Breach Notification , Business Continuity Management / Disaster Recovery , Business Email Compromise (BEC)
City Pays Ransom Despite Pre-Ransomware Outbreak Hack Alert
DoppelPaymer Hit Comes as Ransomware Attacks - and Data-Leaking Shakedowns - Surge
The attack sounds like it was ripped from a script for the television show "24": Hackers have infiltrated a government network, and they're just days away from unleashing crypto-locking code. Viewers can practically hear the countdown.
See Also: The State of Organizations' Security Posture as of Q1 2018
Unfortunately for the city of Florence, Alabama (population: 40,428), no suave secret agent swooped in to save the day. Ten days after receiving an alert that hackers were inside its systems, the city was hit by crypto-locking malware, disrupting the city's email systems and leading to an ongoing network outage.
"The city of Florence online network is currently down. We apologize for any inconvenience," the city's website read on Friday. "We will continue update you on the outage. Thank you for your patience."
Now the city council has approved plans to pay their attacker nearly $300,000 in cryptocurrency in return for the twin promises of receiving a decryption key and not seeing any city data get leaked, if indeed any got stolen, the Florence-based Times Daily reports.
"The city will continue to pursue all appropriate avenues and to take action with the best interests of our citizens in mind," the city says in a press release. "Working with the experts we engaged, we are striving to return to fully operational status in a safe and secure manner as soon as possible."
Countdown to Forced Encryption
Could the city have reacted more quickly to blunt the attack? The city said it received an alert on May 26 that it had been hit by hackers, after which it suffered a ransomware outbreak last Friday, on June 5.
Security blogger Brian Krebs on Tuesday reported that a researcher at Wisconsin cybersecurity firm Hold Security found a username and password for the city's IT manager on a cybercrime forum, suggesting that attackers had already gained a foothold inside the network. He gave the city a heads-up in late May, warning them that the city's network had been breached.
Krebs reports that attackers used a DHL-themed phishing attack against Steve Price, the city's IT manager, and successfully stole his Microsoft Windows credentials. While the city took a number of measures after receiving the May 26 alert, Price tells Krebs that the IT department was still seeking emergency funding to do a more thorough investigation. “We were trying to get another [cybersecurity] response company involved, and that’s what we were trying to get through the city council on Friday when we got hit,” Price told Krebs.
In an emergency meeting on Wednesday, the city council voted to meet the ransomware attackers' demand of 30 bitcoins, worth nearly $300,000, Times Daily reports.
Florence Mayor Steve Holt told Krebs that the city had been hit by attackers wielding DoppelPaymer - aka DopplePaymer - ransomware (see: DoppelPaymer Ransomware Slams Supplier to Boeing and Tesla). He also said that an outside security firm retained by the city, which he didn't name, had negotiated the attackers' ransom demand down from 39 to 30 bitcoins.
Missed: Window of Opportunity
Clearly, the city of Florence story looks like a missed opportunity by officials to react quickly enough.
"It would appear that they had a clear window of opportunity to respond in a robust and timely manner to the initial breach and prevent the ransom phase of the campaign," says incident response expert David Stubley, who heads Edinburgh, Scotland-based security testing firm and consultancy 7 Elements. "Unfortunately, it shows an example of why you need to respond robustly to a breach of a host and understand the capabilities of the actor and the malware."
While the city said that after the tip-off, it had found and isolated the one infected Windows system, that wasn't enough. Stubley said the investigation should have carried on much further.
"Once you understand the capabilities of the actor and the tooling in use, it is vital to assess other assets within the network as actors will look to move laterally and gain access to other systems," he says. "As such, removing just the first compromised device may not prevent sustained access to the network."
Security experts say too many ransomware victims fail to see the infection as part of what might be a much larger problem for the organization. "Should you fall victim to an attack you need to determine how the initial infection happened," says Brian Honan, who heads Dublin-based cybersecurity firm BH Consulting. "Even if you isolate your systems, rebuild them and get back online again, if you have not closed the avenue of attack - or attacks - that the criminals used then it is only a matter of time before you are a victim again."
