Blockchain & Cryptocurrency , Cryptocurrency Fraud , Cybercrime
Buying Bot-Stolen Logs: Marketplaces Make It '2easy'
Genesis Market, 2easy, Russia House Offer Inexpensive Access to Stolen Credentials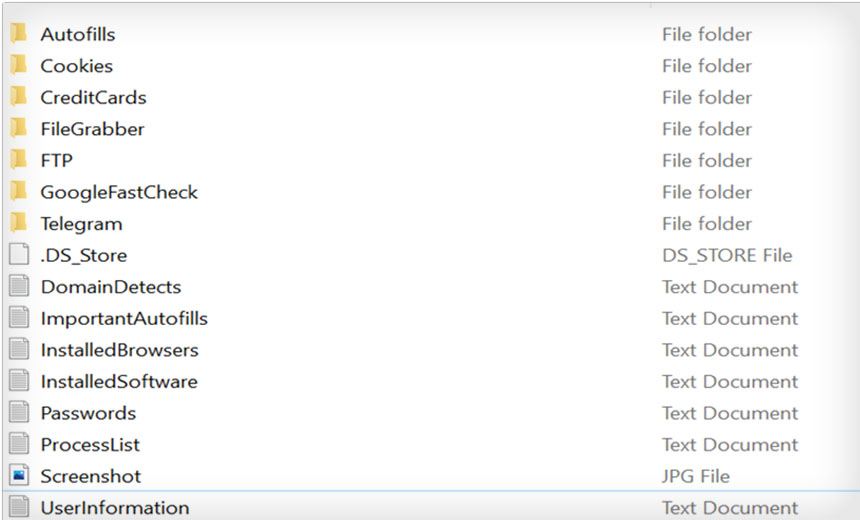
A variety of underground markets exist to help malware-wielding criminals monetize their attacks, including via log marketplaces such as Genesis, Russian Market and 2easy, which offer for sale batches of data that can be used to emulate a victim, whether it's a consumer, an enterprise IT administrator or anyone in between.
See Also: Take Inventory of Your Medical Device Security Risks
Such marketplaces are a reminder that extensive information continues to be harvested by information-stealing malware, such as RedLine and AZORult.
These infostealers often get distributed via booby-trapped emails and websites and after infecting a PC, they can exfiltrate many different types of data, including passwords.
Experts say the most valuable data, such as cryptocurrency wallets and stored payment card data, often gets siphoned off first by attackers. Sometimes, they use this information themselves, for example, to try and steal all of the bitcoins from a victim's cryptocurrency wallet. In other cases, however, attackers may be wielding information-stealing malware they have obtained from a service provider.
Depending on the terms and conditions, some experts say, service providers sometimes reserve the choicest morsels obtained via their malware for themselves.
Multiple sellers on the 2easy market, for example, appear to have already "worked out" certain types of data, meaning it's been excised from logs before they're offered for sale, according to a report from Israeli cybersecurity firm Kela. In many cases, this technique appears to center on cryptocurrency wallets, which attackers can target to siphon away all the funds they store, the report says. But in other cases, it might be part of the terms and conditions being offered by an information-stealing malware service being used by the seller.
The rest, however, often gets put up for sale on log marketplaces.
Log markets specialize in selling bots. In common cybersecurity parlance, a bot typically refers to an individual malware-infected PC, aka zombie, which is being remotely controlled as part of a botnet. But in the market-speak pioneered by Genesis, which debuted in November 2017, "unlike the generally accepted use of the term bots, to mean the automated functioning of a task, the bots for sale on the Genesis Market instead represent the output of those tasks," London-based bot-battling firm Netacea says in a report.
Each bot represents the takings from a single PC: personal information, browser cookies, saved passwords as well as so-called fingerprints, which are "the unique identifiers left behind by browsers and devices when visiting websites - for example, browser version, screen resolution, IP address or operating system," Netacea says.
