Active Defense & Deception , Black Hat , Cybercrime
Visual Journal: Black Hat Europe 2018
London Docklands Plays Host to 17th Annual Information Security Conference
The recent Black Hat Europe conference in London touched on topics ranging from combating "deep fake" videos and information security career challenges to hands-on lock-picking tutorials and the dearth of researchers submitting proposed briefings centered on deception technology (see: 14 Hot Sessions at Black Hat Europe 2018).
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
Here are some of the many highlights from last month's Black Hat Europe 2018:
Spin-off Event

Black Hat Europe was launched by founder Jeff Moss in 2001 as a sister conference to the annual Black Hat conference, which he launched in 1997. Black Hat USA continues to run in Las Vegas every summer.
ExCeL London

This was the 17th annual Black Hat Europe, which again returned to London, following the conference having decamped from Amsterdam in 2016, seeking more space. This year's conference was held at the sprawling ExCeL convention center.
Room to Grow

The ExCeL convention center in East London offers ample space, including room to grow, over its 100-acre campus.
Destination: Docklands

ExCeL London is located on a 100-acre site on the northern quay of the Royal Victoria Dock in London Docklands, situated between Canary Wharf and London City Airport. Formerly part of the Port of London - at one time, the world's biggest port - the area has been the focus of extensive redevelopment and is well-served by the Docklands Light Railway, an automated, light metro system.
Nearly 3,000 Attendees

At this year's Black Hat Europe, nearly 3,000 attendees split their time between 40 sessions delivered by a total of 100 speakers and researchers, including sessions in the business hall.
Moss opened this year's Black Hat Europe by taking to the stage to deliver his annual opening comments. He noted that the ever-expanding quantity of attendees this year included visitors from 106 countries. He singled out 26 countries from which a single representative was attending, including America Samoa and Reunion, although as he noted, the island is technically an overseas department of France.
"Feel free to whoop when I say your country," he said.
Business Hall

The business hall played host to 67 businesses, associations and other organizations, ranging from Accenture and Agari to Yubico and ZeroFox. It also included places for grabbing coffee, purchasing official Black Hat merchandise - including hoodies for any aspiring hackers on your holiday wish lists - or attending Arsenal tool demonstrations and vendors' sessions in the various business hall theaters.
The many briefings touched on everything from steganographic disk encryption and Microsoft browser security to how to exterminate "deep fakes" as well as abuse Windows 10 security questions.
Estonia's Cyberattack Wake-Up Call

Black Hat Europe 2018 opened with a call to action from Marina Kaljurand, chair of the Global Commission on the Stability of Cyberspace.
In her keynote speech, the Estonian politician reflected that where cybersecurity is concerned, Estonia is lucky. That's because it suffered a massive, three-week distributed denial-of-service attack in 2007 that disrupted its banking sector as well as some government websites (see: Black Hat Europe: The Power of Attribution).

While the attacks were primitive by today's standards, "they were humiliating," said Kaljurand, who was Estonia's foreign minister at the time.
The attacks also served as a cybersecurity wake-up call for Estonia's leadership and helped inform how the country would refine its pioneering and lauded e-Estonia program, which makes 99 percent of government services available digitally.
"We were lucky to have the attacks of 2007 to consider and reconsider how to continue with our e-Estonia," she said.
Unusually, Estonia can also count on its own Cyber Defense Unit, which consists of numerous citizens who don't hold government jobs and who contribute their time on weekends. "They're doing it voluntarily; they're doing it out of patriotism; they're doing it for free," she said. While that model wouldn't work for every nation, for a country as small as Estonia, she said it serves its needs well.
See the Bigger Picture

In a side interview at the conference, founder Jeff Moss, reflecting on Kaljurand's opening speech, told me that national pride and patriotism should never be overlooked in a geopolitical context, and that hacking is often only one piece of a much larger picture.
To pick just one example, he said the attacks against Estonia - roundly attributed to Russia - appeared to be in response to Estonia's plans to relocate a controversial, Soviet-built WWII statue as well as war graves.
Facial Recognition: We Don't Need No Badges

Beware the front row, at least if you're attending a briefing delivered by Cesar Jimenez and Fran Gomez of Devo.
The pair demonstrated a live tool they built to see who they can automatically recognize, based on who's in their LinkedIn profiles. They accomplished that by scanning audience members to see who their software could positively match with one of their LinkedIn contacts, based only on the contact's LinkedIn profile picture.