But he says the best response is to already have a good response plan in place (see: To Survive a Data Breach, Create a Response Playbook).
"The best time for an organization to react to such an attack is now. By this I mean you should examine your incident response processes before you suffer an attack to determine how you would react to a breach caused by ransomware," Honan says. "This review should include what steps you would take, how you would minimize the impact, and what remediation actions you need to take now to prevent an attack. One area I recommend you look at is your backup strategy and how robust it is. In the event of an attack restoring from backups may be the only recourse you have."
Shakedown Du Jour: Data Leaking
In the bigger scheme, unfortunately, Florence is just the latest in a long line of victims. Indeed, Mayor Holt told the Times Daily that two other Alabama cities were hit by ransomware at about the same time as his.
The attackers who wield DoppelPaymer are one of about a dozen gangs or ransomware-as-a-service operators who not only forcibly encrypt systems, but first exfiltrate data. Then they name-and-shame victims on the site, typically followed shortly thereafter by trickling out stolen data. Their shakedown play is straightforward: Pay, and they'll immediately remove a victim's name and any leaked data from the site, as well a share a decryption tool.
Ransomware response firm Coveware reports that over the first quarter of this year, DoppelPaymer shifted to using data exfiltration in every single one of its attacks.
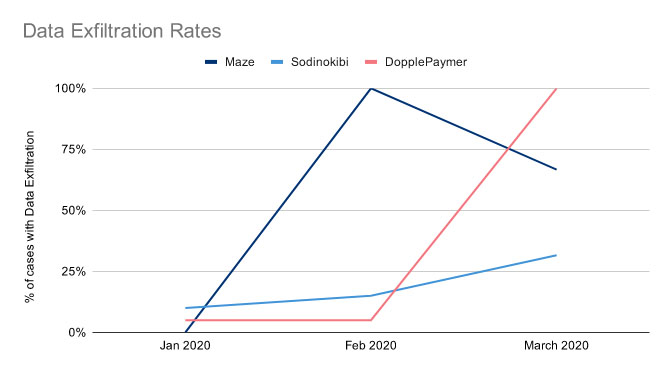
The Maze ransomware gang started the data-leaking trend in October 2019 and in short order, multiple other gangs followed suit. Security experts say the move was likely due to organizations better preparing, and less often paying ransoms. Data published by blockchain analysis firm Chainalysis, for example, suggests that overall ransom payments by victims to their attackers may have been declining.
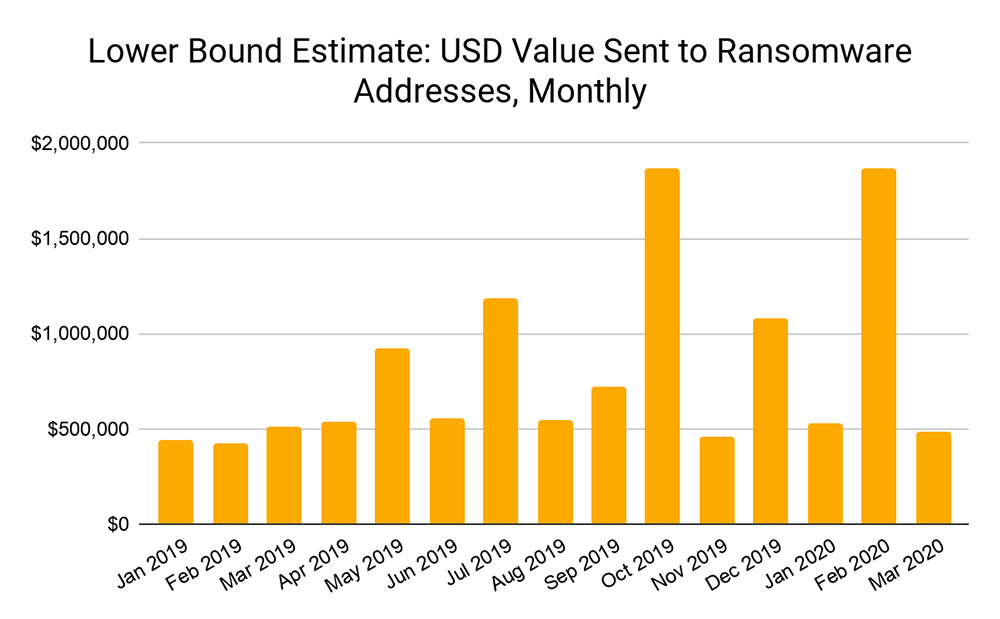
In response, many gangs have begun exfiltrating data, posting victims' names to name-and-shame sites, and leaking data, to try and force payment.
