Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware
WannaCry's Ransom Note: Great Chinese, Not-So-Hot Korean
Linguistic Analysis Suggests Native Chinese Speaker Wrote Ransom Note
The identity of the individual or group behind the massive WannaCry ransomware campaign remains unclear. But whoever wrote the ransom notes appears to have been fluent in Chinese, pretty good at written English, but lacking Korean language skills, according to a new linguistic analysis published by security firm Flashpoint.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
Three Flashpoint researchers who have extensive Chinese language and cultural experience analyzed the 28 versions of the ransom note included with the WannaCry ransomware, which on May 12 began infecting tens of thousands of endpoints. The ransomware was paired with a worm designed to target the EternalBlue exploit written by the Equation Group - and leaked by the Shadow Brokers - which targeted an SMB flaw in Windows (see WannaCry Outbreak: Microsoft Issues Emergency XP Patch).
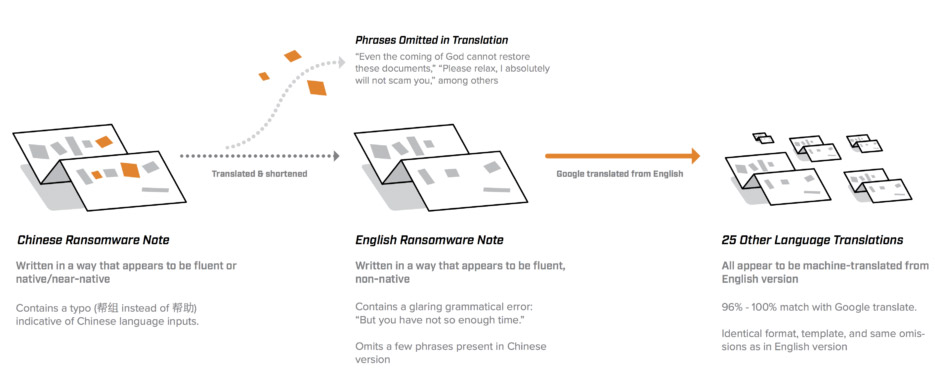
According to Flashpoint's analysis, the original ransom note appears to have been written in Chinese, rewritten in English and then translated en masse using Google's free translation service.
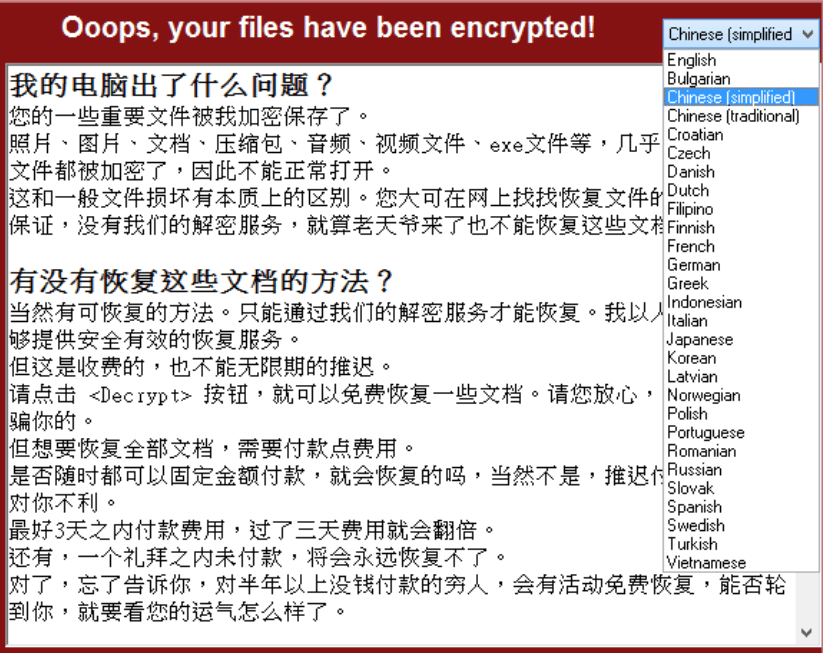
Where the Chinese ransom note is concerned, "a number of unique characteristics in the note indicate it was written by a fluent Chinese speaker," Flashpoint's researchers say. For example, the note includes a typo that most likely came from someone writing in the Chinese language, rather than using an automated translation service.
