Cryptocurrency Fraud , Cybercrime , Fraud Management & Cybercrime
Cryptomining Worm Now Targets Web Apps, IoT Devices
Researchers: Malware Uses New GitHub Repository, Mines for Monero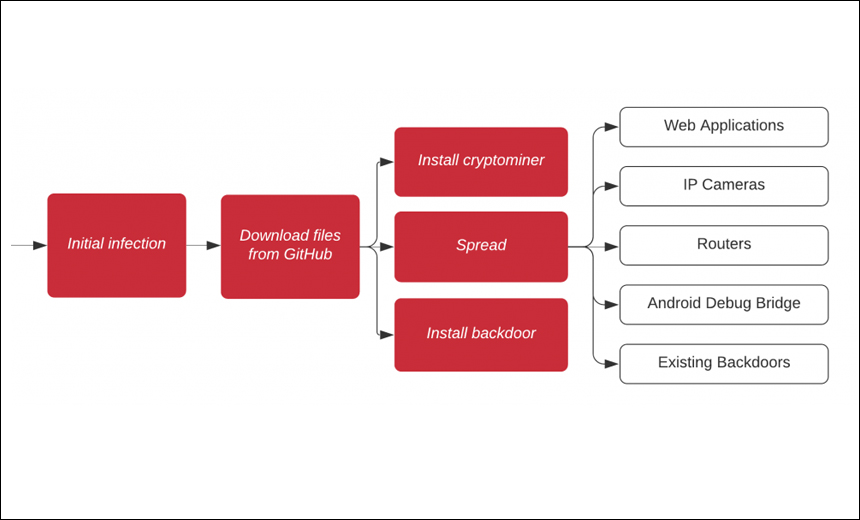
A previously documented cryptomining worm dubbed Gitpaste-12 has returned with a wide-ranging series of attacks targeting web applications and IoT devices that exploit at least 31 vulnerabilities, according to a Juniper Threat Labs.
See Also: The State of Ransomware Readiness 2022
The botnet, which was uncovered in October by Juniper researchers, originally targeted vulnerable Linux applications as well as IoT devices, according to the report. The operators behind Gitpaste-12 were also using legitimate services, such as GitHub and Pastebin, to help hide the malware's infrastructure (see: Botnet Operators Abusing Legit GitHub, Pastebin Resources).
The initial wave of Gitpaste-12 attacks started in July but was not uncovered until October, when the GitHub repository that was hosting the bulk of the worm's payloads was removed. On Nov. 10, the Juniper researchers discovered a second round of attacks had started, according to the report.
The Juniper analysis notes that seven of the vulnerability exploits found in the latest version were ported over from the previous Gitpaste-12 sample. The worm also attempts to compromise open Android Debug Bridge connections and existing malware backdoors.
"The [latest] wave of attacks used payloads from yet another GitHub repository, which contained a Linux cryptominer ('ls'), a list of passwords for brute-force attempts ('pass') and a statically linked Python 3.9 interpreter of unknown provenance," the researchers note in the report.
The Juniper analysis also notes the latest version contains a cryptomining tool that mines for monero virtual currency, as was the case in the earlier version.
GitHub has taken down a section of its platform used to host the malicious worm, which slowed its spread, the researcher say.
Initial Attack
The Juniper researchers who examined the second wave of attacks also found a repository of new attacks vectors in one of the malware's variants that they examined.
That variant, which the researchers call 10-inix, is a UPX-packed binary written in the Go programming language and compiled for x86_64 Linux systems. The repository contained the 31 vulnerabilities that the worm would look for, according to the report.
Many of the vulnerabilities exploited are new, with public disclosures and proof-of-concept exploits dated as recently as September, the researchers say.
Although the X10-unix attacks vary depending on the operating systems and architectures targeted, each of these attacks tries to install the monero cryptomining malware, install the appropriate version of the X10-unix worm and open a backdoor that listens for instructions on ports 30004 and 30006, the report notes.
X10-unix also attempts to connect to Android Debug Bridge connections on port 5555, according to the report.
"While it's difficult to ascertain the breadth or effectiveness of this malware campaign, in part because monero - unlike bitcoin - does not have publicly traceable transactions, [Juniper Threat Labs] can confirm over a hundred distinct hosts have been observed propagating the infection," the researchers note.
Other Botnet Activity
Other researchers have also noted several new botnets that target vulnerable Linux-based devices as well as IoT devices.
In May, for example, researchers uncovered a botnet dubbed Kaiji that uses brute-force methods targeting the SSH protocol to infect endpoints, which also allows it to launch distributed denial-of-service attacks (see: Kaiji Botnet Targets Linux Servers, IoT Devices).
In October, researchers at security firm Avira Protection Lab identified a new strain of the Mirai botnet targeting vulnerable IoT devices (see: Even in Test Mode, New Mirai Variant Infecting IoT Devices).






