Data-Leaking Syndicates Formed
Some gangs have now formed criminal syndicates in which they leak data using another gang's site. Maze's own, so-called news site - in reality, its dedicated doxing site - recently started featuring leaked data from victims of Lockbit, which didn't have its own, dedicated data-leaking site.
On Monday, Maze also began hosting leaks from the RagnarLocker gang, which previously used the Mega file-sharing site to dump data. While that option was free, it also didn't protect the gang against having the stolen data get taken down (see: 7 Ransomware Trends: Gangs Join Forces, Auction Stolen Data).
In an unexpected move, in recent days Maze has also begun cross-posting data from one of its victims - Singapore-based defense contractor ST Engineering's subsidiary VT San Antonio Aerospace - via a leaking site run by RagnarLocker.
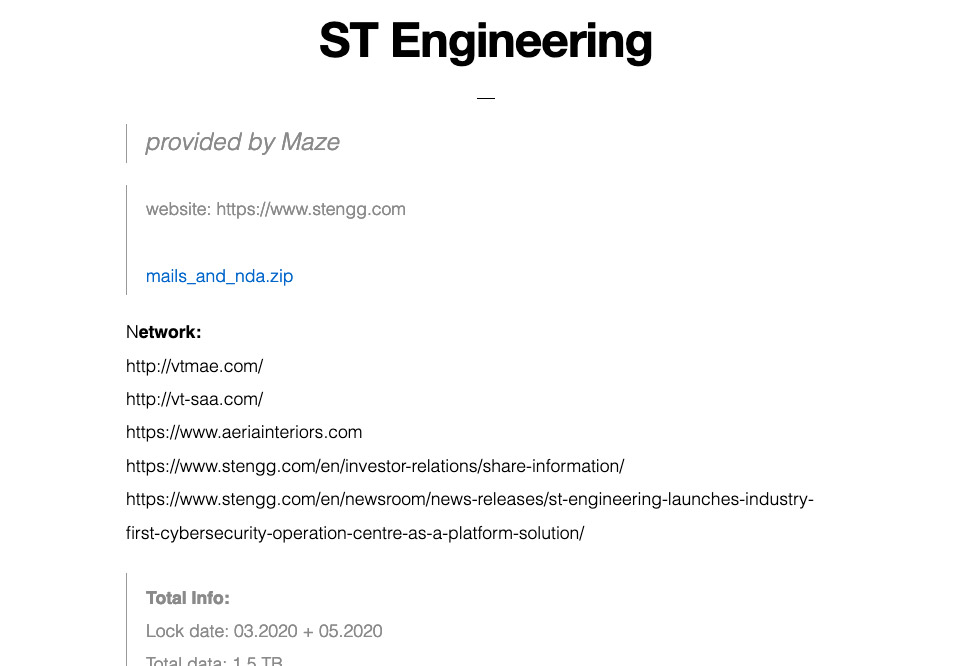
"Maze published ST Engineering’s data initially - they were responsible for the attack - and now RagnarLocker has published it. Maze previously published data that RagnarLocker had stolen," Brett Callow, a threat analyst at security firm Emisoft, tells ISMG.
