Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management
Crime Gang Advertises Stolen 'Anti-Virus Source Code'
Researchers: 'Fxmsp' Russian Hacking Collective Exploits Victims Via RDP and Active Directory
A hacker collective has been advertising source code that it claims to have stolen from three top U.S. anti-virus software development firms, security researchers warn.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
Newly launched New York-based fraud prevention and risk management firm Advanced Intelligence - also known as AdvIntel - says the hacking gang, called "Fxmsp," has been involved in previous high-profile breaches. "Our subject matter experts assess with high confidence that Fxmsp is a credible hacking collective that has a history of selling verifiable corporate breaches returning them profit close to $1 million," the firm says in a research report.
Since April 24, Fxmsp has been claiming to have gained remote access to the networks of three U.S.-based anti-virus firms after working nonstop for months to hack them, AdvIntl says. The hacker collective is offering access to the firms' networks and source code for $300,000.
Advanced Intelligence says the gang has shared screenshots of stolen information, claiming that they have stolen 30 TB of data and that the identities of the three hacked firms can be deduced from these screenshots. "The folders seem to contain information about the company's development documentation, artificial intelligence model, web security software and anti-virus software base code," it says.
"Fxmsp has only provided us with files for one company, which were debugging files, but had references to the source code," Yelisey Boguslavskiy, director of research at AdvIntel, tells Information Security Media Group. "They claim that such a format was chosen by the company itself as a security measure and these files are sufficient to reverse the actual source code."
He says the alleged intrusions and source code theft have been reported to authorities, who have disseminated the information to the allegedly hacked anti-virus firms. Boguslavskiy declined to name the three anti-virus firms, at least at the moment, citing an ongoing law enforcement investigation.
This isn't the first time that Fxmsp has come to security researchers' attention. "Throughout 2017 and 2018, Fxmsp established a network of trusted proxy resellers to promote their breaches on the criminal underground. Some of the known Fxmsp TTPs [tactics, techniques and procedures] included accessing network environments via externally available remote desktop protocol (RDP) servers and exposed Active Directory," AdvIntel says in the research report.
Several security research firms have reported that Fxmsp was also advertising remote access to a hotel chain's systems last year.
Boguslavskiy says whoever is behind Fxmsp appears to speak both Russian and English, specialize in social engineering, has been operating since the mid-2000s, and regularly hacks into firms via remote desktop protocol - RDP - as well as poorly secured Active Directory implementations.
"Most recently, the actor claimed to have developed a credential-stealing botnet capable of infecting high-profile targets in order to exfiltrate sensitive usernames and passwords. Fxmsp has claimed that developing this botnet and improving its capabilities for stealing information from secured systems is their main goal," AdvIntel says.
Boguslavskiy says the alleged anti-virus vendor breaches appear to be both proof of concept as well as meant to better market the gang's own services. "Fxmsp claimed that their team was interested in researching the security capabilities of cyber defense systems to integrate these findings and upgrade their botnet," he says. "When they disappeared for a half year and then re-emerged with this offer [two weeks ago], claiming that they have been working on breaching AV systems for all this time, this all seemed very congruent with their previous claims."
Source Code Exposure: What's the Risk?
The alleged theft of source code is a reminder that even vendors of information security products and services can potentially be hacked (see: Yes Virginia, Even Security Software Has Flaws).
"I would expect, and hope, that the anti-virus company's developers' network is segregated and isolated from their production and operational networks," Brian Honan, who heads Dublin-based cybersecurity consultancy BH Consulting, tells ISMG.
But what's the risk posed if source code for security products gets stolen?
"It's an interesting one because if you have the source code, there may be commercial damage in that people can copy it, but does it pose a security risk? Well, yes, to an extent," says Alan Woodward, a professor of computer science at the University of Surrey.
"First, if someone has the source code there is always the possibility that they may find a security flaw. Even without a direct flaw there are sometimes ways around security features which, although security through obscurity is no real security at all, having the source code can give you a head start," Woodward tells ISMG.
