Fraud Management & Cybercrime , Fraud Risk Management , Malware as-a-Service
Ransomware Attackers May Lurk for Months, FBI Warns
LockerGoga and MegaCortex Gangs May First Ransack Networks for Sensitive Data
Warning: Attackers wielding LockerGoga and MegaCortex ransomware have been hitting large corporate networks, sometimes lingering for months before deploying crypto-locking malware.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
That's according to a recent FBI flash alert, marked "TLP:AMBER" - restricted to receiving organizations. It was issued to certain U.S. businesses by the FBI, Bleeping Computer reports.
"Since January 2019, LockerGoga ransomware has targeted large corporations and organizations in the United States, United Kingdom, France, Norway, and the Netherlands," the FBI's alert reads, according to Bleeping Computer, which obtained a copy. "The MegaCortex ransomware, first identified in May 2019, exhibits Indicators of Compromise (IOCs), command and control (C2) infrastructure, and targeting similar to LockerGoga."
Bleeping Computer reports the alert states: "The actors behind LockerGoga and MegaCortex will gain a foothold on a corporate network using exploits, phishing attacks, SQL injections and stolen login credentials." It also notes that attackers often wield Cobalt Strike penetration testing tools, including Cobalt beacons, to breach sites and gain remote access.
The FBI flash alert confirms what ransomware experts have been telling me for the past couple of years: That a crypto-locking malware infection is often just the final, very noisy end stage of an attack that may have already persisted for weeks or months.
First, attackers often access sites using remote desktop protocol credentials. These can be brute-forced by attackers, or purchased on cybercrime sites - located on the darknet or otherwise - often for as little as $5 per site (see: Ransomware Gangs' Not-So-Secret Attack Vector: RDP Exploits).
Next, more advanced attackers will carefully map the target network, looking for any sensitive intellectual property, customer details or payment card information that they can exfiltrate and sell on cybercrime markets.
As the final stage of their attack, criminals may leave ransomware to try and earn a bit more criminal profit for their hacking efforts.
Or in the case of nation-state hacking operations, attackers may deploy ransomware to make the intrusion look like a criminal undertaking, while helpfully wiping their digital forensic tracks, as Jake Williams, head of cybersecurity consultancy Rendition Infosec, told me at this month's Black Hat Europe conference in London (see: Ransomware 2.0: Cybercrime Gangs Apply APT-Style Tactics).
FBI Flash Alerts: Call to Action
FBI flash alerts that touch on cybersecurity matters generally do not include previously unpublished or confidential information. Rather, they're a distillation of attack facts and essential defenses meant to spur organizations to take action, even if, arguably, their cybersecurity teams should already have done so (see: Ransomware School: Learn Lessons From How Others Fail).
Indeed, information security experts regularly tell me that if the FBI, U.S. National Security Agency or Britain's National Cyber Security Center - part of intelligence agency GCHQ - issue an alert, it's because they're seeing a large number of organizations continue to fall victim to preventable attacks, even if the details of these attacks are already public and widely known. In other words, the FBI is telling potential victims: Get your act together (see: Turla Teardown: Why Attribute Nation-State Attacks?).
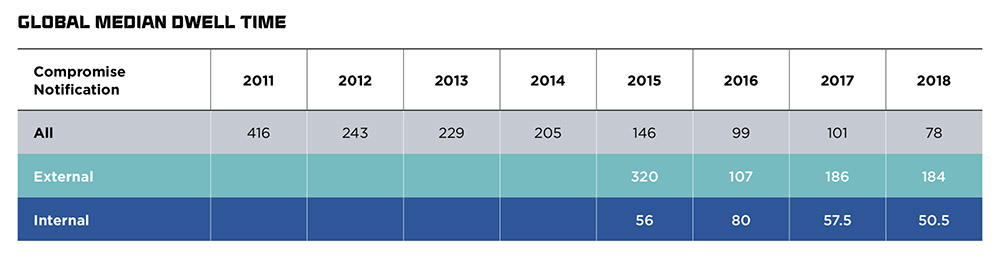
Furthermore, ransomware-wielding attackers potentially are not the only types of hackers camping out in an organization's network, undetected for long periods of time. According to FireEye's Mandiant, when an organization discovers it's been breached - thanks to a heads-up from a third party - the intrusion has already persisted for an average of 184 days.
Ransomware Defense: Security Basics Still Apply
To defend against hackers wielding ransomware, the basics remain the same. For starters, organizations need to ensure they have up-to-date backups, stored offline. That way, if they get hit, they can wipe all systems and restore from backups. Victims still face the threat of downtime and lost business, but to cover those potential losses, many have been investigating cyber insurance policies (see: Norsk Hydro Breach: Update on Insurance Coverage).

Unfortunately, as the seemingly unending spate of ransomware attacks demonstrates, not enough organizations - municipalities, healthcare providers, large businesses and others - have been maintaining the right defenses (see: Ransomware Risk Management: 11 Essential Steps).
Since appearing in January, for example, MegaCortex has been tied to takedowns of big firms, including online cloud hosting provider iNSYNQ in July. After accounting software giant Wolters Kluwer got hit by malware in May, employee chatter on a bulletin board said MegaCortex was the culprit. While that has yet to be officially confirmed, Sophos reported seeing a spike in MegaCortex attacks that month (see: Malware Knocks Out Accounting Software Giant Wolters Kluwer).
In August, consultancy Accenture's iDefense reported seeing a a new variant of MegaCortex hitting victims, with attackers demanding up to $5.8 million in ransom payoffs for the promise of a decryption tool.
Meanwhile, LockerGoga hit aluminum giant Norsk Hydro in March. Since then, it's been tied to many more infections (see: LockerGoga Ransomware Suspected in Two More Attacks).
'Remain Vigilant'
Experts say ransomware remains inexpensive to procure - or to rent, for example, via the Sodinokibi ransomware-as-a-service operation - and automation enables attackers to hit many potential victims at once.
"As with most automated, active attacks, organizations need to remain vigilant," says Andrew Brandt, a security researcher with Sophos. "Tighten up password policies to include multifactor authentication for - at least - admin accounts; put RDP servers behind a VPN; survey your network for vulnerable services exposed to the internet; patch everything; and shut down anything that doesn't need to be poking its nose through the firewall."
Nights and weekends remain prime times for attackers to strike (see: Hackers Love to Strike on Saturday). "Before you log out for an extended break, it would be wise to shut down your workstation, and maybe even pull out the power cord," Brandt says.
As the FBI's alert makes clear, all organizations can become crypto-locking malware victims, so they must put the right defenses in place. Otherwise they can potentially look forward to attackers - of all stripes - camping out in their network for months, leaving ransomware as a final coup de grâce when they're done.











