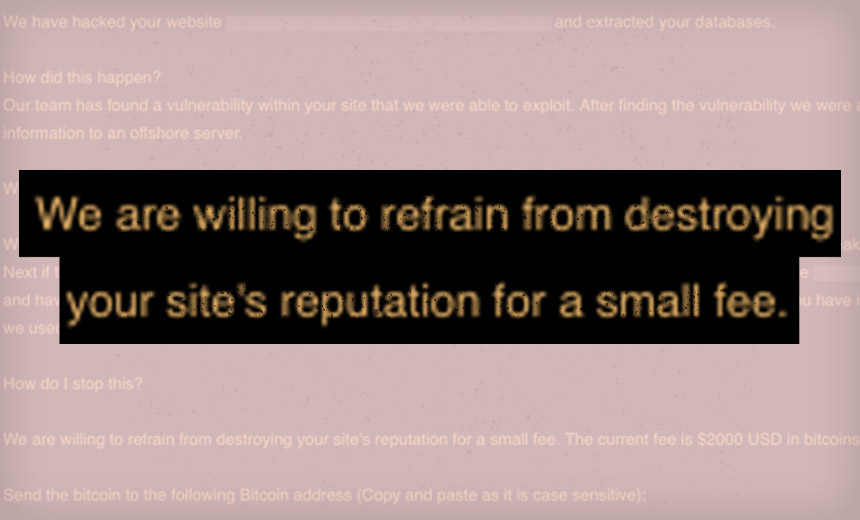
Scammers are looking to capitalize on the extortion campaigns being conducted by the Maze ransomware gang and others by demanding thousands of dollars in ransom to not release data they claim to have exfiltrated from their target when in fact no attack took place and no data was removed, according to security firm WebARX.
See Also: OnDemand | A Master Class on Cybersecurity: Roger Grimes Teaches Data-Driven Defense
The scammers have been attempting this ruse over the last few months, seeking to extort payments of $1,500 to $3,000 paid in bitcoin.
The claim made on ransom notes, according to a new WebARX report, is: "Please forward this email to someone in your company who is allow to make important decisions! We have hacked your website and extracted your databases."
WebARX’s investigation determined that about five victims have fallen for this scam so far. It's not clear when this particular fraud scheme started, but it remains active, according to the report.
"One of the wallets linked to the attack has received close to $2,000 worth of payments in bitcoins. Another wallet used in this scam, which has not yet received payments, has already been reported for abuse 81 times," WebARX reports.
Capitalizing on a Trend
These new extortion attempts are rooted in the latest trends set by ransomware threat actors. In late 2019, Maze led a major transformation of how ransomware gangs function when it began exfiltrating data from its victims and then threatened to make the data public if the ransom was not paid. Many other gangs quickly adopted the same extortion tactic (see: Maze Promotes Other Gang's Stolen Data On Its Darknet Site).
James McQuiggan, security awareness advocate with security firm KnowBe4, offers advice on dealing with scammers who have not actually exfiltrated data.
"From a technology standpoint, the IT department can review and determine if their statements are accurate,” he tells Information Security Media Group. “With this type of scam, it will be prudent to verify their claim and search for any unauthorized attempts, verify user accounts and make sure there are not any external exploitable threats against your website.”
McQuiggan recommends teaching employees how to recognize social engineering schemes.
"Social engineering is all about deception based on information that you may not possess. These emotional lures, combined with limited understanding of how to verify their claims, may cause organizations to fall victim to these types of scams," McQuiggan notes.
Mollie MacDougall, head of Cofense Intelligence, offers a similar perspective.
“We have seen ransomware campaigns where data exfiltration was claimed and the ransomware deployed included no exfiltration mechanism whatsoever,” she says. “If a criminal is alleging to have your sensitive data, you should first identify evidence that they have your data, or that exfiltration from your network has occurred.”