"Second, if someone can get into the companies' servers and steal the crown jewels like this, it is bound to make people wonder what else they may have done whilst inside the system. Could they have altered the source code? Could they have planted some form of Trojan that doesn't affect the main functionality but adds something of their own? In any event, if the source code is real, and was truly stolen by breaking into the systems, it will make users suspicious of how secure that company really is - both looking after their own assets and the security they provide to secure the assets of others."
Honan says another consideration would be the age of the allegedly stolen code. "If true, then consideration needs to be given to how up to date the software is. If the copies of code are old, then they may not provide much insight into how the anti-virus software works," he says. "If the source code is legitimate and up to date, criminals could use the source code to look at how it works and develop ways in their malware to try and evade the affected AV software."
Remote Access Concerns
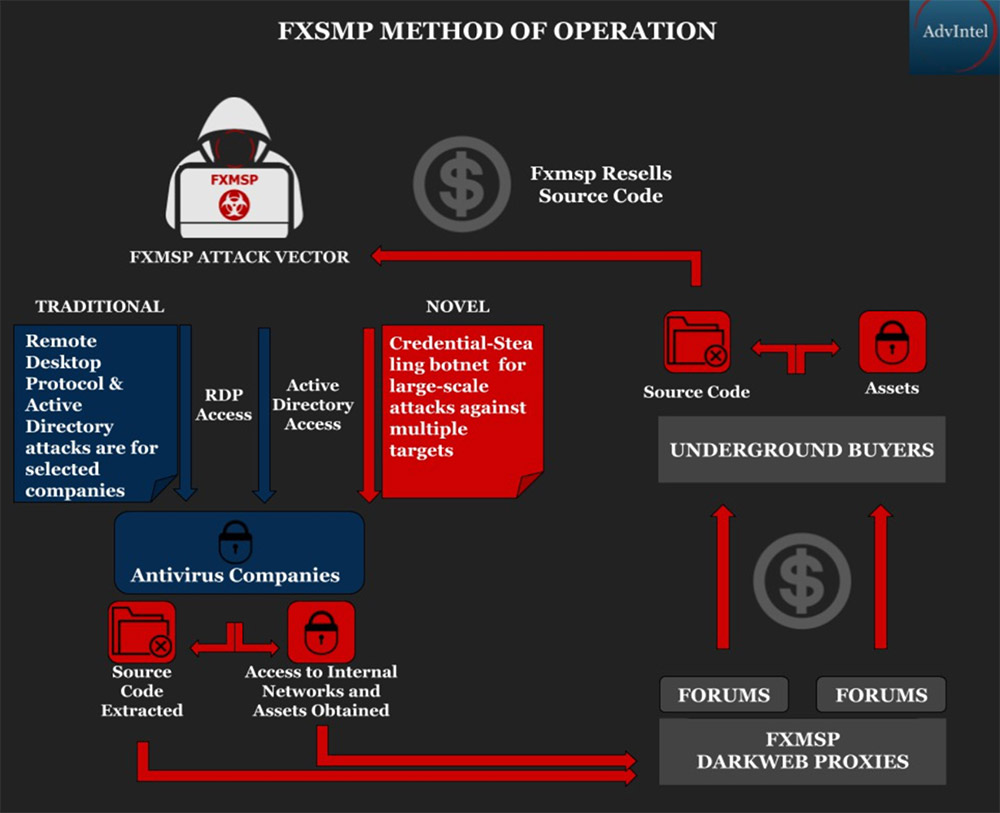
Woodward notes that Fxmsp's claim to have remote access to anti-virus vendors' networks, if true, is especially concerning.
"If they are offering network access. it suggests that they did break into the company's network and they have left a little something behind to enable them to break in in future," he says. "That would be the worst of all worlds as, if true, it means the company has an ongoing security issue about which it doesn't know. That rings all sorts of alarm bells."