"More generally, the note makes use of proper grammar, punctuation, syntax and character choice, indicating the writer was likely fluent or at least native ... in Chinese, as the language used is consistent with that of Southern China, Hong Kong, Taiwan, or Singapore," the researchers say. "There is, however, at least one minor grammatical error which may be explained by autocomplete, or a copy-editing error."
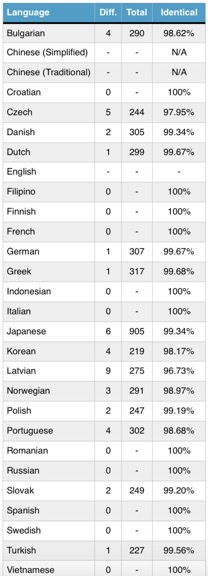
Compared with the other ransom notes, the Chinese version is lengthier and includes much more substance. Flashpoint says the Chinese version appears to have been written first.
After that, the researchers say it appears the notes were rewritten in English by someone "familiar with the English language, though not native."
Subsequently, they say, it appears that Google Translate was used to create a version of the ransom note in the other languages.
WannaCry Ransom Note Genesis
Attribution: Stay Skeptical
What's the takeaway from Flashpoint's analysis?
A flurry of media reports in recent days have suggested, wrongly, that there is overwhelming evidence that WannaCry was launched by the Lazarus group. That hacking team - tied to the hack of Sony Pictures Entertainment and the $81 million heist from Bangladesh Bank via SWIFT interbank messages - has been previously connected with the Pyongyang-based regime that runs the Democratic People's Republic of Korea.
But security experts say there is no conclusive evidence tying WannaCry to either Lazarus or North Korea. Rather, many say the campaign appears to have been launched by amateurs - potentially script kiddies who cobbled together code and created a worm that quickly got out of control (see WannaCry 'Link' to North Korea Remains Tenuous).
Attribution remains the provenance of intelligence agencies, and conclusions about who hacked whom are of greatest use in the diplomatic sphere. For the vast majority of everyone else, security experts say it's better to focus on keeping systems patched and updated, and watching for signs of attack, than to worry about whether it's a nation state, cybercriminal gang or script kiddies gunning for you.
Of course, it can be fun to try to figure out who's lobbing attacks, and Flashpoint's research now throws some potential new clues into the mix. For example, the original WannaCry ransom note may have been written by an individual - or group - for whom Chinese is their native tongue. But as the Flashpoint researchers caution: "This alone is not enough to determine the nationality of the author(s)."
Indeed, linguistic analysis alone does not make for conclusive attribution (see Expert: Sony Hackers Sound Russian).
Furthermore, today's cybercrime ecosystem has become very diversified. Advanced supply chains, which cross countries, exist to provide attackers with anything they might desire: attack code, already infected endpoints, extensive personal details on potential victims, money laundering services and potentially even ransom notes, written to order.
Double Bluff?
Another takeaway from the linguistic analysis, however, is that whoever is behind WannaCry may have thrown in what Flashpoint describes as "subtle" Chinese language clues to serve as a false flag - a way to throw researchers off the trail.
"It's worth noting that they say the Korean was [almost] the worst translation of all," Alan Woodward, a computer science professor at the University of Surrey, tells me. "Of course, it might be a double bluff."
North Korean hackers are long known to have worked out of China, including from Shenyang, a Chinese-North Korean cultural hub located just 235 miles from the North Korean border. Kim Heung-kwang, a former Pyongyang computer science professor who escaped from the country in 2004, told CNN in 2015 that the nation's "Bureau 121" hacking team was based in Shenyang and was composed, at least in part, of former computer science graduates from a five-year program at Pyongyang's University of Automation.
"By day, they worked regular jobs. But the rest of the time, they were acting on orders from Pyongyang," Kim told CNN.
Beware of Too Many Assumptions
But attempting to sketch scenarios in which script kiddies might be tied to the Lazarus group and recruited native Chinese speakers to help launch a poorly thought out global ransomware campaign - perhaps without the backing of Pyongyang - quickly starts to become "tenuous," says Woodward, who's also a cybersecurity adviser to the EU law enforcement intelligence agency, Europol.
"When you start to have to make so many assumptions to support your hypothesis, it starts to look increasingly unlikely," he says.