Emulating Victims
Each bot can be used by a buyer to emulate the victim from whom the data was stolen - for example, to log into their online accounts.
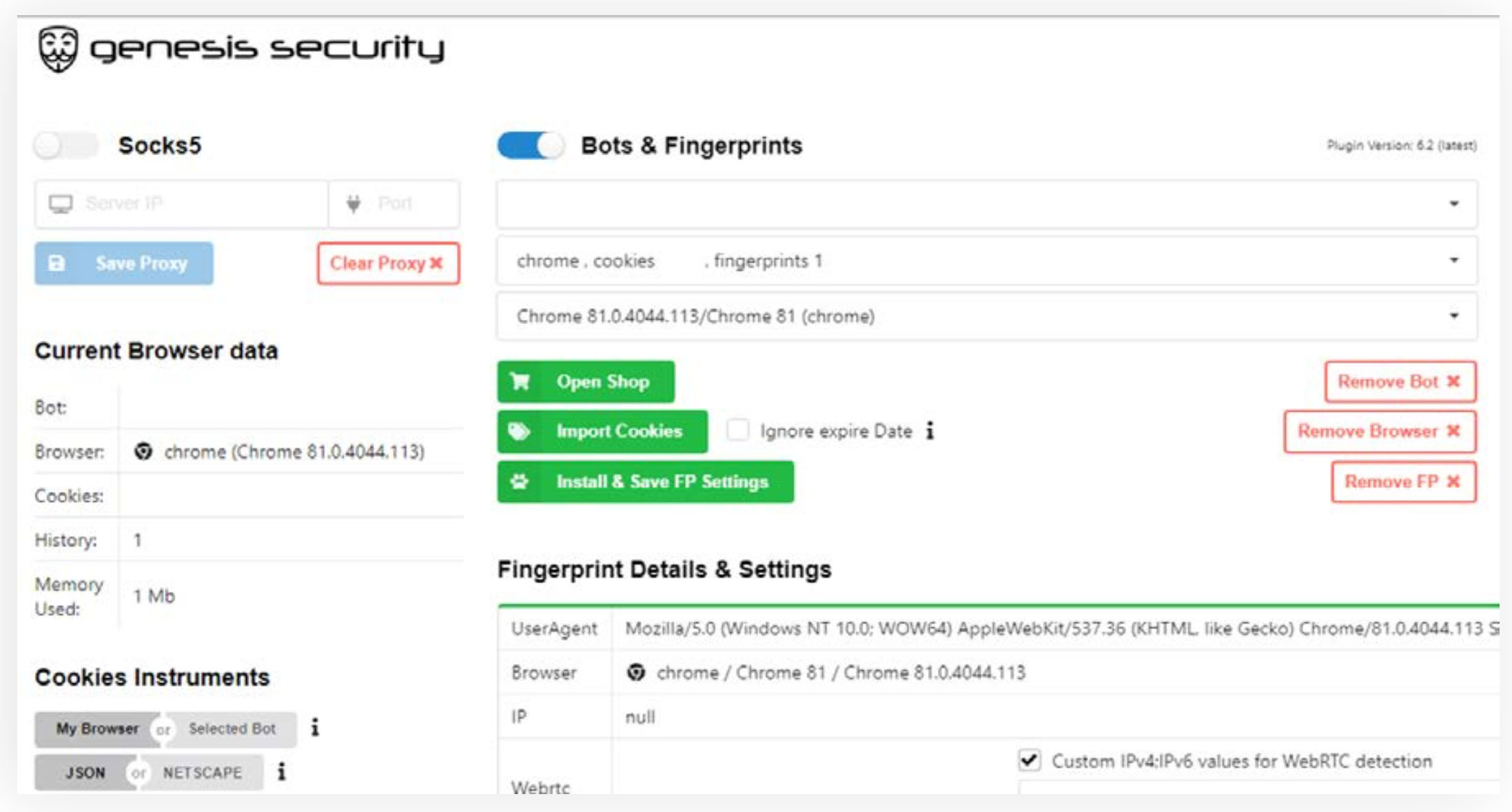
For Genesis users, for example, buyers are offered two different browser-based approaches for putting a log to use, Netacea says. One option is "a Chromium-based browser plug-in, Genesis Security," that can be used with a buyer's own browser. The other option is a "de-Googled" version of Chromium, maintained by Genesis developers, which includes the Genesis Security plug-in preloaded.