Regardless, Honan says anti-virus firms, like all software developers, should have controls in place to prevent such tampering.
"The source code should be regularly checked and sanitized by the anti-virus vendors to ensure no malicious code has been inserted into the source code, so that reduces the risk," says Honan, who's also a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol.
But not all organizations take such precautions. The 2017 NotPetya wiper malware attack, for example, exploited a Ukrainian-based accounting software provider's systems and then used its own software update server to infect numerous organizations.
Potential Exploit Vector: Active Directory
Boguslavskiy says that at least one of the anti-virus firms appears to have been compromised via its Active Directory implementation and persistent access maintained via RDP.
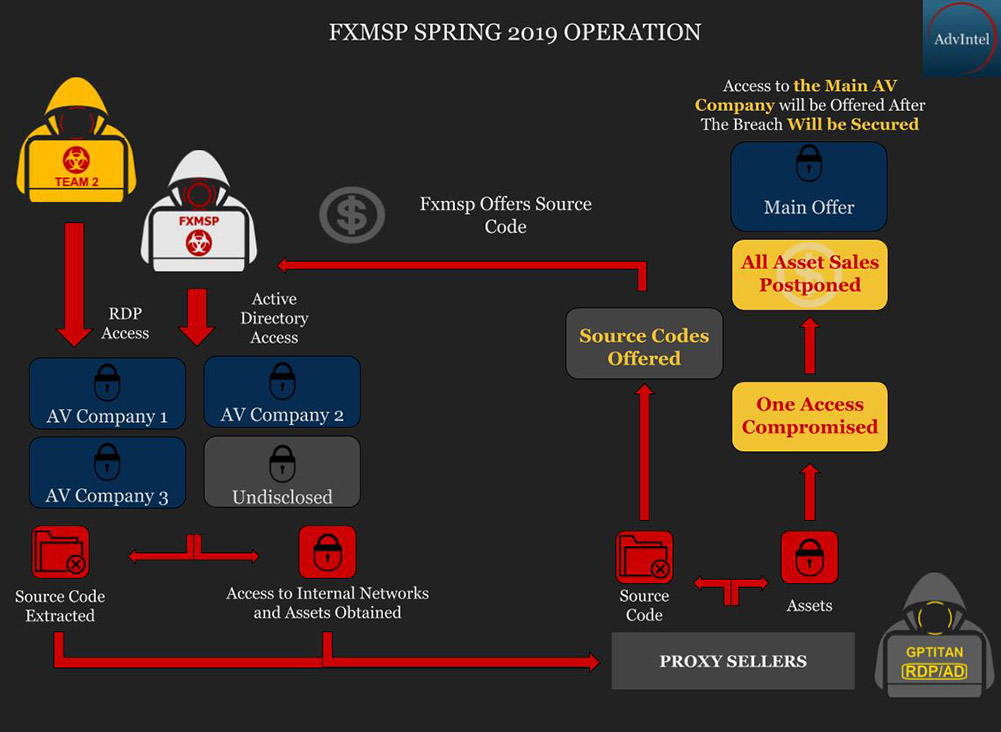
Huy Kha, an information security professional at a Dutch law firm who's an expert on Active Directory security, says that the image that has been obtained from Fxmsp appears to show a Windows Active Directory domain controller - specifically, for Windows Server 2012 R2.
Kha tells ISMG that attackers will often target victims with Word documents with macros designed to give them remote access to a work station. At that point, they often try to exploit the built-in, Active Directory local administrative accounts on domain-joined computers, he says, to gain access to other systems and move across the network.
"After gaining access, the attacker could also have enabled RDP over the internet on the Active Directory Domain Controller to obtain ongoing access," he says.
"Compromising AD means that attackers can get access to all the different user accounts and other company systems."
Story updated with comment from Huy Kha.





















