Business Continuity Management / Disaster Recovery , Cybercrime , Cybercrime as-a-service
Coca-Cola Investigating Data Breach Claim
Stormous Ransomware Group Says It Exfiltrated 161GB of Critical Data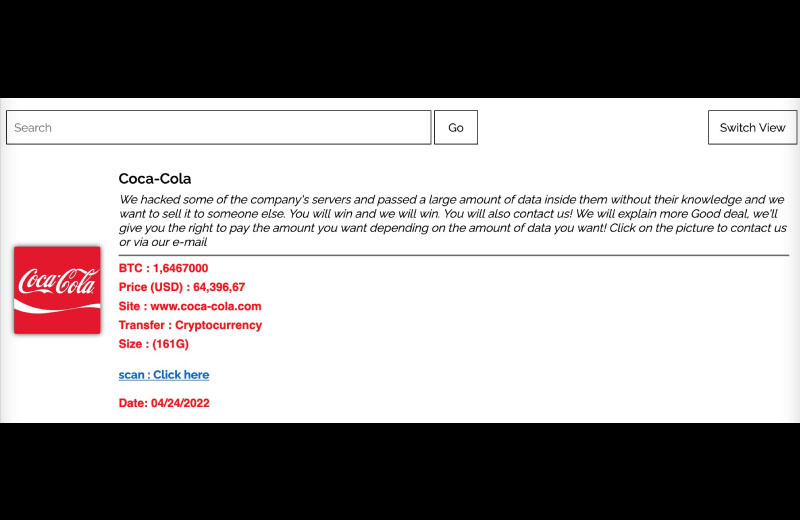
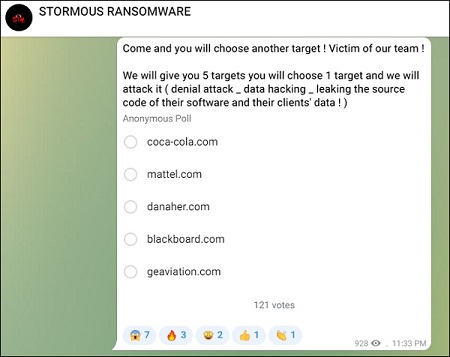
On April 19, Russia-supporting ransomware group Stormous polled its Telegram subscribers, asking for their opinion on which company data it should release next. It now appears that Coca-Cola received the most votes; the cybercriminal group on Monday posted on its Telegram page that it has breached and exfiltrated 161GB worth of critical data from the beverage manufacturing giant.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
Other companies included in the April 19 poll were toy company Mattel, American conglomerate Danaher, EdTech company Blackboard and aircraft engine supplier GE Aviation.
While Mattel, Danaher, Blackboard and GE Aviation did not respond to ISMG's request for information on whether they had detected any unauthorized network access, Coca-Cola confirmed that it was investigating the claim.
"We are aware of this matter and are investigating to determine the validity of the claim. We are coordinating with law enforcement," the company's vice president of communications, Scott Leith, tells Information Security Media Group.
In response to Coca-Cola's statement, Stormous, on its Telegram page, says: "The breach exists and you can check it in several ways!"
"The company says it is investigating the breach of its data by us! We say you've already been hacked! As well as [we have stolen your] files in complete secrecy! Sorry, we don't want you to say like a previous victim (IBM Corporation) that this is a breach that hasn't affected your company significantly. Tell [us your] offer [and] contact us! We can find a solution and publish some data for [you] to be more confident (even though [the company] knows it has been hacked!)," the Telegram post says.
Coca-Cola did not respond to ISMG's request for information about whether any of its trade secrets had been stolen.
Stormous' Claims
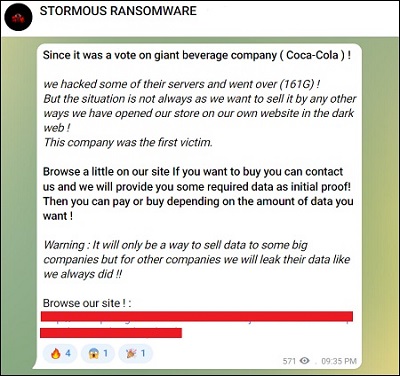
In a post on Monday, Stormous ransomware said it had breached Coca-Cola. This post contained a link to the group's dark web site, where it shared contact details for interested purchasers. It also mentioned that, starting with Coca-Cola, the group will now begin to sell stolen data of "some big companies" via a storefront.