Either approach can help buyers masquerade as the victim of the information-stealing malware and "use saved logins to access their accounts and - where login cookies exist continue a victim's session, all without any access to the original device," Netacea says.
For-sale logs can contain information of a personal as well as a professional nature. Kela says that these saved credentials might include access to enterprise systems, such as a Pulse Secure VPN, Cisco ASA WebVPN and more, offered for sale on 2easy.
Options Abound
In April 2018, researchers at threat intelligence firm Digital Shadows reported that Genesis Market had 1,500 bots for sale. By 2019, that number had risen to 100,000 and by March 2021, it had reached 350,000, Netacea says.
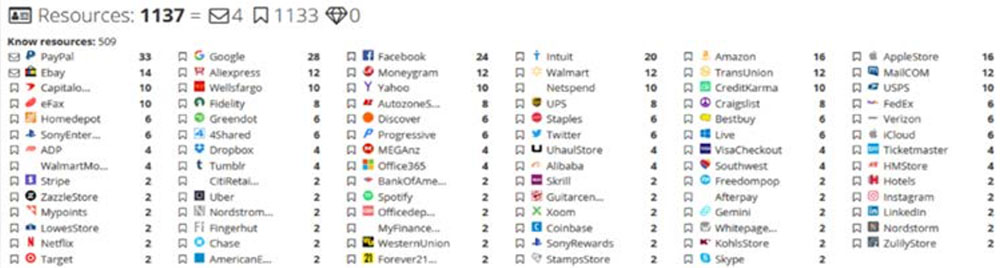
Other log market options are available. Kela says Genesis occupies the upper end of the log market spectrum, with its bots retailing for $5 to $25 each, on average, versus $10 to $15 for Russian Market and just $5 at 2easy, which is a newer player.
New Player: 2easy
Underground chatter is that 2easy is a reputable market, meaning the data it sells appears to have been legitimately stolen and includes buyer protection, such as the ability to request a refund if it looks like the log data is being resold, or if it doesn't contain what was promised - for example, if it's missing listed "passwords or cookies," Kela says.
As of December 2021, 18 different sellers were collectively advertising logs from about 600,000 different systems on 2easy, up from the 28,000 bot-harvested logs it was offering for sale in July 2020, Kela says. It says that just four sellers appear to account for nearly 94% of all listings and that their information-stealing Trojan of choice is most often RedLine malware, followed by AZORult, Vidar and Raccoon, among other malicious software.
After purchasing a bot via 2easy, "a buyer receives an archived - zipped - file containing folders and files with stolen data and information about the bot: saved credentials and credit cards, a list of installed browsers and software, a list of processes, user information, some files, and more," Kela says. "The type of data the buyer gets depends on the capabilities of infostealers used; different malware strains may be focused on stealing various types of data."
Enterprise Risk
What risk does this pose for enterprise security teams?
One challenge is that stolen data can be mined to find credentials that will allow an attacker to gain initial access to a corporate network.
For example, Kela points to the attack on Electronic Arts that came to light in June 2021. "The attack reportedly began with hackers who purchased stolen cookies sold online for just $10 and continued with hackers using those credentials to gain access to a Slack channel used by EA," Kela says. "Once in the Slack channel, those hackers successfully tricked one of EA's employees to provide a multifactor authentication token, which enabled them to steal multiple source codes for EA games."
Hence when properly and successfully put to work, spending around $10 to buy a bot filled with stolen enterprise data offers the potential for a massive return on investment for the criminally inclined.






















