Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Credit Card Theft Ringleader Pleads Guilty
FIN7 Gang Tied to Theft of 15 Million Payment Cards From Restaurant Chains and Others
One of the three Ukrainian men charged with leading the notorious FIN7 hacking group, which prosecutors say stole 15 million payment cards, has pleaded guilty to two federal charges.
See Also: OnDemand | API Protection – The Strategy of Protecting Your APIs
Fedir Hladyr, 34, pleaded guilty on Wednesday to conspiracy to commit wire fraud, which carries a maximum 20-year prison sentence, and conspiracy to commit computer hacking, which carries up to a five-year penalty, according to the court documents. He also agreed to pay up $2.5 million in restitution.
In exchange for his guilty plea, federal prosecutors will drop the other charges included in the indictment. Hladyr remains in federal custody in Washington. His attorney, Arkady Bukh, says that his sentencing will likely take place next year.
Bukh tells Information Security Media Group that he plans to ask the court to sentence Hladyr to time served. He called Hladyr a "great computer analyst" who made serious mistakes.
Tracking FIN7 Leaders
At its height, the FIN7 group sent hundreds of spear-phishing emails that targeted hospitality businesses, casinos and restaurant chains in order to steal credit card data, according to federal prosecutors. The gang allegedly stole at least 15 million payment card records from U.S. businesses, resulting in over $100 million in losses over three years, court records show (see: Feds Announce Arrests of 3 'FIN7' Cybercrime Gang Members).
The U.S. Justice Department unsealed an indictment in August 2018 charging the alleged FIN7 leaders with various crimes. Hladyr was arrested in Germany and extradited to the U.S., according to the FBI. The other two alleged leaders of the hacking group, Dmytro Fedorov and Andrii Kolpakov, were later arrested in Europe.
Kolpakov is also in custody in the U.S. and has pleaded not guilty to the charges against him, with a trial date set for October 2020, according to court records. Records don't offer details on Fedorov.
Dozens of hackers worked for FIN7 between August 2015 and January 2018, prosecutors say. Hladyr held the title of systems administrator for the gang's front company, which called itself Combi Security, according to court documents.
One of Hladyr's main responsibilities was overseeing the command-and-control servers FIN7 used to deliver the malware that would help steal the credit card data from companies and point-of-sale machines. Over three years, Hladyr gained more responsibility, according to documents filed for his guilty plea.
"Among other things, he was responsible for aggregating stolen payment card information, providing technical guidance for FIN7 members, issuing assignments to FIN7 hackers, and supervising teams of hackers," according to court documents. "The defendant routinely relayed orders from FIN7's top-tier leadership to other members of the group."
Hladyr was paid about $100,000 over three years for his FIN7 work, the documents show.
Far-Reaching Campaign
FIN7 targeted dozen of business, including the restaurant chains Arby's, Chili's, Chipotle Mexican Grill, Jason's Deli, Red Robin Gourmet Burgers, Sonic Drive-In and Taco John's, according to the FBI.
Through a network of hackers mostly in Eastern Europe, the gang created spear-phishing emails designed to resemble legitimate messages, such as catering orders or reservation details. Those emails often contained malicious attachments, which, if opened, infected the company's computers, according to security analysts (see: The Art of the Steal: FIN7's Highly Effective Phishing).
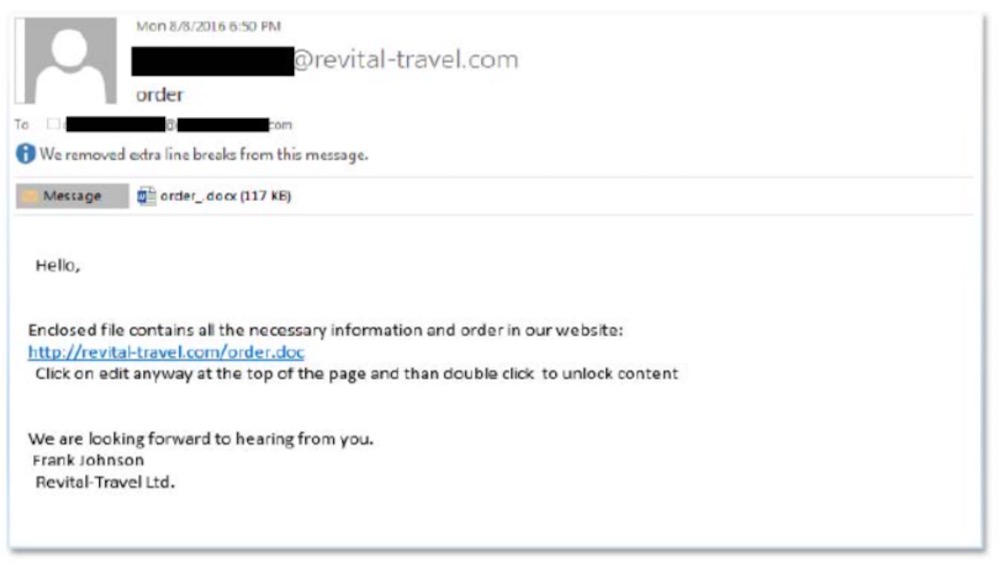
Gang members would typically call the targeted company to ensure that someone got the messages, and also digitally sign malware to help it evade security tools, prosecutors say.
The initial phishing email and malicious attachments enabled FIN7 to open a backdoor into a victim's network, and hackers could then move laterally through the infrastructure, spread additional malware and locate financial data and other sensitive documents, according to the court documents.
The gang also infected point-of-sale machines with malware. "FIN7 then used the malware to scrape and exfiltrate the payment card information," according to Hladyr’s guilty plea documents.
Once the FIN7 group had the credit or payment card number, the name of the cardholder and the ZIP code, the stolen data was packaged and sold on dark net forums, including Joker Stash, the court records show. At one point, Chipotle reported nearly 4 million payment card records stolen, while Jason's Deli had nearly 2 million records compromised, prosecutors say.
Other Gangs
Although federal prosecutors indicted the three leaders of FIN7, it's not clear what happened to the other hackers who participated in the scheme.
Some security researchers, including experts at FireEye, have noted similarities between FIN7 and another financially motivated gang that experts refer to as FIN8, which has targeted point-of-sale machines in the hotel industry in an effort to steal credit card and other payment data (see: FIN8 Group Returns, Targeting POS Devices With Malware).
FIN7 and FIN 8 used similar techniques, including malicious tools to bypass network filters and data loss prevention solutions, security researchers note.
Another hacking group, called FIN6, has also been more active lately, branching out from stealing and selling payment data to distributing ransomware, according to FireEye researchers (see: Report: FIN6 Shifts From Payment Card Theft to Ransomware).






