CryptoInsane - an alias for David Montenegro, who says on Twitter that he is a security researcher - describes how Stormous offers details of the Coca-Cola breach on its dark web site, including its ransom demand in Bitcoin, the size of the leak and an advertisement offering a "good deal" for those interested in buying the data. "We'll give you the right to pay the amount you want depending on the amount of data you want," his tweet, citing the Stormous post, says.
CryptoInsane's tweet, showing what appears to be a screenshot of Stormous' dark web post, shows folders named financial, media, hardware, network, payments, email, passwords and admin. It is unclear if these files can be opened and viewed, but a total of 13 files whose aggregated size comes to approximately 161GB - the amount the group claims it stole - have been listed on its site, according to the image in CryptoInsane's tweet.
Stormous Ransomware - Coca-Cola
— CryptoInsane (@CryptoInsane) April 25, 2022
BTC : 1,6467000
Price (USD) : 64,396,67
Transfer : Cryptocurrency
Size : (161G) pic.twitter.com/fQEejLurfN
Stormous initially said it has priced the Coca-Cola data at 1.6467 Bitcoin, which is currently valued at just under $65,000. However, according to an update posted on its Telegram channel on April 29, the group says it is mulling doubling the ransom amount, as the beverage giant had not initiated communication with it yet.
But Stormous has not yet provided any substantial proof of data stolen from Coca-Cola. In fact, Brett Callow, a threat analyst at Emsisoft, says that the entire incident could likely be an "attention-seeking" technique from Stormous ransomware group.
Russia Supporter
On March 1, a week after the Russia-Ukraine war broke out and cyber hacktivist collective Anonymous and Ukraine's IT Army waged an offensive attack against Russian entities, Stormous also declared its allegiance to Russia on Telegram.
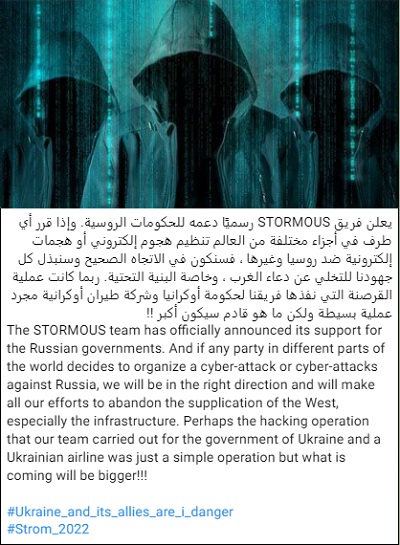
The group announced its support of the Russian government and warned the West that if any attacks were directed toward Russia, it would target Western infrastructure in retaliation.
Soon after this announcement, fast-food brands including McDonald's, Starbucks and Coca-Cola reportedly announced the withdrawal of their services from Russia. The move came amid mounting social media pressure, with users asking for a boycott of these food chains for continuing their services in Russia.
Alan Calder, CEO of U.K.-based GRC International Group, an IT governance, risk management and compliance solutions provider, tells ISMG that this halting of services from Russia could very well be the reason for the attack on Coca-Cola. Other companies, he adds, should also be on guard.
"It has been increasingly obvious that those companies that have withdrawn services from Russia, or condemned their activities, are likely to be particularly targeted. These attacks are not going to abate - particularly not if Russia continues to struggle with making progress in its kinetic activities in Ukraine," Calder says.
The Way Ahead
Coca-Cola now faces the daunting task of confirming the breach - then finding out how the breach occurred and ensuring that no backdoors or malwares were left behind, says Florida-based Erich Kron, security awareness advocate at cybersecurity firm KnowBe4.
As America supports Ukraine in the war, these attacks are not surprising, Kron says.
"[But] what is unfortunate to see is the amount of data - as much as 161GB, including sensitive information - that was moved out of the network without being noticed." This underlines the need for good data loss prevention tools in modern networks, he says.
"Ensuring that DLP is deployed and working, and that servers and devices are up to date with security patches, can significantly reduce the risk of damage if the attackers successfully gain access to the network," Kron adds.




