But the shared efforts don't stop there. The Ransom Leaks account on Twitter, run by a security researcher who's tracking gangs' data-leaking efforts, says: "The RagnarLocker's leak site points back to Maze's leak hosting. So Ragnar is just advertising what Maze has. Very friendly-like."
Ransomware Attack Volume Increases
Attackers are continuing to double down on attacks that use crypto-locking malware, with experts warning that attackers may first spend weeks or months inside a network, looking for valuable data (see: Ransomware Attackers May Lurk for Months, FBI Warns).
Ransomware attacks surged in 2019, with 131% more organizations falling victim to such attacks throughout the year, compared to 2018, reports Beazley Breach Response Services, a unit of global insurance company Beazley. In the first quarter of this year, meanwhile, Beazley says it saw a 25% increase in ransomware attacks being reported to its response team, compared to the fourth quarter of 2019.
In recent months, in line with warnings from many cybersecurity watchers, it's also seen phishing attacks - often with a COVID-19 theme - sharply rise too.
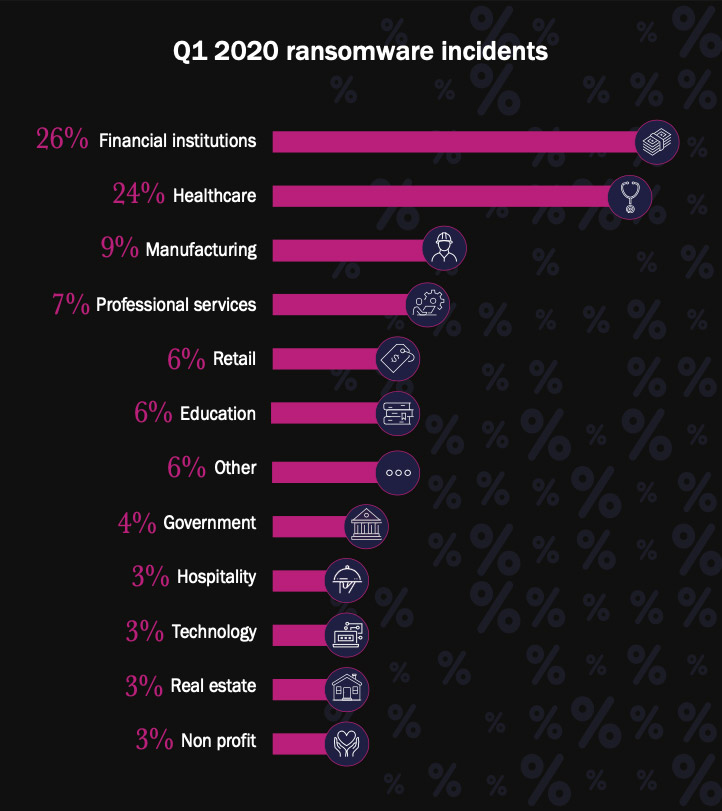
With recent ransomware attacks, hardest hit have been the manufacturing and healthcare sectors, Beazley says (see: No COVID-19 Respite: Ransomware Keeps Pummeling Healthcare).
But ransomware-wielding attackers have also continued to pummel managed service providers, it says, leading to problems for the organizations they support, especially including numerous banks, credit unions and healthcare organizations. Security experts say MSPs remain a prime target, because hacking them can give a gang direct access to the many different organizations the IT provider supports, sometimes via the provider's own remote-access tools.
To help stamp out these attacks, BH Consulting's Honan says law enforcement agencies need intelligence on who's being hit and how. "In all cases I strongly recommend contacting law enforcement and reporting the issue to them," says Honan, who's a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol. "They may not be able to help directly with the breach but any information you give them could be used by law enforcement, both local and international, to identify those behind these attacks."



