"The aim is to know who's in my LinkedIn contacts; it's better than scanning your badges," Gomez said.
The point underlying their demonstration is that it's easier than ever to subject people to facial recognition technology.
Such technology can be used for potentially good purposes. But it can also be used for purposes that might not be in an individual's best interests. For example, China is developing a controversial social credit system, which by 2020 aims to score each citizen's contribution to society in a variety of different areas.
"So, we need some defense, because this is no good for us," Jimenez said.
The researchers ran through a short list of tactics and technologies designed to fool facial recognition, including baseball caps with built-in infrared lamps designed to blind cameras, as well as using face-hiding haircuts.
"Or you can just wear a horse mask," Jimenez said. "It's dangerous, but effective."
Self-Concealing Steganography
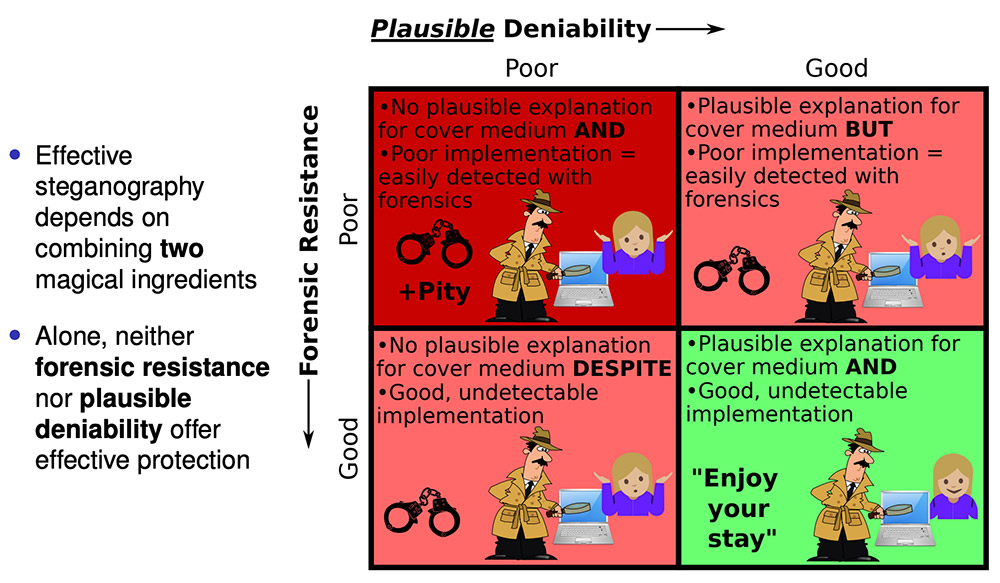
What if you could hide whole operating systems on a hard drive? That steganographic - hiding data in plain site - goal was the focus of a briefing by Dominic Schaub, a researcher at tthe Canadian firm Discrete Integration, which has been building a suite of tools designed to bootstrap a hidden operating system, which remains hidden in the free space on a disk that regularly gets overwritten.
Schaub has designed a technique that uses error correction to restore the "corrected" data and feed it into a run-time environment (see: The Rise of Self-Concealing Steganography).
Schaub says work is continuing to finish developing the tool set. "We just wrapped up late-stage testing and are in the process of releasing Mirage, our first commercial product based on the steganographic technology," he told me.
How to Battle 'Deep Fakes'

Deep fake - or "deepfake" - videos are increasingly being used to harass or otherwise target individuals. Such videos are easy to create using freely available tools; they were initially used to swap victims' faces onto porn stars' bodies. But the technology can also be used to make political figures say things they never said or otherwise try to compromise people's reputations.
"What does it take to make a deep fake? All it takes is a gaming laptop, an internet connection, some passion, some patience, of course, and maybe some rudimentary knowledge of neural networks," said Vijay Thaware, a security researcher at Symantec, during the briefing.
Thankfully, there are a variety of tactics that can be employed to spot deep fakes, he said.
Thaware and his fellow Symantec researcher, Niranjan Agnihotri, have been developing tools that they hope social media networks will use to screen videos before allowing them to be uploaded (see: Face Off: Researchers Battle AI-Generated Deep Fake Videos).
Free Lock-Picking Tutorials

Ever wanted to learn how to pick locks? Experts from Ireland were on hand from IBM X-Force at the IBM Security booth, including ethical hacker Martin Mitchell. He regularly runs lock-picking workshops at the annual Irish Reporting and Information Security Service's IRISSCON Cyber Crime Conference in Dublin (see: 13 Scenes from an Irish Cybercrime Conference).
Mitchell's array of available locks includes "love locks" that he removed from Dublin's Ha'penny Bridge, with the blessing of the city council, because their weight can damage the structure.
MIA: Deception Tech

While the keynote speech opens the briefings, Black Hat closes with a "locknote," led by Moss, who's joined by members of the Black Hat Review Board. Together with Antonios Atlasis of the European Space Agency, Daniel Cuthbert of Banco Santander, and Veronica Valero of Cisco Systems, Moss touched on a variety of topics, including some trends the review board sees, based on its reviews of more than 1,000 submissions every year.
One interesting omission, Moss said, was the apparent lack of use of deception technology. "I never heard one speaker say: 'And then I checked the canary or, and then I [reviewed] the deception tech," he said. "Who here uses deception technology?"
Just one hand among the hundreds of locknote attendees appeared to get raised.
"Who here runs canaries?" he asked, referring to a honeypot designed to detect network intruders. Four hands were raised.
Perhaps the first rule of using deception technology is to never talk about deception technology?
Cuthbert, however, said deception technology poses many problems. "As an ex-attacker, if you breach the network, you go for the juicy network," he said.
In addition, from an administration standpoint, "the moment you throw deception tech on there, you've now got four networks," he said. "It's an overhead nightmare."
Negotiate Time for Learning

The locknote discussion touched on information security career challenges - and progression.
"Ten years ago, we were joining the industry in a different time; we were not so pressured with time; we were more relaxed, I could take a day to learn something," said Cisco's Valero. "Now, companies want you to be productive in three months, and you're just out of school."
The best solution, she said, is to find time, for example, by demanding one day per week to master new technologies or practices. "Negotiate," she said. "It's your career."
We Want Your Good Defense

From a research standpoint, one underserved area is how to craft better defenses. The conference review board members said they're keen to see more Black Hat submissions about research into top-notch defensive techniques.
"We want good defensive talks, because they're harder," Cuthbert said. "Look at HackingTeam; they were very good at breaking stuff and they got popped really hard."
Sounding a hopeful note, he suggested that defensive techniques are the new stunt hacking. "The days of popping xcalc on an internet-connected dildo are well and truly behind us," he said.
All photographs by Mathew Schwartz












